In this challenge, you are asked to solve a simple reversing solution. Download and analyze the binary to discover the password.
There may be anti-reversing measures in place!Bypassing reversing measures
An easy reversing challenge with anti-reversing measures. Sounds fun. We can go through some basic techniques such as the one linked below:
https://pentester.blog/?p=247If we change the binary in such a way that it doesn’t break, such as changing a file header to make our machine treat it as a 32 bit binary instead of 64 bit, we can bypass some measures in place:
Reversing
We save our changes and pop the binary open in ghidra (feel free to use anything you like):
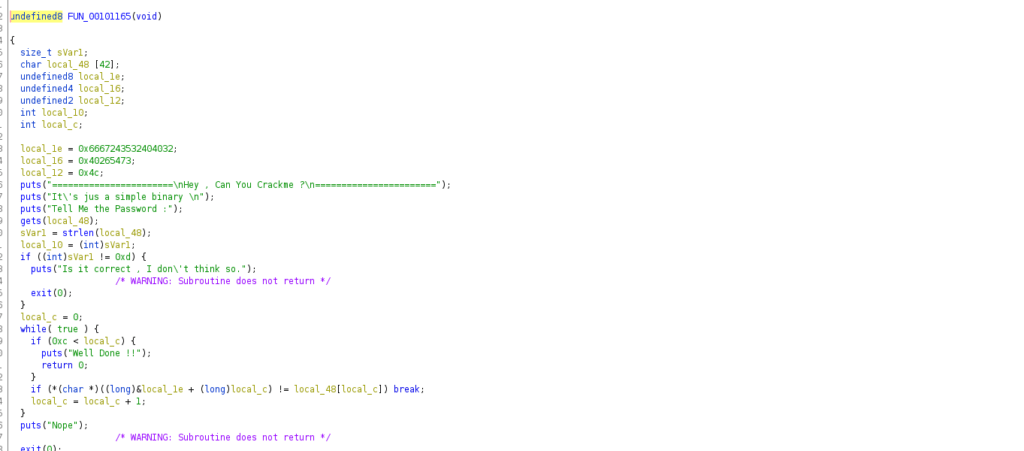
We can clearly see what happens when we give the correct password, as well as the checks that are being made. We see some variables that we can decode to get our password:
local_1e = 0x6667243532404032;
local_16 = 0x40265473;
local_12 = 0x4c;Challenge own
Using our command line, we can decode each string and put them together:
echo 0x6667243532404032 | xxd -r -p
echo 0x40265473 | xxd -r -p
echo 0x4c | xxd -r -pFinally, we reverse each string (in order) and get our password:
2@@25$gfsT&@LWe can test this over at our binary:

Note: Submit the flag as THM{2@@25$gfsT&@L}






