This is a vulnerable linux box focused on web application testing along with showing the importance of enumeration. There are three users you needs to compromise to read the root flag.Enumeration
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
10000/tcp open snet-sensor-mgmt syn-ack ttl 64We have 3 ports open, let’s start with port 80 as usual:
Nothing hugely useful. I ran a nmap scan against the other ports and saw that port 10000 was also a web service:
10000/tcp open http syn-ack ttl 64 MiniServ 1.910 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
|_http-favicon: Unknown favicon MD5: 6594483717A9D1D13CF12F31EBFDB483
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS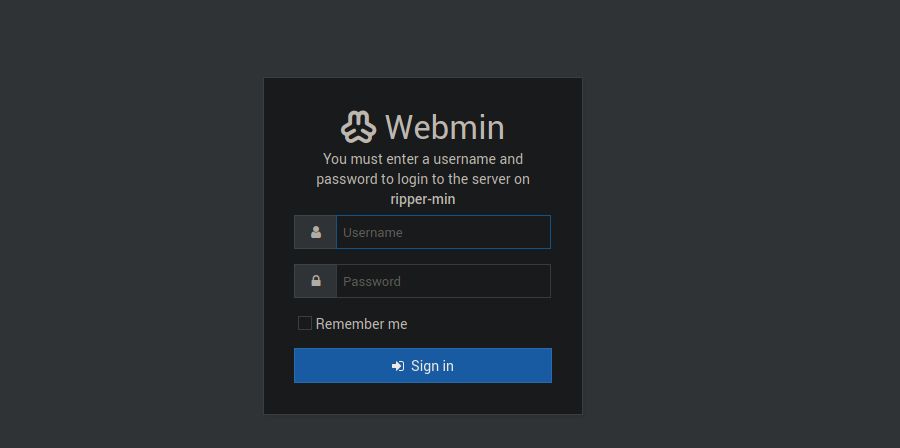
Foothold
This is somewhat of a dead end since we don’t have a login. We’ll try bruteforcing directories on the default site and see if we find anything more useful. We end up finding a rips directory. RIPs is a source code analysis web-app:
We’re able to grab the source code out of different directories. Let’s try grab the source code for the two web apps:
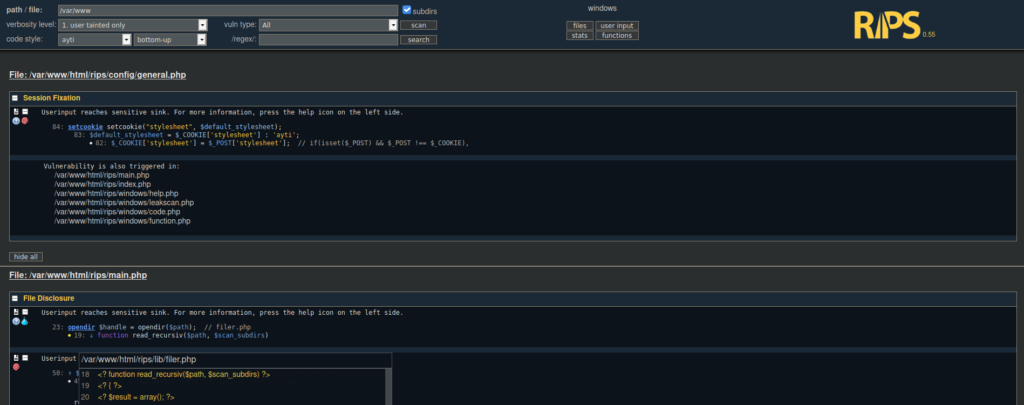
If we click on files in the top right, we see there’s a file called secret.php, it contains some credentials:
<?
<?
<? echo "user name: ripper"
<? echo "pass: Gamespeopleplay"
<?
<? User own
Using the creds we have , we can try reuse them over at webmin but this doesn’t get us anywhere. We can try SSH instead:
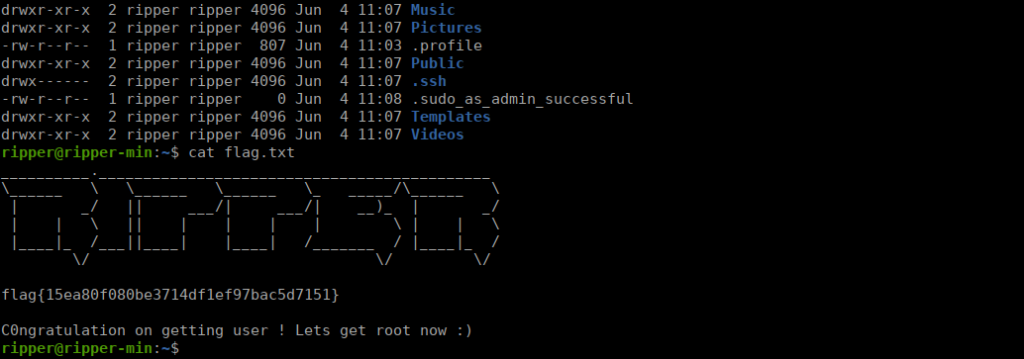
Easy user own, let’s go straight to root!
Root own
Ripper isn’t the only user on this box, cubes could be a potential pivot point. Let’s start enumerating. We have a file called secret.file in the /mnt directory:
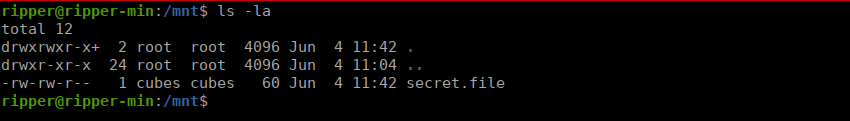
Using the password in the file, we can pivot over to cubes. Cubes has access to the webmin directory. We can look through the log files and see an admin password:
tokiohotel
Using the credentials, we can use a metasploit exploit to get root access:
exploit/linux/http/webmin_packageup_rceor we can use the built in terminal to access a shell as root:







